Masking the web server software in your http header/http server banner (server header obfuscation) is an important layer of security you might want to implement since it can be accomplished so easily on a Netscaler. It’s a layer of security you can add to prevent someone from telling what kind of web server you are running, such as Microsoft IIS or Apache, though it is still quite possible to figure out depending on your environment and application so don’t rely on it too much. The thought is an attacker scans for certain versions of a web server that have known vulnerabilities and begins running attacks for that specific web server software to see if those vulnerabilities have been patched or not. They can do this programmatically so changing the header to say something else is a layer of security that can prevent them from easily figuring out what your web environment infrastructure is like.
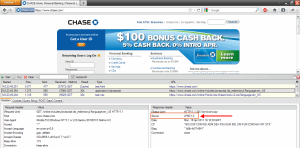
You will notice that Chase.com uses “JPMC1.0”:
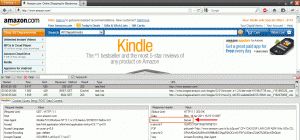
Amazon.com uses just “Server”:
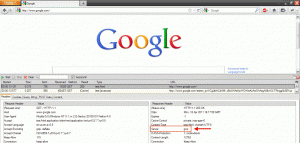
Google.com uses “gws”:
This can be done very easily using rewrite policies on the Netscaler. Catherine Hampton wrote a great article over at the Citrix Developer Network on how to do this:
http://community.citrix.com/display/ns/Using+Rewrite+to+Improve+Web+Server+Security
And if you want to read more about web server fingerprinting, check Net-square’s website and their httprint tool:
http://www.net-square.com/httprint.html
Saumil Shah at Net-square wrote an excellent and very thorough article on HTTP fingerprinting here:
http://www.net-square.com/httprint_paper.html
Jason Samuel is a visionary product leader and trusted advisor with a proven track record of shaping strategy and driving technology innovation. With extensive expertise in enterprise end-user computing, security, cloud, automation, and virtualization technologies, Jason has become a globally recognized authority in the IT industry. His career spans consulting for hundreds of Fortune 500 enterprises across diverse business sectors worldwide, delivering cutting-edge digital solutions from Citrix, Microsoft, VMware, Amazon, Google, and NVIDIA that seamlessly balance security with exceptional user experiences.
Jason’s leadership is amplified by his dedication to knowledge-sharing as an author, speaker, podcaster, and mentor within the global IT and technology community. Recognized with numerous prestigious awards, Jason’s contributions underscore his commitment to advancing technology and empowering organizations to achieve transformative results. Follow him on LinkedIn.
Disclaimer: Views expressed here are his own and do not reflect the views of his employer, past or present, or any organizations he is affiliated with. Content is for informational or personal purposes only.





Thanks a lot for this article!
Hi Jason, I read your blogs and its quite good and eye opening for me. I need an input from…
I'm with Richard Powell and Andreas Mariotti. Things work if I do it the USB redirection way, but not with…
We see this behaviour with 2203 CU2 VDAs and while being happy, that there is at leasy an workaround without…
Saved my butt without playing around over dozens attempts to get that certificate installed! Thank you! <3 Chris