
I have for the longest time wanted to give my WiFi network an overhaul. After months of research I decided to move forward with Ubiquiti Networks (UBNT) UniFi line of WiFi products to help build my new network. My previous WiFi equipment was fast, had good coverage, was easy to segment and manage, but one thing was lacking…easy visibility. I felt like the metrics I was really interested in were hard to get out the devices themselves. I test the heck out of consumer IoT, enterprise IoT, and industrial IoT (IIoT) gear and I need to be able to see what kind of traffic is produced. I had to resort to 3rd party tools to gather the info I needed and it just felt overly cumbersome. There is some other enterprise level gear that I have used in my career that can do exactly what I wanted but the price is just way out there to justify for a home network. Some of the lower priced appliances that would have worked have annual subscription fees attached. The UBNT gear is reasonably priced and doesn’t have any subscription fees. But price alone wasn’t the reason why I chose UBNT UniFi.
Why I ultimately decided on UniFi gear
I looked into newer consumer mesh WiFi technologies like eero, Google Wifi
, and even Ubiquiti Networks AmpliFi
but in the end decided mesh WiFi was not for me. I have always been a proponent of wired backhaul. Switching to mesh or using wireless backhaul decreases available bandwidth. I already had the CAT5e runs to continue with a wired backhaul infrastructure to all APs so I decided to stick with this approach for the best possible WiFi performance. A lot of people look into mesh networks for better roaming but you can achieve the same type of experience if you tune the minimum RSSI on your APs correctly. These APs do have seamless roaming (Zero-Handoff) by the way but it has some additional requirements. I also found exploring my options that the UniFi Controller software gave me all the insight into my WiFi network (and much more) over these other platforms plus the price of these platforms were all pretty close to the same range. If you’re the average consumer, I think you would be better off with those actually and I would whole heartedly recommend them to my non-IT family and friends. If you are the type of person that likes to run a solid network but also tinker and squeeze the last bit of performance out of everything, then I would not suggest these platforms and tell you to really take a close look at UniFi. As I add more UniFi equipment in the future beyond WiFi gear I will be able to use UniFi Controller for central management and analytics. Kind of like NetScaler MAS for you Citrix NetScaler fans 🙂
I bought a Ubiquiti Unifi Cloud Key which has the UniFi Controller built-in. This is used for hybrid cloud device management. You can also choose to install it on your own systems or even a Raspberry Pi but for the under $80 price, I’d rather just have the solid hardened device and not have to worry about updates since it can update itself. Plus it can do PoE so just plug it into a PoE switch and forget about it. I’ll go into more on the Cloud Key later.
The next step was choosing the proper Access Points (APs). The UniFi line has quite a bit as you can see here:
https://www.ubnt.com/products/#unifi
I opted for 2 of the Ubiquiti Networks Unifi AC PRO APs (UAP-AC-PRO-US) since they can do up to 1300 Mbps which is similar performance to what my previous gear could do. After a few weeks of testing I decided this was definitely the platform for me and purchased a 3rd one. The only thing I wish I had done is purchase 2 of the UniFi AP In-Wall AC versions that can do 5 Ghz when they were available for beta. Right now you can only purchase the 2.4 Ghz only versions of those. When the AC versions do become available for purchase I plan on adding those to the mix. It’s not that the 3 AC Pro APs don’t have good coverage, they are great actually. It’s just that some of my 2×2 MIMO (2 antennae) or 3×3 MIMO (3 antennae) devices use the 5 Ghz band and to really get the advertised speeds I have to crank up the 5 GHz radios to use the VHT80 channel width. I’m still testing this right now. The con of doing this is that it doesn’t penetrate as well so even a couple of layers of drywall and you’re going to get a significant drop in signal. In these areas of the home where I really want those 800+ Mbps speeds I plan on replacing the in-wall CAT5e wallplates/keystone jacks with the AC In-Wall APs and I should be good. By the way, the fastest device I’ve been able to test is a 2×2 MIMO device and it can do 867 Mbps with ease on these APs. As better devices come out I’m sure I’ll see these speeds creep up even higher so I don’t think I’m fully using these APs near their true potential yet. Some of you might ask why a wireless device needs local speeds like that on the LAN. If you have a Plex Media Server and very high quality content, you can almost completely saturate a 1 Gbps NIC on the server pushing a single high quality video/multi-channel audio stream for example. I can’t even imagine how it’s going to be once 4K/UHD playback is fully supported. I like to think ahead and make sure I’m building infrastructure that is going to serve me well into the future.
UBNT does not have a technical support phone number which is really disappointing to me. You call any IoT vendor like Ring, Rachio, etc. you get immediate phone support but for a consumer through enterprise focused networking company, UBNT has no phone options from what I can see. You have to go to their website and start a chat to get help. There were a few hiccups during my testing stage. After a firmware upgrade an AP thought it was being managed by a “ghost” controller and wouldn’t let it self be “adopted” again. There were no answers on the forums on how to re-adopt. Another hiccup was after a Cloud Key firmware update it would no longer do SSO. The 2 times I had to reach out to Support they were helpful, first time I was up and running within 15 minutes, second time the chat never connected but they followed up by email the next day at which point I had solved the problem myself. I’m just setting expectations with you all, don’t go in thinking you’re going to get immediate help with UBNT when you hit a hurdle. With that said, the forums is where UBNT shines. Sometimes a helpful and enthusiastic community is what makes a product appealing and that really helped me make my choice. A lot of the advanced configurations I will be doing have already been done and shared by others: https://community.ubnt.com/t5/custom/page/page-id/Forums
Just a few weeks in now and having about 95% of my WiFi devices on this new gear I definitely know I made the right choice. I haven’t even scratched the service in available features yet. I’m going to go over some basic stuff I’m using now so think of this guide as just an intro into UniFi gear.
Segmenting Network Traffic
What’s beautiful about UniFi is how easy it is to create wireless networks. I decided for the time being to segment my traffic almost the same way as I did with my old gear. Each of these is it’s own SSID:
- 2.4 Ghz SSID for legacy devices
- 5 Ghz SSID for everything else
- Dual radio (2.4 Ghz/5 Ghz) SSID for guest traffic
- Dual radio (2.4 Ghz/5 Ghz) SSID for IoT traffic
- Dual radio (2.4 Ghz/5 Ghz) SSID for lab traffic (enabled only when needed)
I like to force my 5 Ghz capable devices onto their own radio which is why I am splitting legacy and newer devices. I want to see where 5 Ghz has trouble and improve the coverage in those areas using 802.11ac compatible In-Wall APs. Especially since I’m using the VHT80 channel width right now. I don’t ever want them to drop down to the 2.4 Ghz radio.
For guest traffic, UniFi offers some out of the box features I think are freaking awesome like a captive portal with vouchers. A real wow factor when guests come over and ask to for the WiFi password. 🙂 I’ll get into that more later on.
UniFi allows you to add a VLAN to the SSID so my IoT traffic can be segmented off from the rest of the network like guest traffic but without all the extra bells and whistles. I can make my regular devices talk to the IoT network and allow those IoT devices to respond back but the IoT network can never initiate communication to the regular devices. Keep in mind many IoT devices are 2.4 Ghz devices because you are more concerned about signal and range which 2.4 Ghz is superior at compared to 5 Ghz. For this reason they only have the single radio and cannot connect to 5 Ghz. Just letting you know so you’re not shocked when you see so many 2.4 Ghz devices connecting even though you may have just recently bought them. It’s for cost and power savings.
Finally the lab traffic SSID is something I enable only when I need. It’s for isolating traffic completely when I’m doing some involved testing. It’s on it’s own WLAN group and I can enable it on the closet AP to the lab when I need it.
The AC Pro APs
You walk into Best Buy and look at their access point/routers these days and they look like they came out of Skunk Works. I don’t need my AP to look like Darth Vader with 14 antennas sticking out of it. The AC Pros are just nice clean circular discs and honestly remind me of the old Cisco Aironet APs from much earlier in my career. They just blend in with the decor.

You can tell they put a lot of thought into the design. The back mounting ring comes off easily with just 1 little locking tab.

It has a secondary RJ45 port you can use for bridging if you need it. It has a removable channel piece so you can route your CAT5e/CAT6 cable easily. The LEDs are blue and can be made to blink to locate them (think big deployments) or you can completely turn them off which is handy if you plan on mounting these guys in bedrooms. They are also weather resistant so no problems putting them out on a patio.

Nice little rubber cover to keep your ports weather sealed. The RJ45 connector will pass-through the hole just fine. No need to cut the end off, pass the cable through, then crimp a new connector on like I thought at first glance.

If you buy single units you will get a power injector wall wart. If you buy a bulk pack they won’t come with the power injectors because they expect you are using a PoE switch with them. The power injector looks like a regular AC adapter except it has 2 RJ45 ports. You plug one port into your regular non-PoE switch and the other port which combines that data + the power from the wall into the AC Pro. What I like about this design is if your house is already wired with CAT5e and you don’t want to use a PoE switch, you can just plug your AC Pro into one of these RJ45 ports. Then in your low voltage panel where all your CAT5Es are run to, you can just plug all your PoE injectors into a UPS and now you’ve got some redundancy when there’s a power blip. This gives you a very clean install on all the locations you’re going to be installing these APs.

Now my house is pre-wired with CAT5e wall jacks at outlet height and these APs are truly designed to be mounted on the ceiling dispersing their signal downward. Upstairs locations are easy to deploy on ceilings since you have attic space to work in. In downstairs locations I can always cut a small hole in the drywall near the ceiling, disconnect the keystone jack from the wall plate and pull the twisted pair wires off, run the cable up through the whole at the top, add an RJ45 connector, and plug this CAT5e into the AP so I can mount them higher up on the wall. Initially I thought about just connecting a small white CAT5e patch cable from my outlet height port and mount the AP just above the jack to keep it simple. In my super scientific testing of placing the AP on the bottom rung of a ladder vs. the top I found that the higher the AP was the better the signal was on a device that was connected nearby.

Signal reported by the device on the bottom rung:

Signal reported by the device on the top rung as pictured above:

So it’s definitely better to mount the APs as high as you can for optimal coverage but if you don’t and mount them outlet height it’s not the end of the world. They’ll still work pretty darn well.
For now I’m not screwing the mounting bracket into my wall. Since I’m still figuring out final placements and wanting to wait to finalize until I get those AC In-Walls I am using this wonderful stuff called 3M Dual Lock to mount my APs to the walls.
I’ve been using this over velcro for a lot of things lately and I don’t think I’ll ever go back. Just buy a roll and thank me later. A little bit of this stuff is strong enough to hold the lightweight APs with no trouble. If you are unsure of placement, I highly recommend using this or some other temporary method like 3M Command Hooks before you start drilling holes and mounting things permanently. Warning, 3M Dual Lock is strong and will mess up your paint if you pull it off so expect to do minor paint touch-ups if you remove it later.
The Cloud Key and UniFi Controller
UniFi Controller is the name of the software to centrally manage all your UniFi gear (WiFi access points, switches, gateways, cameras, whatever). It is the core of their SDN (Software Defined Networking) platform. It can be installed on a variety of OSes as you can see at https://www.ubnt.com/download/unifi but honestly, just buy the Cloud Key instead. The UniFi Cloud Key is a hardened purpose built hybrid cloud device that has Unifi Controller running on it but also allows you to securely manage your network remotely through the cloud.
What I really love about it is that it supports PoE so you can just plug it into any switch and it will get power and be able to manage your network. Right now I have it plugged into my non-PoE switch as you can see here so I have to use the AC adapter and have it hanging off like this. When I get some PoE switches I’ll just plug this in and tuck it off to the side.

The other great thing is the automated backups. It comes with an 8 GB microSD card you pop in here and it will do weekly or whatever interval you set backups for you to that microSD card. You can even choose how many backups to keep. It just doesn’t make sense to me to dedicate a system or even a Raspberry Pi when the the cost of the Cloud Key is not much more and gives you these perks.

Now let’s go into some of the Controller screens. Fair warning, I’m only showing you some of the basics I thought were really cool. There is so much more and I’d have to do a series of articles to really go through things in detail.
The main dashboard
You can see here it’s pretty blank right now because some of these graphs require UniFi Security Gateway (USG) and UniFi switches to grab WAN and LAN data. It’s only currently populating WLAN because all I have are the wireless APs. This screen is far more impressive when you have those devices collecting data and I will be adding those soon. I do want to note that DPI (deep packet inspection) with USG is not true DPI like we’re used to in Enterprise. You’re not going to get URLs and GET/POSTS. It’s not going to alert on anomalous DNS requests indicating a sign of a compromise. There is no packet header inspection to that degree from what I can tell. Once I get a USG in hand at some point soon I’ll be able to dig into it a bit more and verify what all it can do.
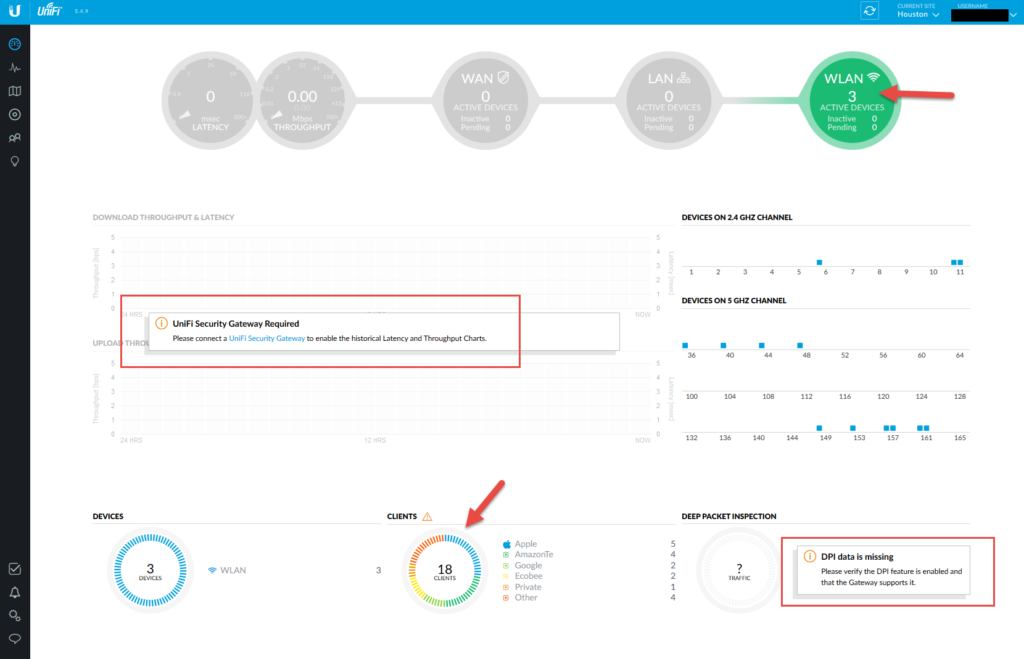
The statistics view
I have 18 clients connected at this exact moment and this shows off each of my SSIDs and how much traffic is being put through each AP. There’s also a historical graph at the bottom and you can kind of see when people start going to sleep and waking up.
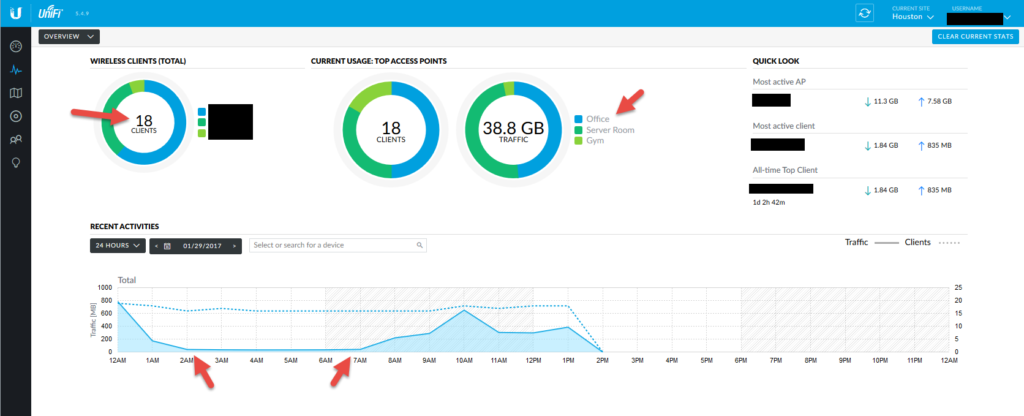
The map view
If you have a floorplan of your house (or office, hotel, stadium, whatever) you can upload it here and place your APs so you can figure out what your coverage looks like with a heat map. I haven’t uploaded mine yet but here’s me dropping my APs on the default sample map to give you an idea of how my 5 Ghz coverage looks like.
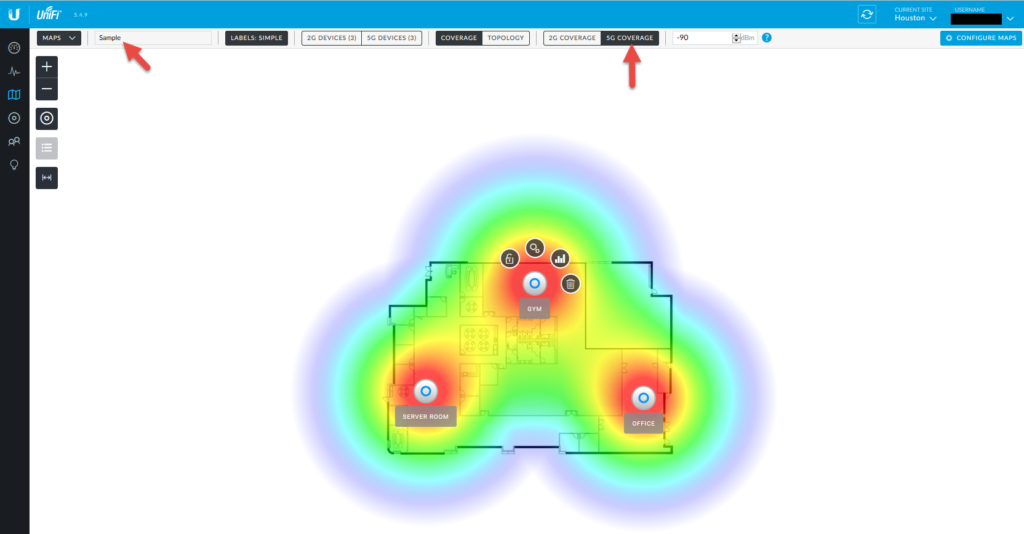
There is also a very cool topology map that shows you what APs your clients are connected to:
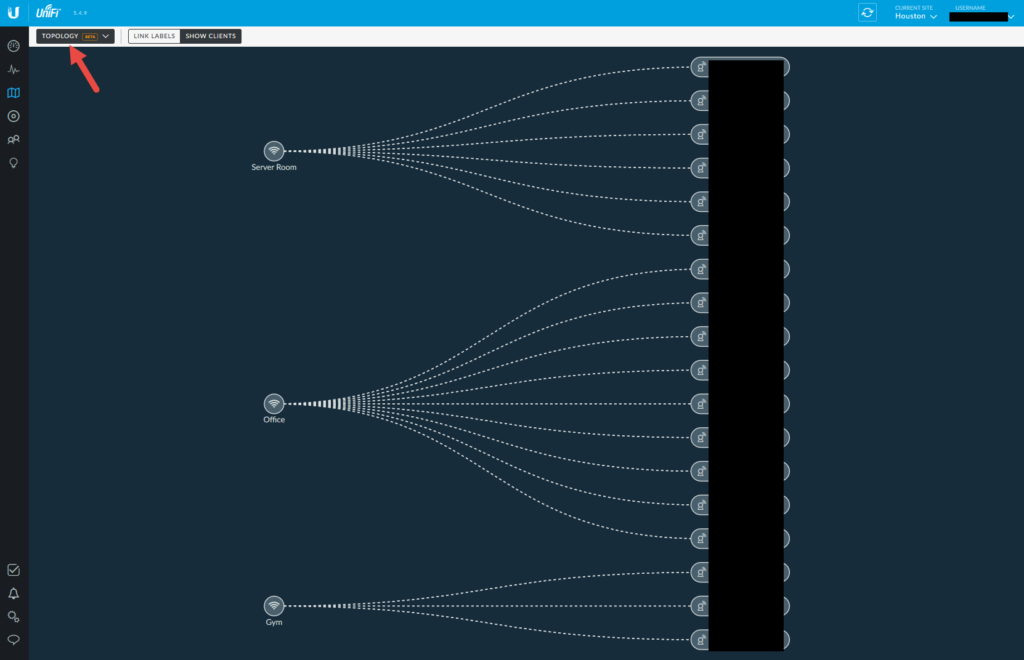
The devices view
Really nice way to see all your Unifi devices. You can schedule auto updates and restart them from here by the way. The process of buying and adding a new device is called “adopting” and it literally a single click and it gets the config the other APs have. So easy. Make sure to play with the litte gear on the right so you can add additional columns. You can see here I like to look at quite a bit of data from the AP radios so have a lot of columns displayed.
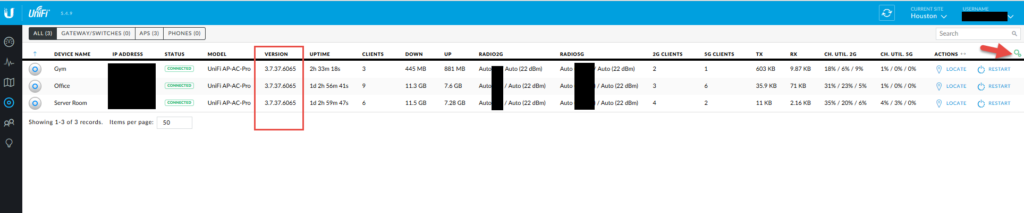
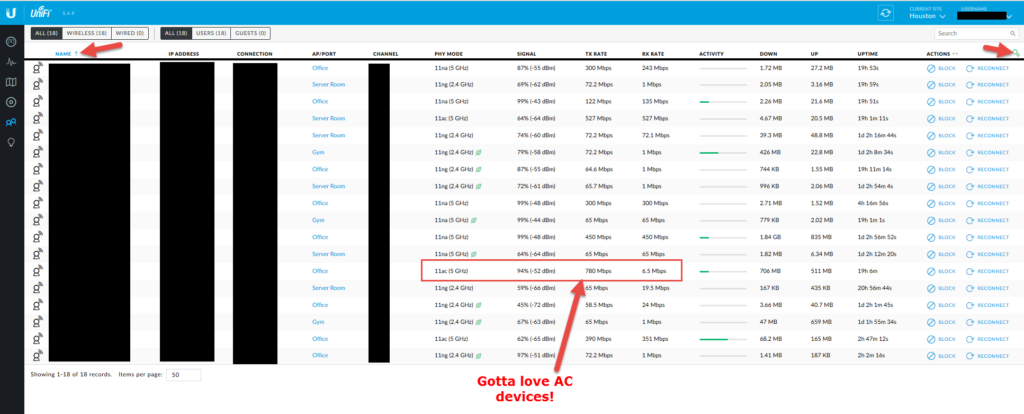
The clients view
Finally! My favorite view! You can click the gear and add the extra columns I show below. Easy to sort by any of these columns to see where some areas may need more coverage or you have a really old device and need to upgrade it. You can also alias your devices so if you have a bunch of devices that show up as an alpha-numeric mess for a host name you can edit it to something that makes more sense like “Amazon-Echo-Kitchen”. Very handy feature! You can see 802.11ac devices out pace older devices by far. 🙂
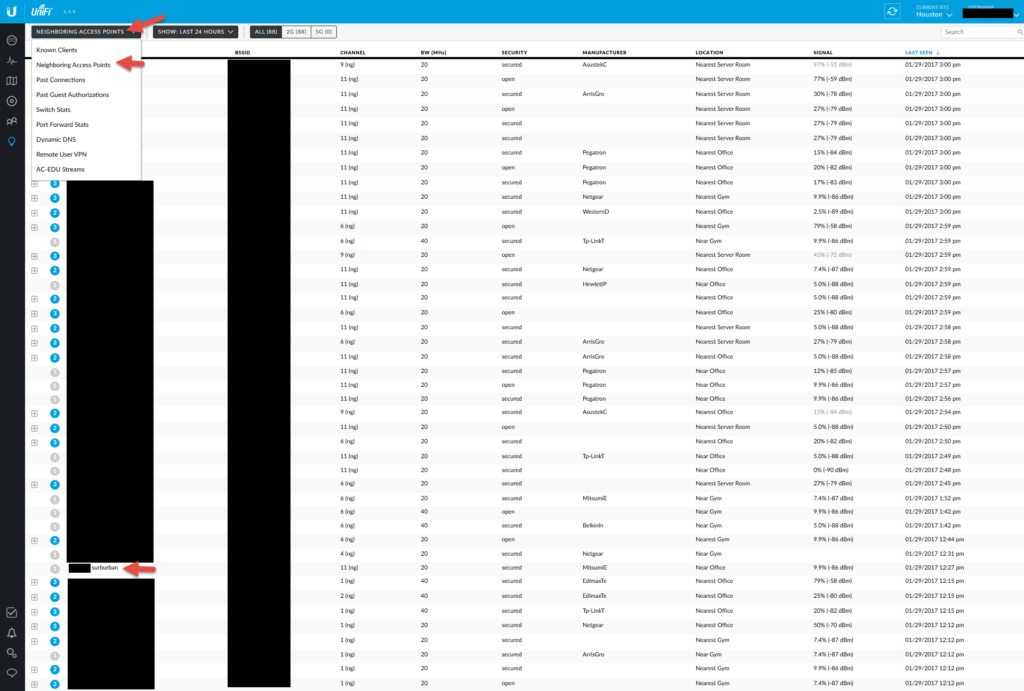
The insights view
This is where you can get some pretty cool info about the types of devices in your environment. You can see past device connection history and all the known clients that have ever connected to your network. There’s also a neighboring APs view. I didn’t realized how many vehicles have built in WiFi hotspots in them these days. I’ve been picking up Tahoes, Suburbans, Denalis, Cadillacs, GMCs, etc. that keep driving by my house! Brings a whole new spin to wardriving. 🙂 They also seem to be using Mitsumi Electric components which is one of the companies that produces the in-dash navigation parts for XM Satellite Radio.
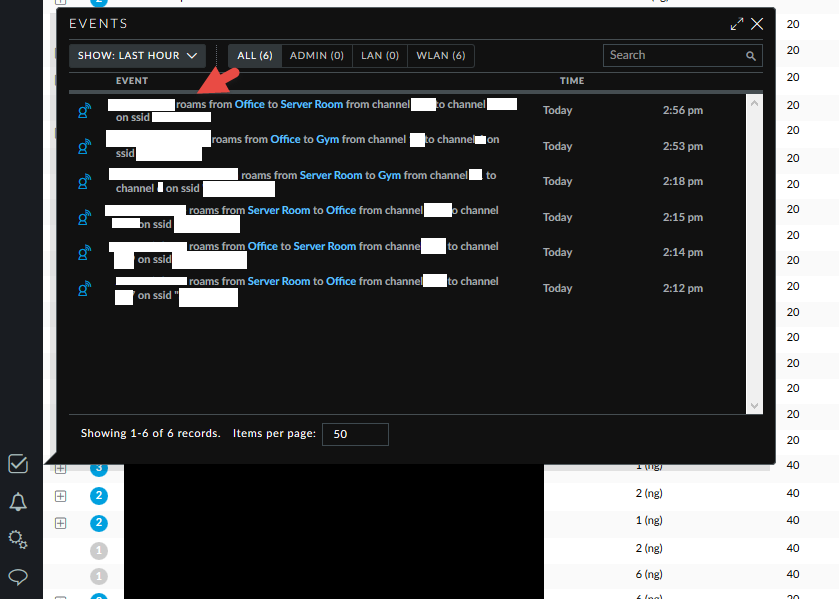
The events view
This is really nice to watch your devices roam from AP to AP in real time.
The alerts view
This is what I don’t like. You can’t really configure any alerts. I want be alerted when a new device gets added to my network for example. Or someone trys to login with a bad WPA2 key. I can’t find any way to setup email alerts for these kinds of things. I wish there was some kind of “if this then that” logic you can use to create custom alerts from the events. From what I’ve seen so far you may have to syslog this out if it even captures that stuff. I need to explore these options further.
THE UNIFI MOBILE APP
This is where in my opinion the Cloud Key really shines. You can manage and even reconfigure your APs from anywhere in the world using the app. You even have the ability to block devices on your network or force them to reconnect. Remember October 2016 and the big IoT botnet DDoS attack that took down half the Internet? If you noticed you had any compromised devices and weren’t home you could simply login through the Unifi mobile app/Cloud Key and hit block on those devices so you can deal with them when you got back home.
Once you authenticate using TouchID it will show you your Cloud Key, click on it:
The dashboard give you a quick overview like the web GUI:
You can see all your devices and drill down into them to manage or reconfigure them:
You can see all the connected clients and very easily see if they are on 2G or 5G (orange vs. green):
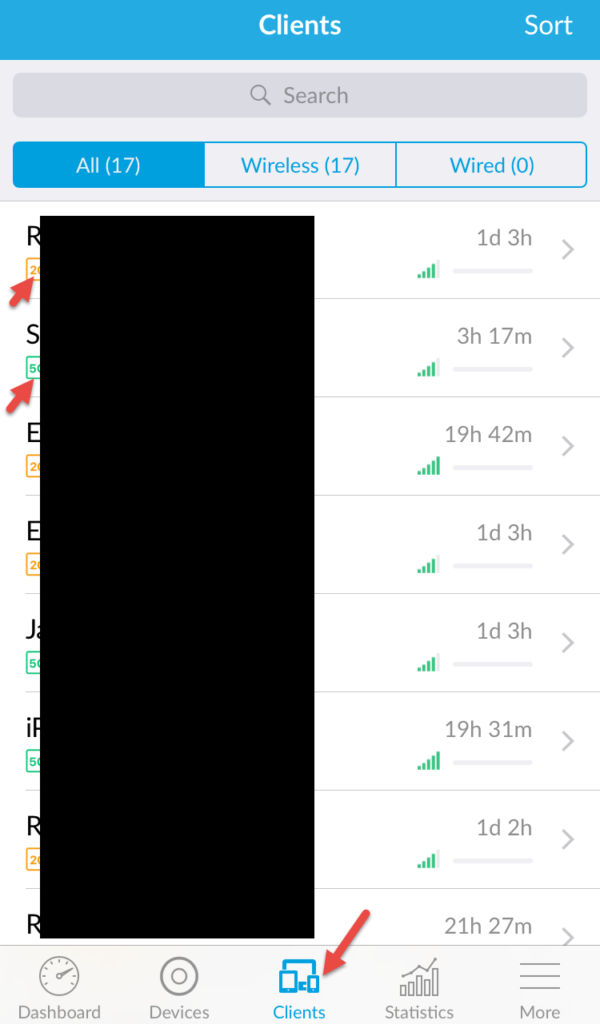
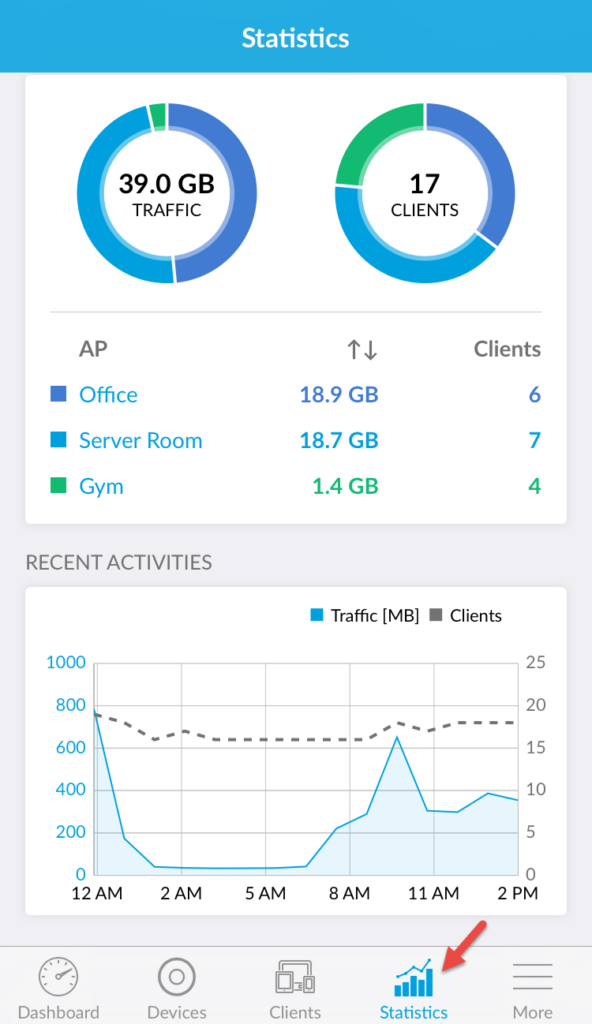
Statistics is pretty cool, same stats as on the web:
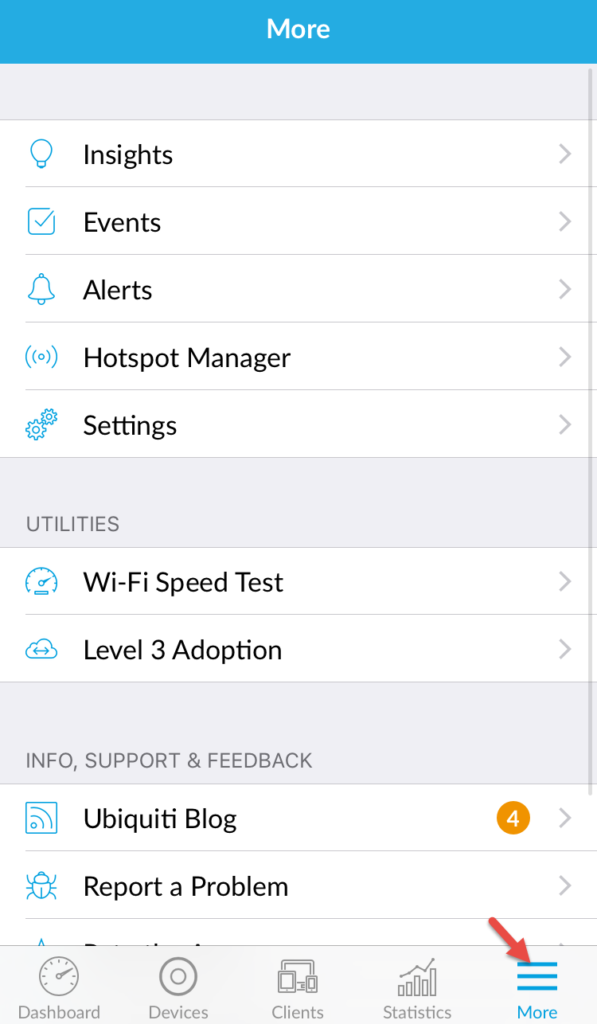
Lastly the more tab give you Insights, Events, Alerts, and the very awesome Hotspot Manager which I’ll cover more later:
Events are great but again, no way to just select it and say “Alert on events like this” or something:

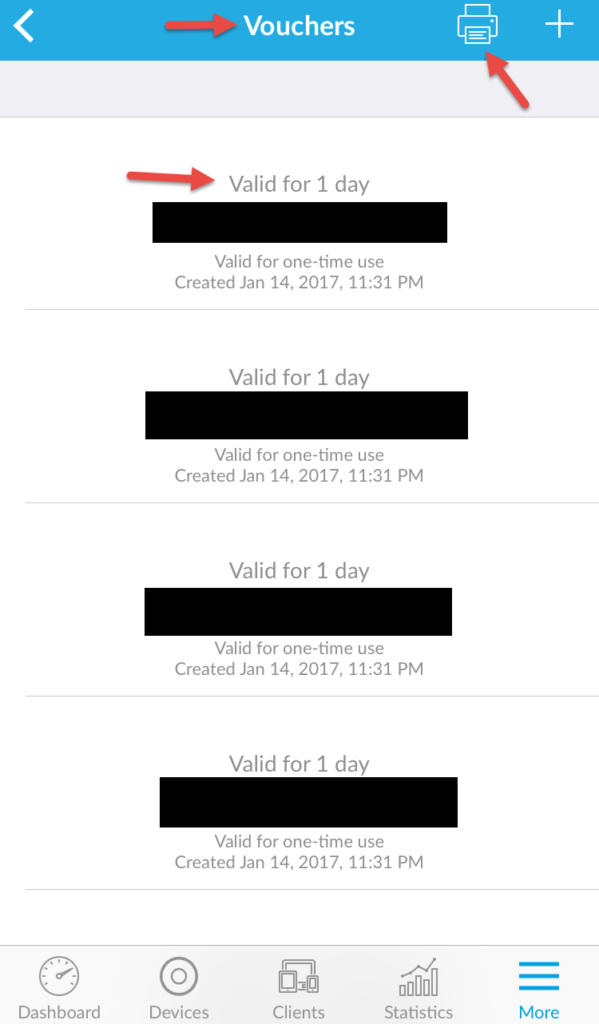
And lastly, the HotSpot Manager vouchers. These are for your guests. You can print them out or generate more anytime. My big complaint about these is that you can’t click on them to copy the voucher code to your clipboard so you can SMS it to your guests for easy entry. Hope that gets changed in an upcoming version. Would be even cooler if there was a share button next to each and you can choose from SMS, email, etc:
CREATING A HOTEL LIKE EXPERIENCE FOR GUESTS
And that takes me into the next topic…your guests. I always hated giving a visitor to my home the WPA2 Key to the guest network. They’ll come over and visit once and then 3 months later show up again and be automatically connected to my WiFi without even knowing. I don’t want to change the guest key every time I have a guest leave my house. So I protect the guest network with a WPA2 key and a captive portal. The guest has to enter a voucher that’s good for 24 hours of WiFi access into the captive portal. They get this voucher code from me or anyone I deem as an “Operator”. Unfortunately Operators will have to login to the web UI in order to do this as there is no role based access in the UniFi mobile app. I have seen on the forums that they are considering releasing another “UniFi HotSpot Manager” mobile app that operators can use for this purpose.
The process of getting this type of guest network setup is extremely simple. After creating your Guest network and security key make sure you check the box for the Guest Policy:
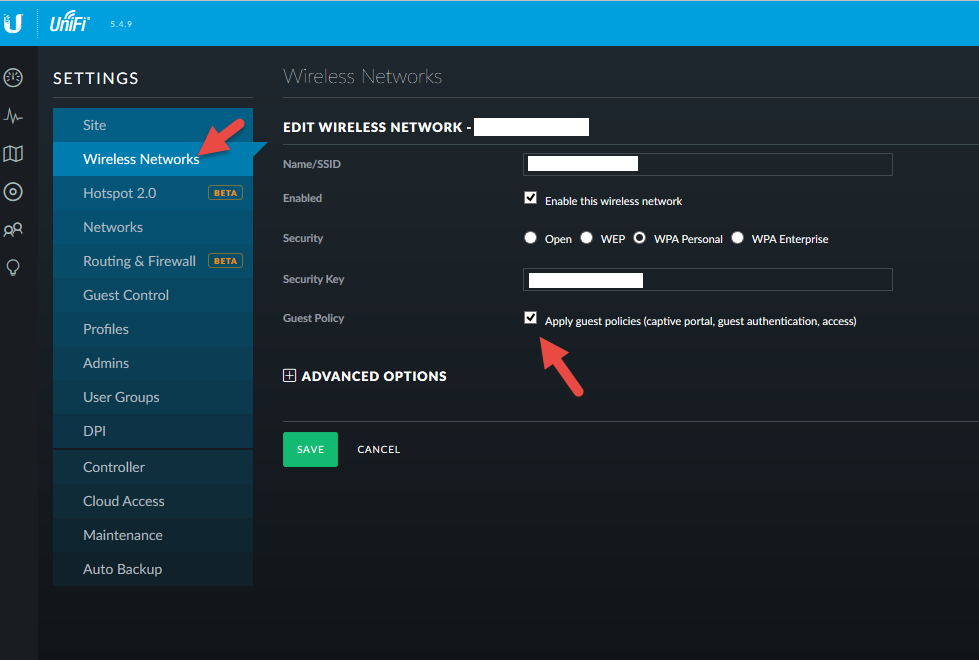
Now head over to the Guest Control section and make sure the Guest Portal is enabled. This is the captive portal. Make sure it’s set for Hotspot mode. Enable AngularJS which unlocks all the cool customization options. Then modify as needed. Remember to use both the Desktop Preview and Mobile Preview so you can see how everything looks in real-time as you make the changes. At the bottom enable the voucher-based authentication and then go to the HotSpot Manager to create vouchers, create operators, etc.
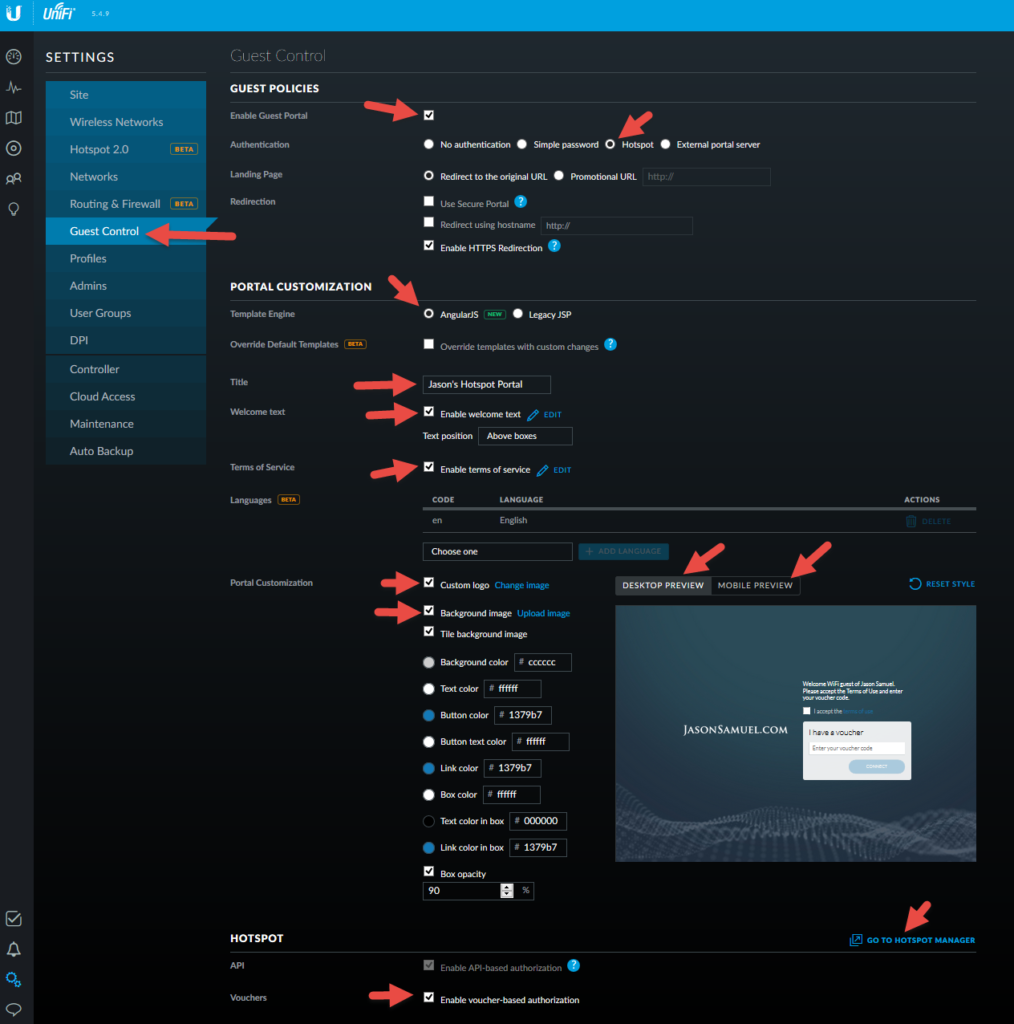
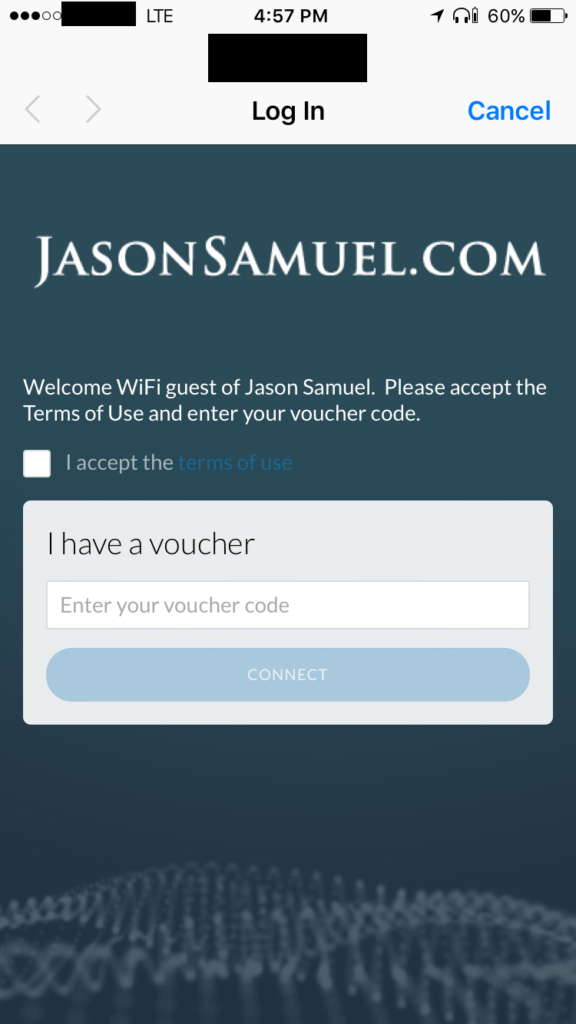
Now the user experience is that when the Guest comes over to visit, they need to be given the WPA2 key first. This never changes. Once they enter the key they are taken to the HotSpot portal to enter their 24 hour one time use voucher. This is what sets the limits on their session so when they come back in 3 months to visit they’ll get auto joined to the WiFi but will land at the captive portal and can’t do anything until I issue them another voucher. On a mobile device my HotSpot captive portal looks like this:
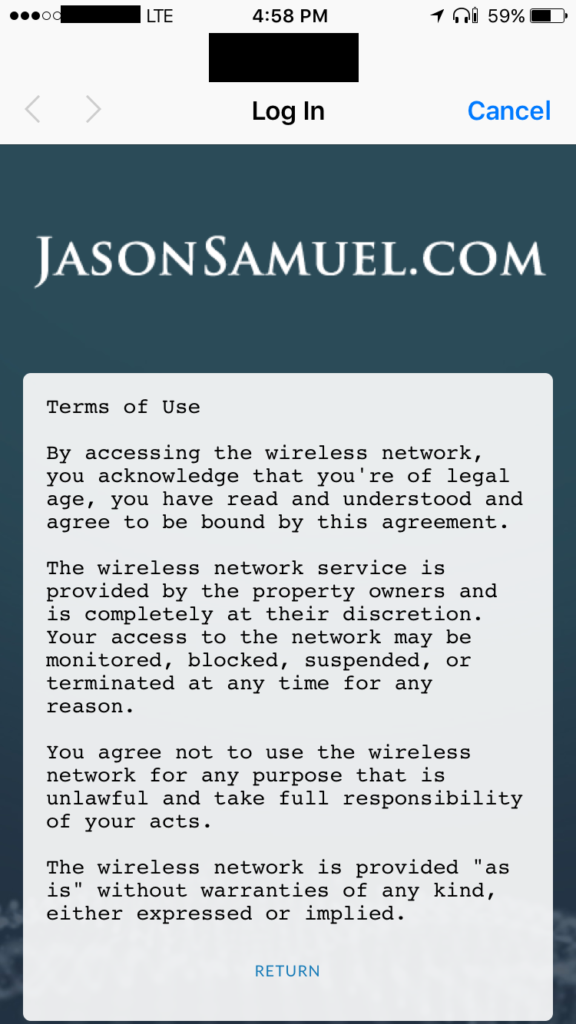
The Terms of Use looks like this. Make sure you have something in there about monitoring so you don’t get sued or something if you’re a hotel and using DPI:
The confirmation page is hideous. I’m not sure if this is because it’s redirecting to captive.apple.com or something. Ideally I’d want it to match my theme:

Now what’s cool as an Operator, I can see the code the guest used to login and I can also extend their session beyond the 24 hours very easily from both the mobile app and the web UI. So if I have a guest staying the weekend or something I immediately go in here and hit extend a few times and I know they’ll be good for the duration of their stay without needing another voucher:
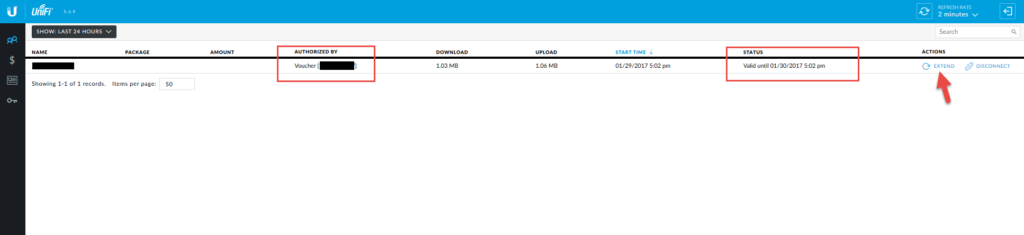
When using the mobile app it might not be obvious how to do this. You need to swipe to the left in order for the Extend option to show up. Each time you press Extend it adds an extra 24 hours to the voucher session:
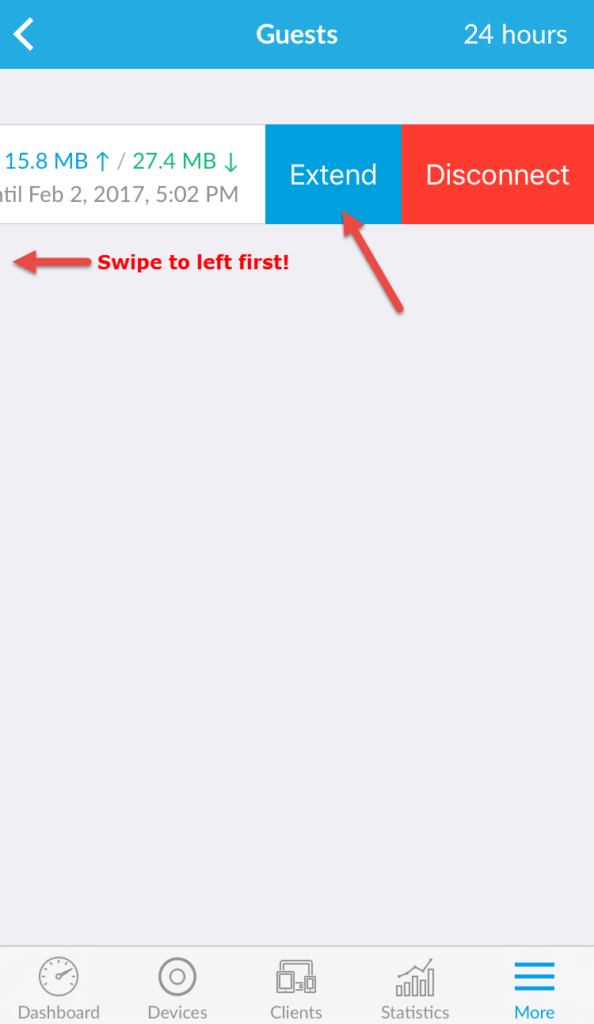
The other thing I want to note is that can you can apply pre and post authorization subnets so these HotSpot users only have access to certain subnets at each stage of access control. Really cool feature:

FUTURE
Using UniFi for a few weeks now I can appreciate that it’s built with an engineer first mindset. I’ve used a lot of gear in the past where you can tell corporate marketing/GUI designers took over and really dumbed things down to make it palatable to the masses. UBNT doesn’t feel like that, it’s almost like functionality was first and foremost and then they wrapped it in a slick design.
So what am I planning in the future with UniFI (when funds allow it)?
- Grabbing 2 of those AC In-Wall APs as soon as they are available.
- Researching if everything the EdgeMAX EdgeRouter line my buddy and fellow CTP Trond Eirik Haavarstein talks about here he modeled after Richard Parnell’s SD-WAN demo will work with UniFI Security Gateway Pro (USG Pro 4)
: http://xenappblog.com/2016/cheapest-dual-wan-router-for-failover/. Customizing USG is a painful process vs. the EdgeRouter line but friend and CTP Jarian Gibson showed me this post saying not to worry, a lot of what I want to do is coming to USG soon: https://community.ubnt.com/t5/UniFi-Routing-Switching/USG-Feature-Roadmap-January-2017-update/td-p/1792230. I’d like to stick with USG because you can view and manage it using the UniFi Controller. You can’t use the UniFi Controller with EdgeMAX gear unfortunately since it’s a completely different line of products.
- Grabbing a Ubiquiti UniFi 24 Port Managed PoE switch (US-24-250W)
and UniFi 16 Port Managed PoE Switch (US‑16‑150W)
to replace my non-PoE switches. I advise getting PoE if you’re home running your APs. When I bring up PoE people always think VoIP but as you can see it comes in handy for APs, Cloud Key, surveillance cameras, etc. Get a small UniFi 8 port PoE Switch (US-8-60W)
for those needs and a regular gigabit switch for the more day to day needs if you don’t want to invest in one the larger PoE switches.
Hope this little intro guide to UniFi has helped you out. If you would like a deep dive into any UniFi features let me know. If you have any questions or comments please leave them below.
Jason Samuel is a visionary product leader and trusted advisor with a proven track record of shaping strategy and driving technology innovation. With extensive expertise in enterprise end-user computing, security, cloud, automation, and virtualization technologies, Jason has become a globally recognized authority in the IT industry. His career spans consulting for hundreds of Fortune 500 enterprises across diverse business sectors worldwide, delivering cutting-edge digital solutions from Citrix, Microsoft, VMware, Amazon, Google, and NVIDIA that seamlessly balance security with exceptional user experiences.
Jason’s leadership is amplified by his dedication to knowledge-sharing as an author, speaker, podcaster, and mentor within the global IT and technology community. Recognized with numerous prestigious awards, Jason’s contributions underscore his commitment to advancing technology and empowering organizations to achieve transformative results. Follow him on LinkedIn.
Disclaimer: Views expressed here are his own and do not reflect the views of his employer, past or present, or any organizations he is affiliated with. Content is for informational or personal purposes only.











William Bluhm
January 30, 2017 at 9:28 PM
Jason,
I am curious to know how you got your hotspot portal working. I’ve been trying to get mine setup and when I connect to the “hotspot” it gets certificate error. How did you get around this?
William B.
Jason Samuel
January 30, 2017 at 10:18 PM
Hi William, I have not had that issue on my mobile devices or laptops. Everything in my screenshot above of the Guest Control section is how its all running right now. My HotSpot portal is using HTTP (though I would like to put a public cert on it soon and use HTTPS with a custom URL). Do you have “Use Secure Portal” unchecked like in my screenshot? Is this happening on all your devices/browsers? Are you running the latest Controller version?
William Bluhm
January 31, 2017 at 11:40 AM
Jason,
Upon looking back at my settings, I verified that the “Use Secure Portal” is not checked, however “Enable HTTPS Redirection” is enabled. So far it is only happening on mobile devices such as a Galaxy S7 and a Galaxy Tab 2. My laptop proceeds just like it would at a hotel. I am using Controller version 5.4.9 (https://goo.gl/H6xJVe) which was recently released as a stable version.
george sumner
February 16, 2017 at 6:06 PM
Thanks Jason. Fascinating reading. Very helpful — I’m about to set up a similar, though simpler, network. More than a how-to, it gave me a much better understanding of how it all works. Also great to watch a genius at work 🙂
I’m about to buy the gear and had decided to go with the EdgeRouter but now I’ll take another look at the USG, which at the moment I don’t really understand. You make a convincing case for making the jump though. Thanks again.
George
Kenneth Dixon
February 24, 2017 at 9:57 AM
Impressive article!! Thank you for the time and effort to share your knowledge.
Richard Schwab
June 19, 2017 at 12:28 PM
I am encountering an interesting situation and am wondering if you have experienced it. We installed a Unifi network which entailed connecting a cloud Key to our network switch and installing three UAP-AC-PRO access points. We set up two wireless networks, one of them being for guests. This guest network is secured and we have set up voucher authentication. A number of voucher codes have been issued and for the most part this has worked beautifully. Today I issued a new voucher code to a client to replace an expired one. The client is getting a “Authentication error occurred” on her Android phone and she is unable to browse on the Internet. Any thoughts?
Richard Schwab
June 19, 2017 at 1:16 PM
I am encountering an interesting situation and am wondering if you have experienced it. We installed a Unifi network which entailed connecting a cloud Key to our network switch and installing three UAP-AC-PRO access points. We set up two wireless networks, one of them being for guests. This guest network is secured and we have set up voucher authentication. A number of voucher codes have been issued and for the most part this has worked beautifully. Today I issued a new voucher code to a client to replace an expired one. The client is getting an “Authentication error occurred” on her Android phone and she is unable to browse on the Internet. Any thoughts?
Cassie
April 20, 2018 at 5:07 PM
Is there a way to create this portal to use an open network? I’d prefer not to have my guests type in two different “passwords”.
Thanks!
Bill Drummond
December 18, 2018 at 2:24 PM
We are looking at replacing APs in two Auditoriums and one in a common area. This will be just guest access and we want to assign each user/device a login name and password and provide seamless roaming via a single SSID for the site. We look at purchasing the Pro model AP and Cloud key. Will this equipment and management software allow us to configure and manage the APs and users?