Throughout the past year, I’ve been involved with many successful projects involving services in Citrix Cloud, primarily Citrix Virtual Apps and Desktops Service. The advantages of having an always up to date control plane offers too many advantages for most companies to pass up. One of the common questions that comes up is whether to use the new Workspace experience with Gateway Service or if you should continue using on premises or IaaS deployed StoreFront and NetScaler Gateway. I’d like to go over some experiences from the field I’ve come across to help you make your decision.
StoreFront vs. Workspace
One misconception I keep seeing is that Workspace is just the cloud version of StoreFront. This is incorrect, StoreFront does not equal Workspace. Workspace is not just a cloud-based version of StoreFront but an evolution of StoreFront. There is no version of this exact Workspace experience for on-prem and I doubt there ever will be since it has so many cloud integration points, it would be next to impossible to maintain an on-prem platform at the pace of innovation in my opinion. StoreFront on-prem is great but it’s not the same experience as Workspace. It’s like trying to maintain Exchange on-prem while your peers are all using O365 with the latest bells and whistles and a better user experience. Your company will eventually gravitate to where your industry peers are, it’s just a question of WHEN it is right for your company specifically.
So what does Workspace give you over StoreFront?
- Ability to enumerate Virtual Apps and Desktop Service in Citrix Cloud (previously known as XenApp and XenDesktop Service). You will also see me shorten this to CVAD Service (Citrix Virtual Apps and Desktop Service) in this write up in the interest of extending my keyboard’s useful life. Keep in mind your VDAs can reside anywhere. On premises in your datacenter or in a public cloud of your choosing. No VDAs are hosted in Citrix Cloud itself since it’s only a PaaS control plane offering. You just point your VDAs at the Cloud Connectors you stand up in your datacenter and you’re done. If you need help understanding the architecture read my guide here: https://www.jasonsamuel.com/2018/01/23/how-to-extend-your-on-premises-xenapp-xendesktop-environment-to-citrix-cloud-xa-xd-service-and-microsoft-azure/
- Ability to enumerate on premises Citrix Virtual Apps and Desktops (previously known as XenApp and XenDesktop) through the Site Aggregation feature. Yes including XenApp 7.15 LTSR which many of my customers are on. This gives you the ability to immediately suck in all your on premises VDAs in one click and show them on your new yourcompany.cloud.com Workspace URL. You DO NOT need to repoint all your VDAs to your Cloud Connectors to do this. In fact you can have your new Workspace (yourcompany.cloud.com) URL show all these apps while simultaneously showing them on your legacy StoreFront+NetScaler Gateway on prem URL. That way you can migrate pockets of users to the new experience just by sending them an email saying “Hey, login at this URL today” without causing any disruption for the rest of the company. When you are ready to repoint your VDAs later on, it’s a very easy process. If you use PVS or MCS it’s just a simple update on your VDA to point at a local Cloud Controller within the image. If you have a bunch of static machines that are not using a single image management technology like PVS or MCS then you can use ControlUp to quickly change the ListOfDDCs registry key value on groups of servers and restart the service to talk to the Cloud Connectors. No reboot required. I’ve used this method at several customers to migrate groups of servers in minutes to CVAD Service and it works great. Here’s a screenshot of how Site Aggregation works if you want to take the simple approach first. You can see a legacy XenApp 6.5 farm and 2 on premises XenApp sites 7.x sites (one is 7.15 LTSR the other 1811 CR) all being aggregated:
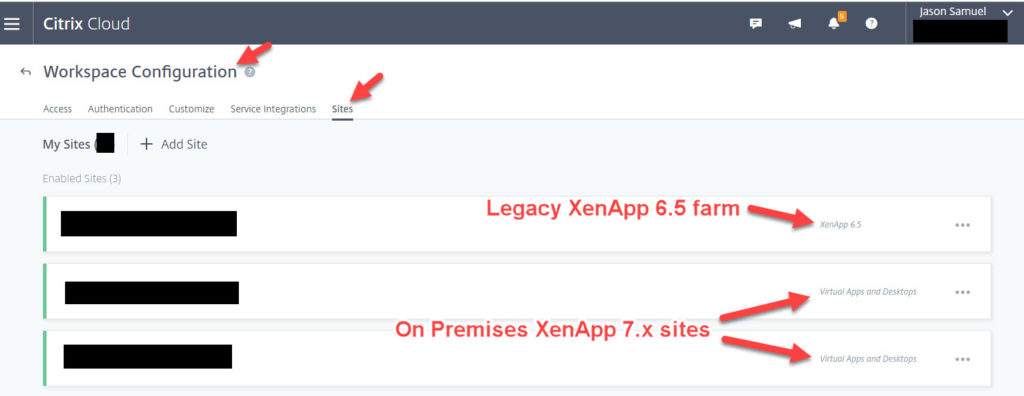
- Ability to enumerate on premises XenApp 6.5. Yes, which a handful of my customers are still on (typically inherited environments from acquisitions) and trying to finish migrating off ASAP. As you can see in the screenshot above, using the Site Aggregation feature basically propels legacy Citrix environments into a single URL modern cloud based Workspace experience while giving you a breather to shift the backend workloads to moderns OSes and VDAs at your own pace. Much better than having angry business units that are tired of going to multiple URLs for new vs. old vs. some other URL for some company you recently acquired. This ends the cobweb of URLs in one shot. The last “citrix migration” your users will ever have to experience is this final one to Workspace. Everything new and old will always be on this one URL.
- Ability to enumerate SaaS apps like Office365, SalesForce, Expensify, Concur, etc. with one click and full single sign-on to them. There’s a reason why I love modern authentication and tell people your identity is the new perimeter. Many apps an enterprise uses are becoming web apps. But Windows apps will always be there as well. How do you webify Windows apps designed to run on a Server OS? Well, that’s what we’ve been doing for the past 25+ years with Citrix if you really think about it. To the end user, it shouldn’t matter where apps are coming from. As long as you sign in once and can see all your apps in one spot regardless of it being from a Server OS or somewhere in someone’s cloud, and launch them without being prompted again for the same or different set of credentials, you have improved the user experience 100x from the mess I have seen with companies that haven’t quite embraced the digital workspace way of thinking.
- Ability to integrate Content Collaboration (previously known as ShareFile) to help deliver files easily to users. Either your own on-prem file repositories on NTFS shares, OpenText Documentum, etc. or cloud storage locations like OneDrive for Business. It’s all displayed seamlessly so the user doesn’t have to think where to go anymore, it’s just all there:
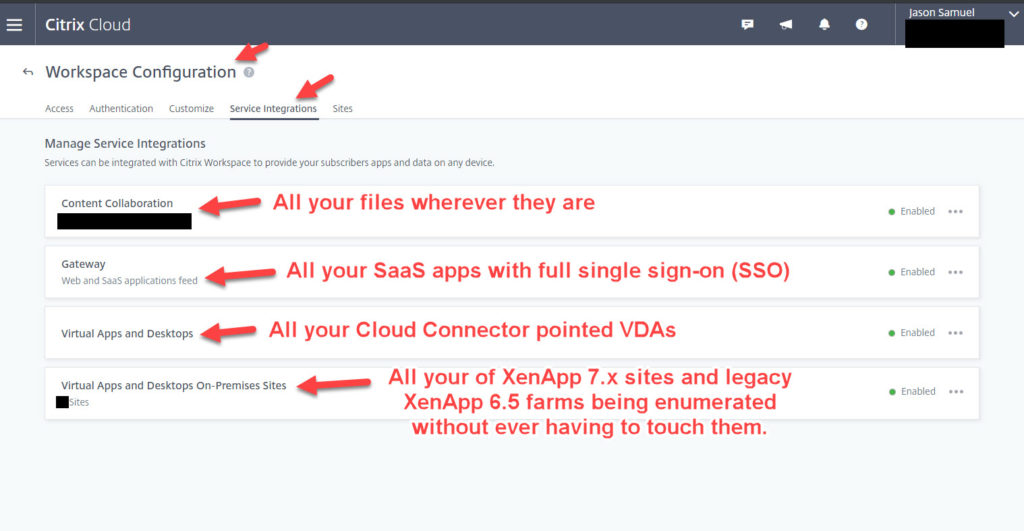
- Ability to enumerate physical desktops using Citrix Remote PC (which is built into both on-prem or cloud based CVAD and replaces the need for VPN + RDP to a physical endpoint which some of my customers still do believe it or not!). Many customers don’t realize the VDA (virtual delivery agent) actually works on physical desktops too. You install it the same way as you do in a VM and create a machine catalog of these physical Windows desktops. They will be shown under the Desktops section of Workspace and will launch just like a virtual desktop does leveraging the HDX secure remoting protocol. All those Windows 10 PCs under your users’ desks can be securely accessed the same way as if it were a virtual desktop running in your datacenter or public cloud if you wish. Without the need for a VPN tunnel and all the fun of split tunneling traffic and device posture which usually creates a headache for IT.
- Ability to enumerate other services in the future. I’m under NDA so can’t tell you what’s coming, but I promise you Citrix has some tricks up its sleeve and is working closely with the partner ecosystem. You will be very happy when things are announced publicly. 🙂 You can get a sneak peak here on this road-map that Citrix updated back on November 27, 2018 on what’s been launched so far and what’s in development: https://www.citrix.com/products/citrix-workspace/roadmap.html
- All wrapped around some intelligence. You see, on-prem StoreFront for the last 20+ years in all it’s incarnations has essentially just been an app launcher. You launch your app and then you minimize it for the rest of the day. What if it started understanding how each user uniquely works and started reacting to that making them more productive? A tailored experience for every user around everything in the enterprise they use. That’s the power of a cloud powered Workspace. It then becomes a productivity hub and not just an app launcher. Your users will start having it open next to Outlook now instead of minimizing it. My friend and fellow CTP Nicolas Ignoto has done a great job with an analysis of where he believes Workspace is going and has some quotes from Citrix executive leadership with their thoughts and vision here: https://www.citrixguru.com/2018/11/15/citrix-acquires-sapho-to-make-citrix-workspace-more-intelligent/. Further, I had the privilege of having a very enlightening meeting with PJ Hough (Chief Product Office at Citrix) last month in Orlando as well as Fouad ElNaggar (CEO of Sapho, now part of Citrix) just last week in California. The vision I hear from these leaders on what they are planning to deliver for Workspace is infectiously exciting. I just really don’t see anything quite exactly like this out there today. Listening to what they intend to deliver in the short term as well as their long term vision, I can see the value to enterprise users immediately and believe the adoption rate will be sky high. I hope licensing options are just as easy to adopt for companies so they can grow into these features quickly. Keep an eye out for more on this as things are announced more publicly. 🙂
NetScaler vs. Gateway Service
NetScaler is now known as Citrix ADC. NetScaler is now a legacy name but most folks still use it just to help make sure people understand it’s the same thing during this transitionary period. NetScaler Gateway and Unified Gateway modules are now known as Citrix Gateway.
Citrix ADC functions are primarily things like load balancing, SSL offloading, app firewall, content switching, rewrite, responder, etc. These are all ways of taking a packet and bending it to your will. This is what always made NetScaler such a special box. It comes in physical SDX and MPX form factors and virtual VPX as always. You can also deploy it in any cloud (Azure, AWS, GCP, etc.) or on premises hypervisors (ESXi, AHV, XenServer, Hyper-V, etc).
Citrix Gateway is the remote access component within Citrix ADC. You can deploy Citrix Gateway which is just HDX proxy only. Or you can deploy Unified Gateway where you get HDX proxy, SaaS apps, and SSL VPN in one spot. You can also tack on RDP Proxy and other little features if needed for your company. Everything I mentioned so far comes all together as part of your licensing and you can choose to pool your licensing for all your ADCs together and carve them out for on premises or public cloud ADCs on the fly.
The Citrix Gateway Service is the simplified version of the Gateway module that exists within your on premises NetScaler but delivered in Citrix Cloud as a PaaS offering. It is HDX proxy + SaaS apps. There is nothing to configure for HDX proxy, it is included and on by default when you purchase CVAD Service in Citrix Cloud which many people are doing these days. There are no vservers, SSL certs, SSL cipher settings, rate control settings, authentication policies, worrying about firmware upgrades, etc. with the HDX proxy capability of Gateway Service. It is ultra-simplistic and most of my customers don’t even realize they are using it since it’s on by default. You get an instant global deployment of your Workspace URL with no action needed to be taken by you. Look at this map to help illustrate what you get right out of the box with not a finger lifted by you, 12 POPS in a high resiliency multi-cloud deployment (Azure+AWS) globally load balancing yourcompany.cloud.com for you:
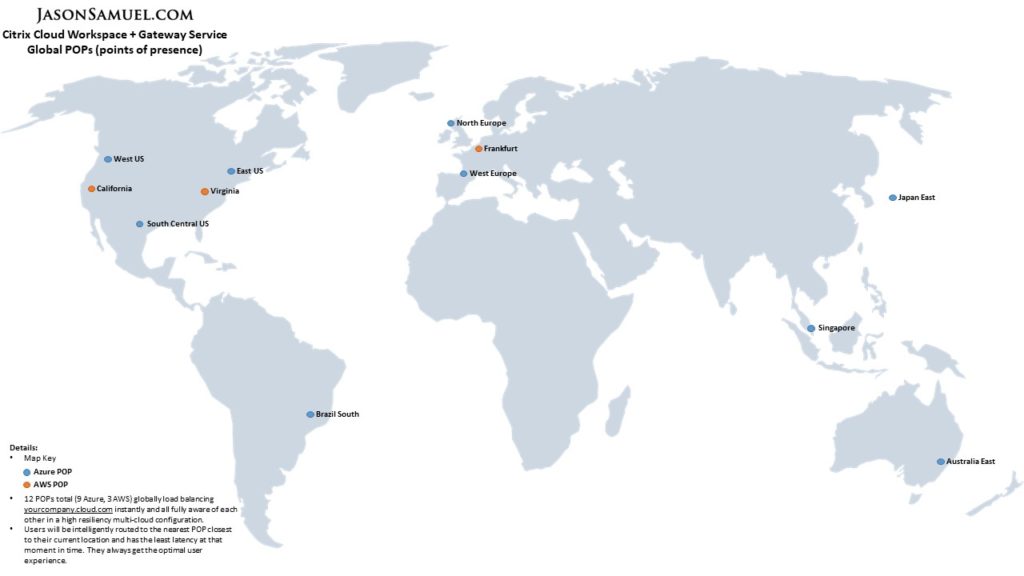
Think of it like Netflix. No matter where you travel in the world you will be able to watch Netflix because you have a monthly subscription to it. You may primarily watch movies and TV shows in the US but when you travel internationally, you are hitting the nearest Netflix POP that is closest to you. You will also see only the movies and TV shows that are available in that region. Netflix admins have decided what your user account can or cannot see when you travel to these regions.
Just like this Netflix example, you can have your own datacenters or use cloud regions in Azure, AWS, etc. in or near these same POPs. You can put your apps, desktops, and files as close to the user as you need or you can one-up the Netflix example and keep your resources within a single region but feed all these other regions with these resources for compliance and governance reasons. You still get to take advantage of the lower latency backbone if you have Azure ExpressRoute or AWS Direct Connect from your datacenters or simply have these resources already existing in IaaS in or near these POPs. This gives you the flexibility to build something even better than Netflix has done with their movies and TV show content, but for your enterprise content in the form of apps, desktops, and files!
Each user gets 1 GB of data transfer through the Gateway Service and Citrix does offer the ability to purchase more bandwidth if you need it. None of my customers have needed to purchase more to date by the way so don’t be scared off by that 1 GB cap. In fact, doing some network analysis with a few of my bigger deployments I know some users are going well over this and it has not been an issue.
When should you use which?
If you have on-prem licensing, then you can’t use Workspace + Gateway Service. You are limited to using on-prem StoreFront + NetScaler.
If you have Virtual Apps and Desktop Service licensing in Citrix Cloud, you can use Workspace + Gateway Service OR you can choose to use StoreFront + NetScaler Gateway on-prem if you’d like to. Most of my customers have embraced Workspace + Gateway Service when moving to a Citrix Cloud based control plane. It is a far superior administrative experience in my opinion than wiring up on prem StoreFront + NetScaler Gateway to the CVAD Service.
Some folks have chosen to use StoreFront + NetScaler today because:
- They need to use an on premises MFA solution based on RADIUS. At the time of writing this article, AD is supported but you cannot specify a RADIUS proxy down to an on-prem MFA solution. We know from https://www.citrix.com/products/citrix-workspace/roadmap.html that it is in development however:
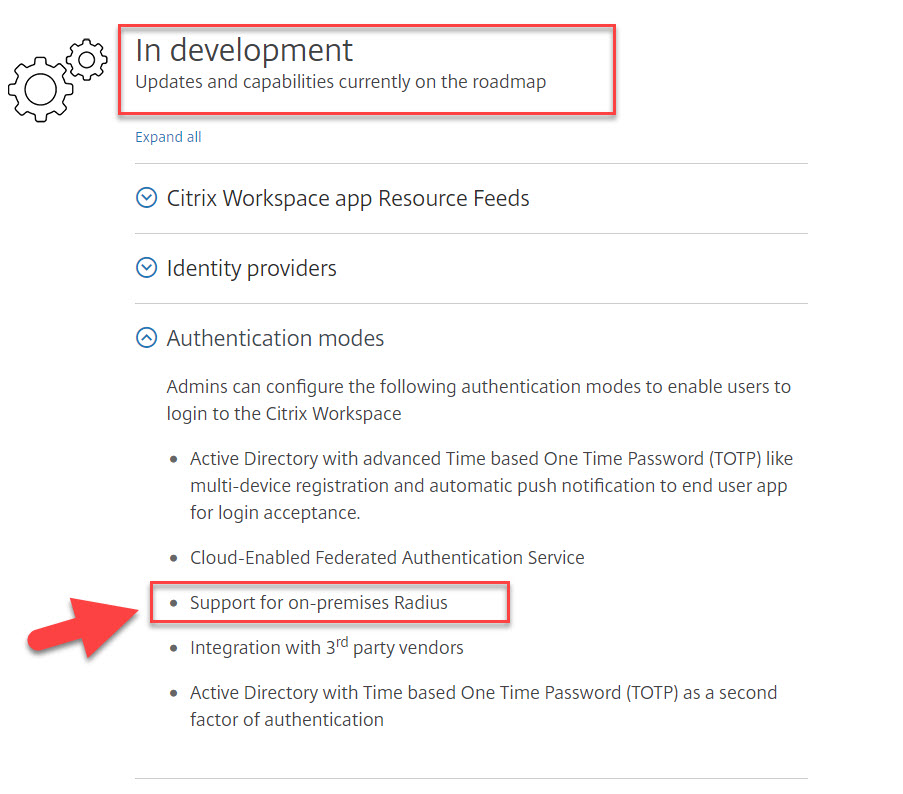 If you were at Synergy in 2018, you may have seen a cloud based TOTP solution at one of the expo booths that is built into Workspace but it has not been released yet. When this is released it will give you the ability to use a simple MFA solution as an extra layer of security if you don’t already have an existing MFA investment at your company. In that expo booth link above, I am showing pictures of the Citrix SSO app but naturally by the very nature of the TOTP algorithm RFC 6238, you can use any authenticator app your users prefer in order to authenticate with the 30-second countdown code.
If you were at Synergy in 2018, you may have seen a cloud based TOTP solution at one of the expo booths that is built into Workspace but it has not been released yet. When this is released it will give you the ability to use a simple MFA solution as an extra layer of security if you don’t already have an existing MFA investment at your company. In that expo booth link above, I am showing pictures of the Citrix SSO app but naturally by the very nature of the TOTP algorithm RFC 6238, you can use any authenticator app your users prefer in order to authenticate with the 30-second countdown code.
- They have a different cloud-based identity provider than Azure AD (examples: Okta, Ping Federate, etc). At the time of this article, Azure AD is the only 3rd party identity provider you can use. We know from https://www.citrix.com/products/citrix-workspace/roadmap.html that Okta, Google, and even setting your NetScaler as an IdP via the AAA module is in development however. The fact that Okta and Google are called out specifically leads me to believe the integration will be OIDC (OpenID Connect) based as the current Azure AD integration is. Okta has an extremely mature offering for enterprises and Google Identity Platform has a very compelling story as well. Integrating other identity providers is extremely exciting to me and often a big ask I hear from people. It would be even nice if you can use nFactor type “If This, Then That” capability to route certain sets of users to certain IdPs. Example, internal enterprise users to Azure AD but external contractors to Okta UD. And if one IdP were *knock on wood* having an outage you can fail-over between IdPs so users can still get into Workspace and work. Definitely one of my wishlist items and something I hear quite a bit in the field.
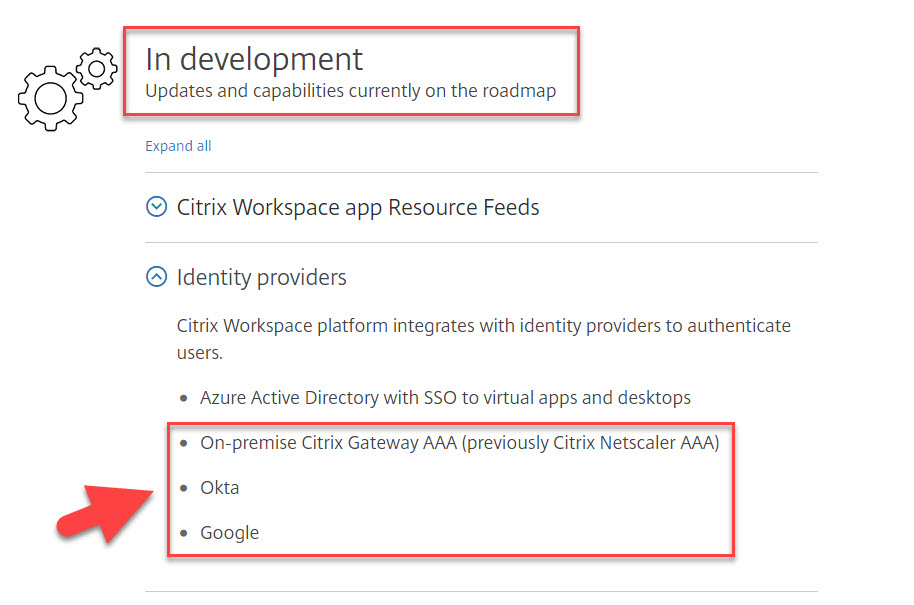
- They have a virtual or physical smart card solution (including PIV and CAC for those state and federal folks I’ve spoken with). In the above screenshot, the NetScaler AAA module integration should be able to satisfy even the requirements of my most stringent federal friends.
- They want to use nFactor as an authentication engine to intelligently route to the proper authentication mechanism and identity provider (example: Employees login against internal AD but contractors get sent to an external Okta Universal Directory to log in.)
- They have some heavy Gateway or StoreFront customizations (Example: Self-service password reset link in the footer using rewrite policy). When you move to modern auth typically the identity provider you are redirected to themselves can offer functionality like self-service password reset so this may not be a big deal for most people.
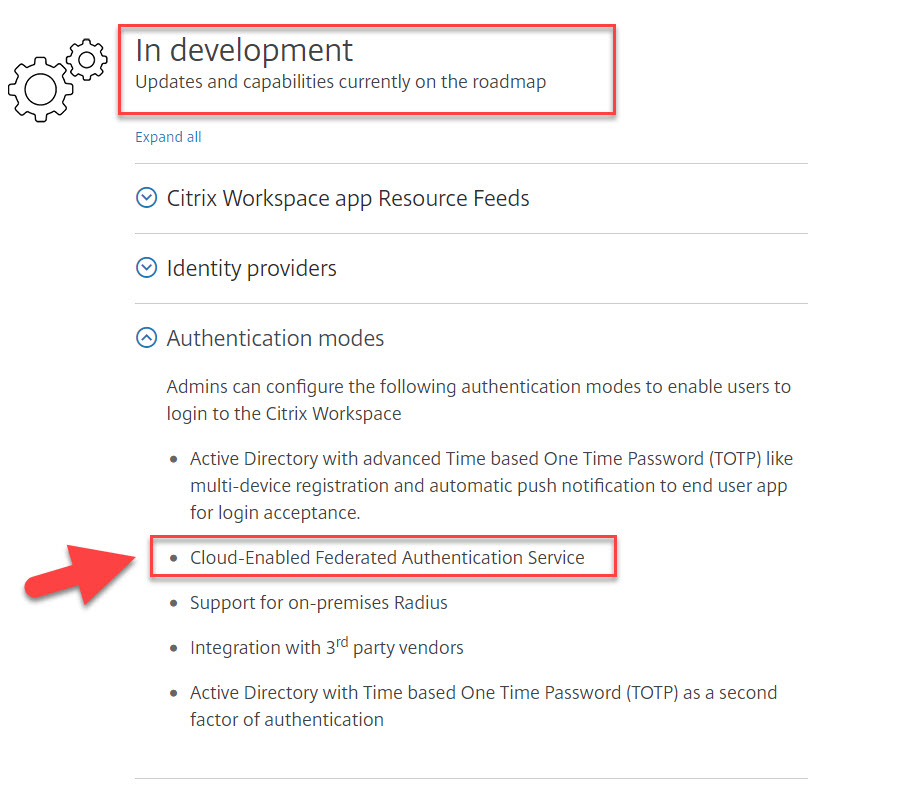
- They are using modern web-based authentication (OpenID Connect/OAuth2, SAML, etc) with Citrix FAS (Federated Authentication Service) to do SSO into their Windows Server OSes for virtual apps or Windows 10 OSes for virtual desktops. It’s critical to have FAS in place to embrace modern auth. Luckily we know from https://www.citrix.com/products/citrix-workspace/roadmap.html that cloud enabling FAS is in development:
- They want to use LHC (Local Host Cache) in the event of an Internet outage with their provider. Internal users in your main office and branches are still able to launch and consume apps from the datacenter as long as those circuits of inter-connectivity are still up and working. So with no Internet connectivity, you can still consume apps and desktops with an inaccessible control plane in Citrix Cloud with very little disruption to your business. However, I’m sure your users will know something is amiss when no external websites are coming up in their browsers! Always have multiple ISP circuits at your datacenter, but even then I’ve lived through some pretty crazy scenarios in my career where even that wasn’t enough to avoid an Internet outage. From someone losing control of a vehicle to a landscaper excavating the wrong area for a new rose bed, I can tell you some pretty interesting stories that have caused an entire datacenter to drop off the face of the Internet.
Some folks have chosen to use Workspace + Gateway Service because:
- They want a modern experience that integrates everything.
- They want a globally load balanced deployment across 12 POPs (point of presence locations) using a multi-cloud strategy (9 POPs in Azure + 3 POPs in AWS) instantly without the need to configure anything. Users will hit the nearest POP they are close to.
- Their use case is simple HDX proxy and SaaS apps only and don’t have a need for advanced ADC modules.
- They don’t want to mess with SSL certs or keep up with the latest ciphers.
- They don’t want to mess with firmware updates, testing, change management, and potential bugs.
- They don’t want to read documentation on the latest best practices and settings for HDX traffic. Did you know that for years pretty much everyone including myself has been configuring a TCP profile on NetScalers that is probably not quite the optimum config? Check out this excellent post from Juan Rivera, Citrix SVP of Cloud and Server Engineering, spreading awareness on the effects of TCP Nagle on HDX traffic. With Workspace/Gateway Service you don’t have to worry about changing things like this in response to the latest guidance and instead Citrix manages it for you:
NetScaler Gateway documentation may indicate that you should enable TCP Nagle for HDX traffic. This is incorrect, Nagle impacts user interactivity (mouse/keyboard). We are updating the documentation to avoid confusion on this.
— Juan Rivera (@juancitrix) January 10, 2019
- Their existing on premises Citrix ADC (NetScaler) appliances using Gateway functionality only are up for hardware refresh so it makes sense to move to a subscription model.
- They use Azure AD as an identity provider. Azure AD allows for Azure MFA but it can also be set to delegate authentication to on premises AD FS 3.0, AD FS 4.0, and AD FS 2019 for smartcard, PIV/CAC, or virtual smart card on TPM chip authentication, passwordless authentication with Microsoft Authenticator, or FIDO2 based auth in the form of YubiKey 5, HID Crescendo smart cards, or any number of FIDO2 compliant authentication devices which extend WebAuthn. The beauty is Workspace can consume OIDC (Open ID Connect) from Azure AD and then as most my customers like to do, delegate auth down to AD FS because they don’t want to do password hash sync. This is usually using SAML but can be configured for OAuth2 as well. I have personally configured most all of these with Workspace in Citrix Cloud and it works great. Just be wary of authentication attempts from users on very poor networks where there are packet drops as web auth is very unforgiving here and they may need to try to log in a few times in the event the assertion becomes malformed when you are delegating auth across multiple systems like this. Very rare scenarios of course but I just want to put it out there.
- Their users are fine getting a login prompt from Windows after they have launched their app or desktop. I would personally love a fully cloud based FAS “easy button” service appear in Citrix Cloud since the whole point of Citrix Cloud is to simplify infrastructure and operational overhead. I realize some customers may not like that strategy and may have a mature FAS deployment on premises they would like to use similar to how you can use on premises NetScaler or StoreFront. One thing is for sure, modern web based authentication is what many of my projects have been the past couple of years and there are no signs of this trend slowing down. The easier modern web based authentication becomes to deploy with Citrix, the better. With Windows Hello for Business gaining traction in enterprise deployments, hopefully we will see some deep integration with Citrix FAS that may even be able to utilize some capabilities here. I’ve always said to people that identity and access management is the key to enterprise mobility and that is validated every day in the projects I do.
- Gateway Service has a very simple way of onboarding SaaS apps. Its template driven so makes it easy to add SSO or just a simple bookmark for a SaaS website. The templates feel a lot like Okta Integration Network (OIN) in my opinion. It would be nice if Okta customers that already have a very large investment in it can simply feed all these SaaS apps they spent time configuring already into Workspace itself. That would be my dream since I really love the simplicity of Okta as do many of my customers.
- They want to prepare to extend Windows Virtual Desktop (WVD). I’m under NDA with both Microsoft and Citrix so until WVD Public Preview is released I can’t share much publicly. But what we can infer from the roadmap at https://www.citrix.com/products/citrix-workspace/roadmap.html is that Citrix Workspace can extend WVD as a resource feed. Another great feature of feeds that I’ve been asked about is bringing VMware Horizon into the Workspace experience. I have quite a few customers with both CVAD and Horizon deployed side by side for different business units based on whatever the need was at that time. These customers are starting to realize user experience is import and want one common secure launcher for apps and desktops from any remoting protocol and delivery platform. I’m happy to see that is also in development. It will be interesting to see how this list of integration points grows over time:
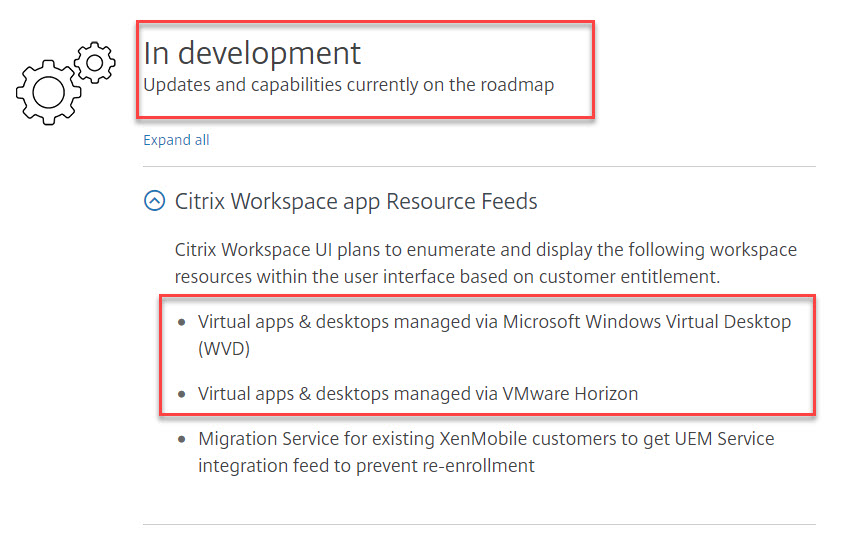
I can’t make a blanket statement on what is right for your company. You have to analyze your needs and pick the solution that best fits. Some of my customers are anti-cloud anything (at least at this given point in time in their journey) so they choose to keep everything on prem. Most of them are in a transitionary period migrating their Citrix control plane to the cloud however so as part of this, their access and enumeration are either on prem or cloud based depending on their needs I outlined above.
I can tell you that many anti-cloud customers are now moving to a Citrix Cloud based control plane versus continuing to build out on premises or in Azure IaaS. I remember in 2017 the majority of my projects were building the traditional on-prem Citrix control plane with only a few moving to Citrix Cloud. In 2018 things, progressed very quickly and Epic has authorized the use of a Citrix Cloud Virtual Apps and Desktop Service based control plane so hospital systems started coming to me in droves asking how to simplify their environments. Citrix Cloud is also certified to run in Azure Gov so federal customers are also asking for advice on how to migrate. Going back through my 2018 project list this weekend to reflect, the majority of my projects in 2018 were Citrix Cloud CVAD Service based vs. traditional on-prem. In 2019, I expect this kind of momentum to continue in the projects I am asked to help with.
So how well does this new stuff work in the real world?
I always tell people I live in a virtual desktop all day, every day. Last year I completely migrated off of on-prem StoreFront and NetScaler Gateway to cloud based Workspace and Gateway Service. I wanted to be able to better deploy it as well as consume the user experience fully. After all, I’d be a horrible architect if I didn’t consume the very things I built and be happy with the results. If I don’t like something, chances are my users won’t either. The biggest take away that may impact the user experience is that your HDX proxy traffic will always go out to the Internet, yes even for internal users. Internal and external users are all treated the same way in this regard. So even if the VDA is in your building and the user is sitting on the same floor, that HDX traffic is going out of your organization over the Internet to the nearest Gateway Sevice POP and back in via a Cloud Connector to display the session from the VDA (aka traffic hairpin). Besides needing to do a little fine tuning of your HDX policy in Studio (more on that coming up, keep reading), everything has worked very well for me from every location I’ve been to both inside and outside the country since last year. Here’s an example from just the other week:
- I’m on a flight with my iPad sitting on the tray table watching a movie I had pre-downloaded with Netflix before my trip. I’m usually so busy on the ground this is about the only time I can catch up on movies without interruption. 🙂 I realize I needed to check on something back in Houston and send an urgent email out before I land. I pay for the in-flight WiFi on my iPad and realize it’s super slow. I’m somewhere north of Phoenix at this point:
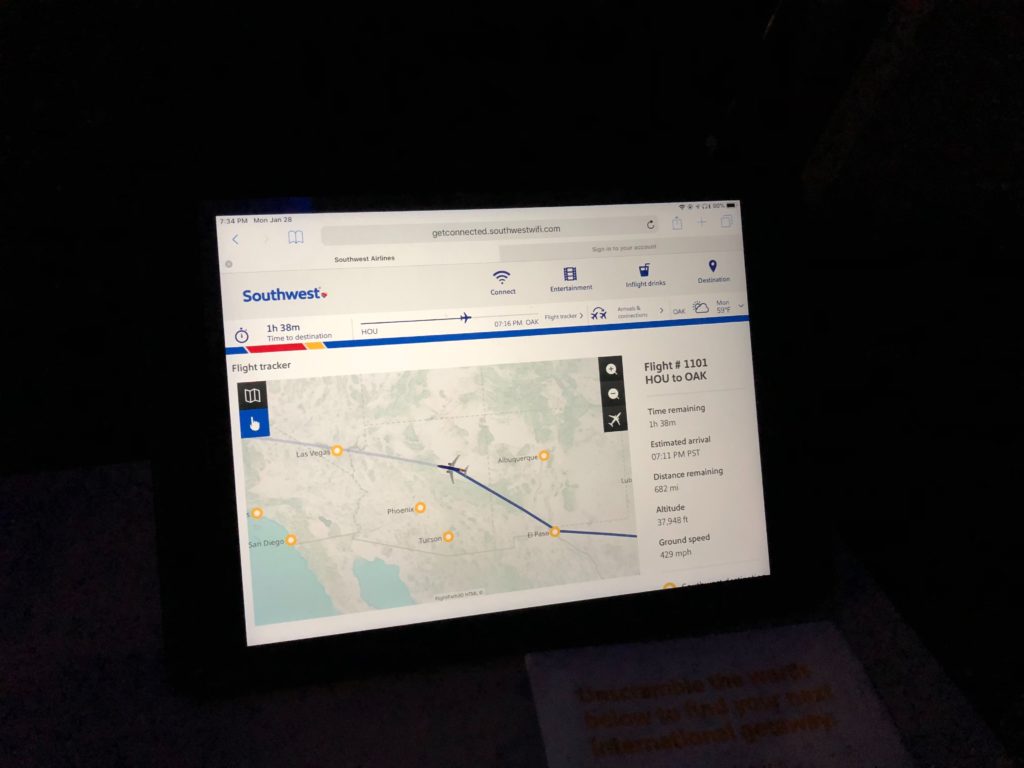
- I open my Workspace app integrated with Azure AD and Azure MFA. I didn’t want to spend another $8 to get WiFi on my phone just for a push notification so decided to use the TOTP code displayed in the Microsoft Authenticator app in my phone instead:
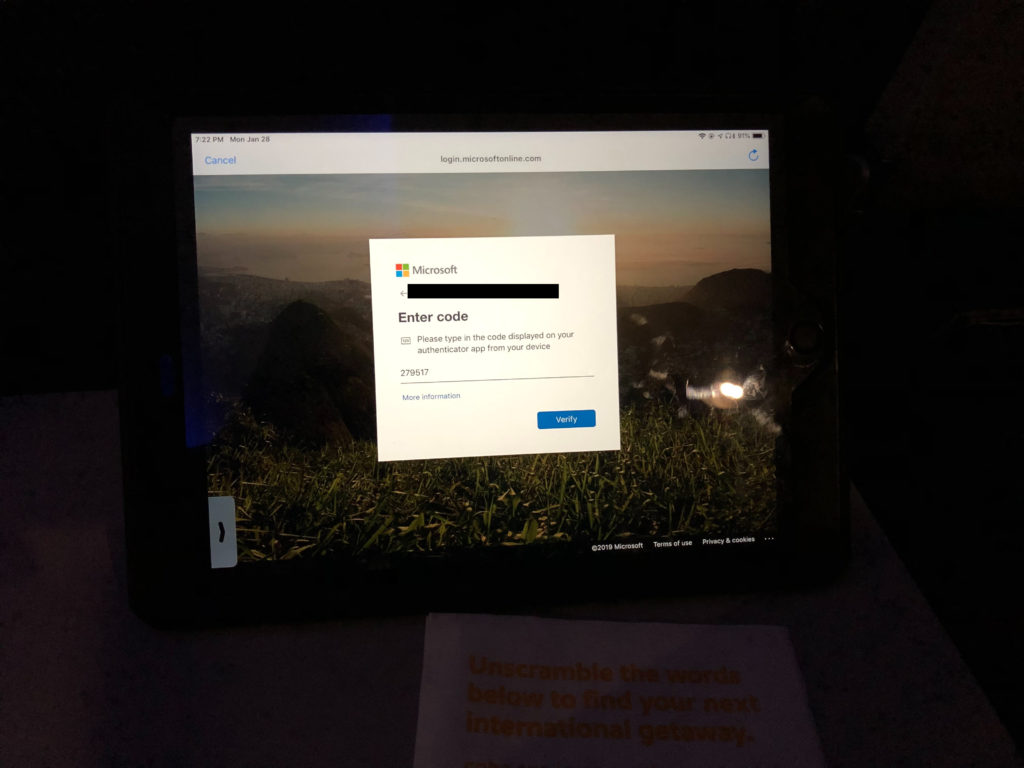
- Post auth, here comes Workspace! Ahh the benefits of modern authentication.
- Let’s get that Virtual Desktop launched shall we?
- Voila, Windows 10 virtual desktop running in my datacenter back in Houston but delivered via Workspace in Citrix Cloud at whichever of the 12 Gateway Service POPs (9 in Azure, 3 in AWS) that was closest to me at that time all the way down to my iPad:
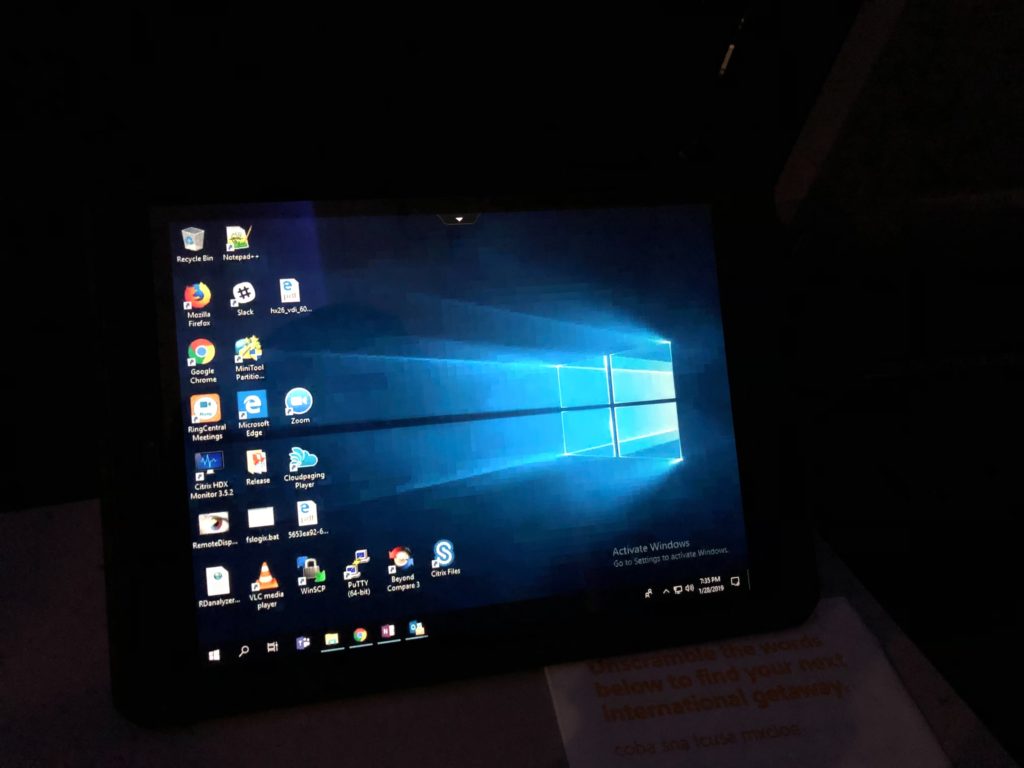
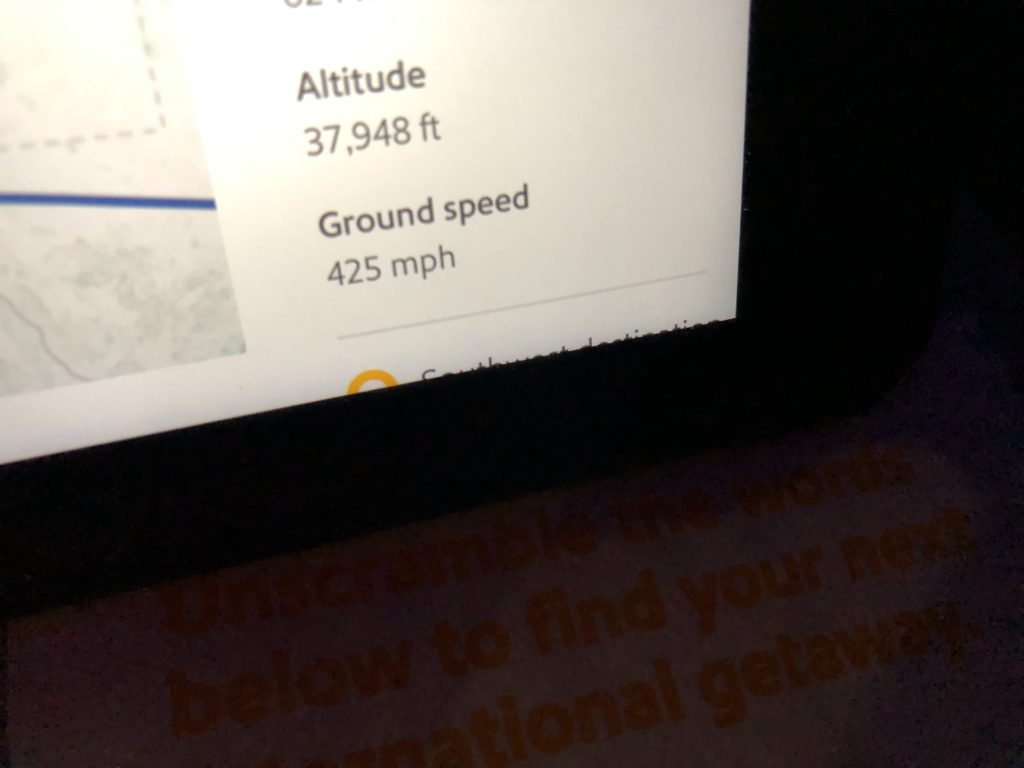
- Even at almost 38,000 feet traveling at 425 miles per hour on a very slow in-flight WiFi I have a pretty good user experience with my Windows 10 virtual desktop. I just picked up exactly where I left off at the office when I locked my physical desktop and left to go to the airport!
Are there ways to make performance even better?
Yes! Here’s a trick I discovered for better performance with Workspace last year:
When using #CitrixGateway Service in #CitrixCloud, how many people have enabled the “Very High Definition User Experience” HDX policy template? The performance difference vs. default policy is remarkable and with very little bandwidth increase in my testing.
— Jason Samuel (@_JasonSamuel) September 28, 2018
I have seen a great deal of success with Workspace and Gateway Service in many customers with this HDX policy template enabled so highly recommend you test it out for your environment and see if you have similar results. Without this enabled, I have seen pixelation artifacts, banding, and degraded visualization of the virtual desktop session at times. For some users in some verticals that is acceptable but let’s say for example in a medical setting, it may be a very unacceptable experience to the end user. You can’t really control every network hop between you and the nearest Gateway Service POP so if there’s a spike in latency due to some external factor and you are choking bandwidth using a restrictive HDX policy, the impact will be felt by your users. Once enabling the Very High Definition User Experience HDX policy the session feels very close to the same experience as you would get proxying ICA traffic through an on-prem NetScaler Gateway. I suspect once Workspace/Gateway Service supports EDT it can even perform better.
Another point I want to make is to be wary of VPNs and web proxies. In some companies, users have been instructed to use VPN when out of the office so it’s second nature to them. Or they simply don’t have a choice and VPN is in an “always-on” mode with their company devices. In this scenario, the VPN Admins must enable split tunneling with Gateway Service POP destined traffic or it won’t work well. Users will be routed incorrectly and suffer a very poor remote streaming experience of their HDX sessions, files will be slow to access, things enumerate slowly, etc. Think of like like Office 365 and Microsoft’s recommendation to enable split tunneling for this traffic. Don’t even route it over ExpressRoute, the recommendation is to route directly out to the Internet as the O365 services were designed to work. Workspace and Gateway Service must be treated the same way in order for your users to have a functional user experience. Whitelist traffic on web proxies and don’t attempt to decrypt and re-encrypt this SSL traffic as it will completely break the user sessions. Citrix Analytics offers all the visibility you need into user sessions, behavior, and traffic analysis within the Citrix ecosystem. It can interface directly with your company’s SIEM or Microsoft Security Graph and provide this data without breaking the user’s session. The use of CASBs (cloud access security brokers) like Netskope that are designed to work with Citrix Cloud based services is also something some of my customers are doing successfully.
The other thing I’ve seen a lot of success with my virtual desktop is enabling Browser Content Redirection (BCR). That way if you are looking at a YouTube video it leverages your host PC rather than stress the virtual desktop resources, kind of like the old Flash redirection days. I use it with Chrome browser and it works great. Just remember though that if you are signed into let’s say Google in your virtual desktop, when you load YouTube in a new tab it won’t carry that session sign-in over to YouTube as it’s really being rendered from your local PC. Therefore you will need to sign-in to YouTube separately within that tab in this example. Another item you will notice is that browser content blockers you may have installed within the virtual desktop browser have no effect on ads. They will be shown and not blocked since everything on the YouTube.com page is coming from the physical desktop, not just the video like the old Flash redirection days. Most companies block ads at the network level anyhow so this might not be a problem but I want to draw awareness to this if there are some browser add-ons your users use that need to interact with the page. Citrix recently released the 2.0 version of BCR and you can read about it more here from Fernando Klurfan, the Principal Product Manager for HDX: https://www.citrix.com/blogs/2018/12/12/browser-content-redirection-2-0-will-help-you-maximize-your-multimedia/. Sneaky Citrix, releasing stuff in December when everyone’s on vacation. I did not have a chance to test out all the new improvements in depth yet. I was quite happy with the 1.0 version so far. Just wish it didn’t need that Chrome browser extension though. The less things I have to manage in my images the better. I remember when Fernando first explained how BCR works and convinced me to deploy it, I told him I wish I could go back in time and enable this on all my projects from the past few years! 🙂 It seriously makes multimedia in a virtual desktop exceptional and aligns to what a user’s expectation should be, that it is no different from using a physical desktop.
Anyhow this weekend as I was wrapping up this article I decided what the heck, let me quickly update my VDA and test out this BCR 2.0 functionality. I downloaded the 1811 VDA and installed it in my image. While downloading it from citrix.com and installing it into my image I thought to myself, why isn’t this easier where cloud based Citrix Studio can tell me when my VDAs are out of date and I can update the VDA in my master images from there with a push? Think VMware Tools and how VCSA and VUM manage things. That way its kind of staring at me in the face that I’m missing functionality I probably want for my users and Studio encourages me to keep my VDAs up to date. Definitely a wish list item.
After the update, my experience with BCR 2.0 has been very positive so far. It’s only been a weekend so time will tell how big a leap ahead it is over the 1.0 version. The “Browser Content Redirection Authentication Sites” policy is something I started working with this weekend and am still testing out on different sites. Websites that are rendering using redirection but completely decoupled from authentication is very interesting to me and what I have tried so far seems to be working well.
There is also the new HDX Adaptive Throughput feature which I just started testing with this VDA update. All it requires is to just update your VDA to 1811 and be on the latest Workspace app to test: https://www.citrix.com/blogs/2018/12/17/turbo-charging-ica-part-2/. The article does not state anything at all about CVAD Service, only on-prem CVAD. I reached out to Miguel Contreras, the author of the article and Product Manager on the HDX team last week and he confirmed it will work with CVAD Service as well. The benefits listed in the article lead me to believe this should make my virtual desktop experience even better than with the policy I have enabled. Since I’ve been home all weekend I haven’t really stressed it but first impressions are everything seems to be running well. Hopefully, over the next few weeks, I’ll have an answer to how much of an improvement there is as I travel and jump on some spotty WiFi networks.
What to expect in the future
I think Citrix will be investing even more into the Workspace and Gateway Service in the coming year. You’ve seen the roadmap screenshots above and there’s a lot of work already in progress. In addition to this, I think there will be a lot of work done in the areas of speed and resiliency around the delivery protocols when used with these services as even more people transition. The expectation from people I talk to is that it needs to work the same or better than on-prem and so far it’s very close to feature parity with on-prem in my opinion. Even beyond on-prem in some areas. It will be a very interesting year ahead!
If you want to try out any of the functionality I spoke about above yourself without impacting your current production environment, you can start a trial on any Citrix Cloud service you like including Workspace and Gateway Service. Here is some info to read over on how to do it: https://docs.citrix.com/en-us/citrix-cloud/overview/citrix-cloud-service-trials.html. I always encourage people to learn new skills. Even if your company is not currently looking at it, it is worth your time to improve your understanding of how new technology works and what you may be expected to deploy in the future for your company. Hope this info has helped you and please leave a comment below if you have any questions or would like to share your own experiences.
Jason Samuel is a visionary product leader and trusted advisor with a proven track record of shaping strategy and driving technology innovation. With extensive expertise in enterprise end-user computing, security, cloud, automation, and virtualization technologies, Jason has become a globally recognized authority in the IT industry. His career spans consulting for hundreds of Fortune 500 enterprises across diverse business sectors worldwide, delivering cutting-edge digital solutions from Citrix, Microsoft, VMware, Amazon, Google, and NVIDIA that seamlessly balance security with exceptional user experiences.
Jason’s leadership is amplified by his dedication to knowledge-sharing as an author, speaker, podcaster, and mentor within the global IT and technology community. Recognized with numerous prestigious awards, Jason’s contributions underscore his commitment to advancing technology and empowering organizations to achieve transformative results. Follow him on LinkedIn.





Bart Jacobs
February 12, 2019 at 5:21 AM
Jason, great write-up as usual.
I do have one question: what about the Gateway connector? And the Cloud Connector vs Gateway Connector question?
Jason Samuel
February 12, 2019 at 9:33 AM
Thanks Bart!
The Cloud Connector is software that goes on a Windows server and runs as a service. It check in with the Citrix Cloud based control plane and is used for AD enumeration, Studio being able to talk down to on prem VDAs to publish things, and HDX proxy traffic. Your VDAs are pointed at these rather than traditional Delivery Controllers. It is a critical component for CVAD Service.
The Gateway Connector is a newer component and is an appliance based on Citrix ADC code that gets imported to your hypervisor. It allows you to deliver internal websites through Workspace currently.
Daureo Silva
March 24, 2019 at 1:25 AM
Excellent article!
I do have a question though: currently we use Citrix Cloud based control plane + Azure and although we have Citrix Gateway Service and Citrix Workspace enabled, we are still relying on StoreFront+Netscaler Gateway on-prem. We are about to move subscription on Azure and I would love to get rid of the on-prem and go full Cloud. So I wonder, if I move all my resources to the new subscription but Store Front and Netscaler Gateway, Workspace and and NG as service would take over seamlessly?
Thanks!
Jason Samuel
March 24, 2019 at 12:03 PM
Hi Daureo, yes that is easy to do. Go to your Citrix Cloud Console > Workspace Configuration > Access tab > External Connectivity. You just change the Connectivity Type from Traditional Gateway to Gateway Service for your Resource Locations, takes just minutes to do. At that point, your users will get the new Workspace experience and will be coming in through the Gateway Service.
Jay
May 24, 2019 at 9:20 PM
Hi Jason, great article and thanks. I have few questions:
1. In Citrix Cloud, when I am setting a Access, under External Connectivity, I choose my Resource location and there is an option called Internal Access Only, I am trying to understand what it does functionality wise. If I use Internal Access, users would still connect to virtual apps and desktops via Internet only, correct?
2. For my case users can connect to closet POP is Singapore and that is 6000 KM away and users are sharing 8Mpbs link only using gateway as a service, not use how user experience is going to be like and require further testing. In that case should I recommend them to use Netscaler as a service or should we configure MPLS and have Citrix Netscaler VPX on Prem?
3. Do you have some examples of HDX policy you recommend for the users using POP over 6000 KMs and over 8Mps shared link only?
Thanks so much Jason
Jason Samuel
May 29, 2019 at 11:16 AM
Hi Jay,
1. Internal Only should not be used in most cases. Use the Gateway Service option. Here is more info on this: https://docs.citrix.com/en-us/citrix-cloud/workspaces/add-on-premises-site.html#task-3-configure-connectivity-and-confirm-settings
2. There are now Gateway Service POPs in South Africa North and South India Azure regions. This was announced just last week at Synergy and they are live. I would recommend trying Gateway Service over deploying NetScalers if you can. If you need a closer Azure or AWS region, let me know and I will send that feedback to Citrix product managers.
3. I recommend starting with the “Very High Definition User Experience” HDX policy template and working backwards from that. That HDX policy seems to give the best user experience. With just an 8 Mbps link you will need to tune down some settings in this policy to account for user load.
Jay
May 29, 2019 at 8:05 PM
Hi Jason,
Thanks so much for reply. Really helpful. Yes it will be good to have POP close to Manila Philippines. Most of our users are based in Manila and using heavy business applications. The closet Pop for them is Singapore and that is about 5 and half thousand KM away.
Since many organization are having their team based in Philippines, it would be great to have Azure or AWS region in Manila. Please send the feedback to Citrix Product Manager.
Thanks again for your reply.
Jay
Ctxldy
July 1, 2019 at 10:45 PM
Jason — Great write-up! I’ve definitely seen more interest in Citrix Cloud over the last 6 months but I wanted to ask a question — I thought there used to be an option to use an “on prem” NetScaler which could really be hosted in a public cloud for that matter in conjunction with the Workspace service (as opposed to on prem Storefront). Is this no longer an option? I can find older documentation that seems to reference it but the options don’t appear any longer in Citrix Cloud. Thoughts??
Richard
September 26, 2019 at 4:51 AM
Hi Jason,
Can Workspace aggregate with Storefront on-prem? The customer I am working with have been advised by Citrix to not use the NetScaler Gateway Service to maintain on-prem MFA with DUO.
Also can Controllers still be On-Prem or is this no longer required as the Cloud Connector has a LHC?
Andreas
September 26, 2019 at 5:27 AM
Hi Jason,
we also made a few tests with Citrix Gateway service and we mentioned, that Adaptive Transport does not work, we can’t establish a HDX connection to our workers using UDP. Do you know if this “by design” or are there additione proxy and firewall settings to implement? Usind Workspace with our on-prem ADC, UDP works fine.
Kind regards from Switzerland,
Andreas
Jason Samuel
September 26, 2019 at 2:37 PM
@Ctxldy, You can use NetScaler + StoreFront hosted on-prem or in a public cloud like Azure, AWS, GCP, etc. This is for both traffic and app launching so Workspace would not be used. Now a new feature has been released that allows you to use your on-prem or public cloud NetScaler for authentication only while using the cloud-based Workspace for traffic and app launching. This is the better approach because it gives you all the benefits of Workspace.
@Andreas, That is correct. EDT/HDX Adaptive Transport over UDP is not available with Workspace right now. Only with NetScaler + StoreFront currently. It will be coming to Workspace at some point. I am awaiting this feature as well for some of my customers.
Jason Samuel
September 26, 2019 at 2:40 PM
@Richard, Workspace can aggregate on-prem delivery controllers. You can decom StoreFront, it is not needed anymore. If the customer wants on-prem MFA with Duo just add their NetScaler as the authentication option for Workspace and they can then use DUO. Delivery Controllers are not needed at all if using CVAD Service, just the Cloud Connectors.
ctxfan
December 10, 2019 at 12:33 PM
Hi Jason — great article! Quick question – is the 1 GB limit per user based on a monthly cumulative?So if a user consumes 500 Kbps during their 8 hour session x 5 days per week = 2.5 Mbps x 4 weeks = 10 Mbps for the month. Does that sound right? Any suggestions for calculating existing usage without HDX Insight/MAS?
Thanks!
Jason Samuel
December 11, 2019 at 8:25 PM
@ctxfan, Thank you. I have not seen any limits being enforced, documentation, or even visibility of this traffic to the admin after deploying it in many large environments. Newer docs don’t even talk about bandwidth limits anymore. I would check with your Citrix account team to get direction on it. Personally, I don’t factor this in with my deployments at this time.
jigna
March 10, 2020 at 2:26 PM
Hi Jason, can you get away with just using workspace configuration and not the gateway service? that way decommission onprem storefront and netscalers? If so, does just using workspace url and not gateway service just keep you from globally deploying or configuring the workspace url from different pops?
Jason Samuel
March 11, 2020 at 12:13 AM
@jigna, Workspace and Gateway Service come together as one solution. Just sign up and start using it. Once you have cut over your users to the new yourcompany.cloud.com URL, you can then decom your on-prem StoreFront and NetScalers.
jigna
March 11, 2020 at 8:34 AM
Thanks I have virtual apps and desktop service, i thought gateway service was an additional cost
Jason Samuel
March 11, 2020 at 5:57 PM
@jigna, the CVAD Service you are subscribed to comes with Workspace and Gateway Service. There is no additional cost. There is no actual admin facing configuration in Citrix Cloud for Gateway Service. It’s just there and always running in front of Workspace by default transparently. When you use yourcompany.cloud.com and launch an app or desktop, you are by default routing through the Gateway Service to launch that session.
Ray Davis
January 1, 2022 at 8:00 AM
This doc is older but still has a lot of good information for people that are in the conversation phase of the differences. I think the biggest problem is many folks take the on premises knowledge and try to use it within the CVAD services. The configuration is much simpler and many of us are used to deep configuration. Nice write still after many years.
Happy new year as well.
WD
January 13, 2022 at 9:46 AM
Hello Jason,
We are running into challenges with users through the Gateway service in Calgary Canada. The closest pop is 2200 miles and latency is in the high 100 ms. In this use case, users in Calgary are connecting to Remote PCs through our colo in Calgary, but to do so, they are connecting through Cali POP. Are there plans for a closer POP? Alternatively, is there way to use our on premise ADC to proxy the ICA connection just for these users, but leave the rest going through the Gateway Service?