It’s finally here! Full Windows SSO (single sign-on) with Windows virtual apps and virtual desktops through Citrix Workspace when using modern web authentication like Azure AD and modern access management like password-less phone sign-in with Microsoft Authenticator over the HDX remoting protocol! I know that’s a mouthful so an easier way to say it, ultra-secure user logins for your enterprise with an amazingly fast login experience your users will love, it almost feels like cheating. 🙂
I’ve written about using Citrix FAS (Federated Authentication Service) with SAML and OIDC (OpenID Connect) in the past but it was always with on-prem StoreFront and Citrix Gateway (previously Citrix NetScaler Gateway). In a nutshell, Citrix FAS is a middle-man that helps take modern web auth and convert it to an authentication method that the Windows operating system understands (short-lived certificates from your Microsoft CA that mimics a smartcard login). It almost acts as a “virtual smartcard service” in a way generating smartcards on the fly to help with Windows SSO when coming in over a remoting protocol like HDX.
For people that wanted to use Citrix Workspace which is the evolution of StoreFront, whenever you launch a Windows desktop or server OS session, it would always prompt you for an additional login from Windows itself. This was always a suboptimal experience. There was no way to get around it and FAS could not be wired up to Workspace. Until now!
With this new capability, you can now take your on-prem or cloud IaaS deployed FAS environment and make it talk to Workspace. This capability is part of the Citrix Identity Platform (CIP). CIP is a core piece of Citrix Cloud control plane and uses Microsoft Azure Service Fabric, you can read more about it here: https://customers.microsoft.com/en-us/story/citrix-cloud-streamlines-with-single-sign-on-access-based-on-azure-service-fabric. Now when users launch a virtual app or virtual desktop, they will have a seamless single sign-on experience and never see a Windows login prompt!
This highly anticipated feature is now in Private Preview with Public Preview coming soon. Big thanks to Oscar Day, Product Manager at Citrix focusing on Identity and Authentication, for letting me test this capability so early and share this information with the community as an early sneak peek! Please note, this is Private Preview meaning things can change by the time of Public Preview and General Availability of this capability. If there are any major changes to the setup at those points in time, I will update this guide. Granted it works so well currently, I don’t think there will be many changes. 🙂
Enable FAS with Citrix Cloud based Workspace
1. Log into Citrix Cloud and hit the hamburger icon (3 lines) in the top left:
2. Click on Workspace Configuration:
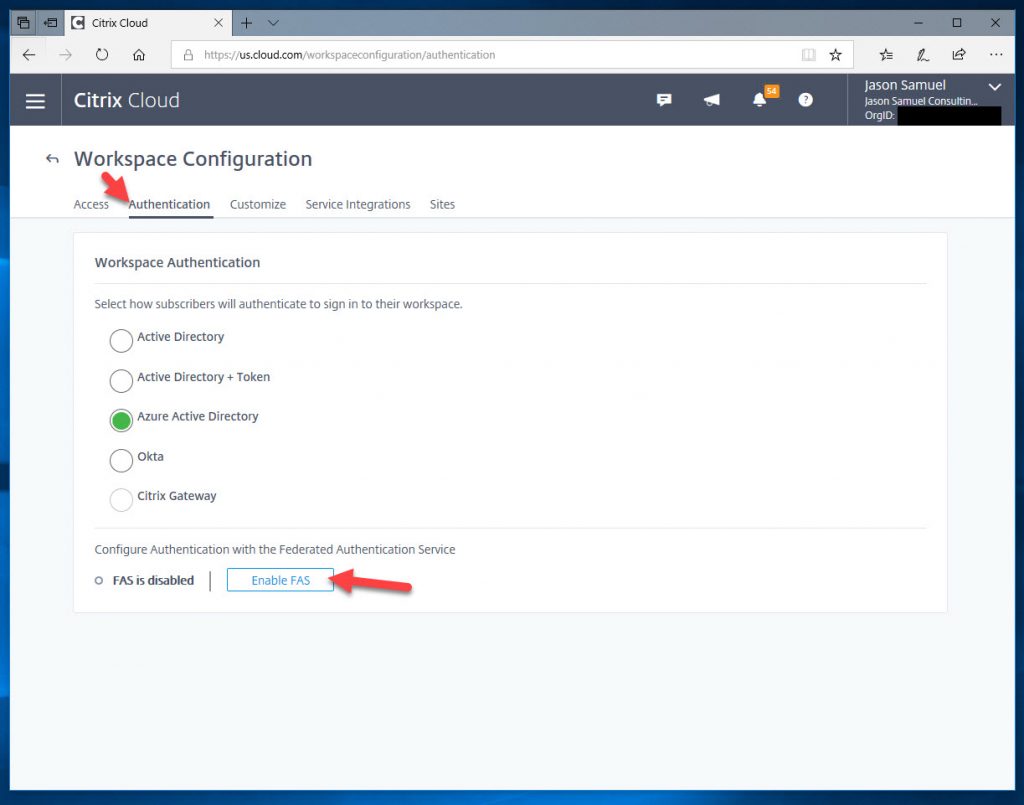
3. Click the Authentication tab and you will see a new option saying “Configure Authentication with the Federated Authentication Service”. It will say “FAS is disabled”. Click the “Enable FAS” button:
4. It will then have a green dot and say “FAS is enabled”:

5. Now click the hamburger icon (3 lines) and click on Resource Locations:
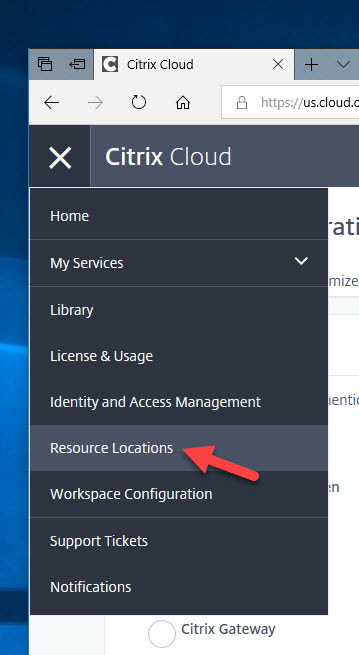
6. Under your Resource Location (your various datacenters or public cloud IaaS regions), you will see an option to add FAS Servers. Click on the plus button:
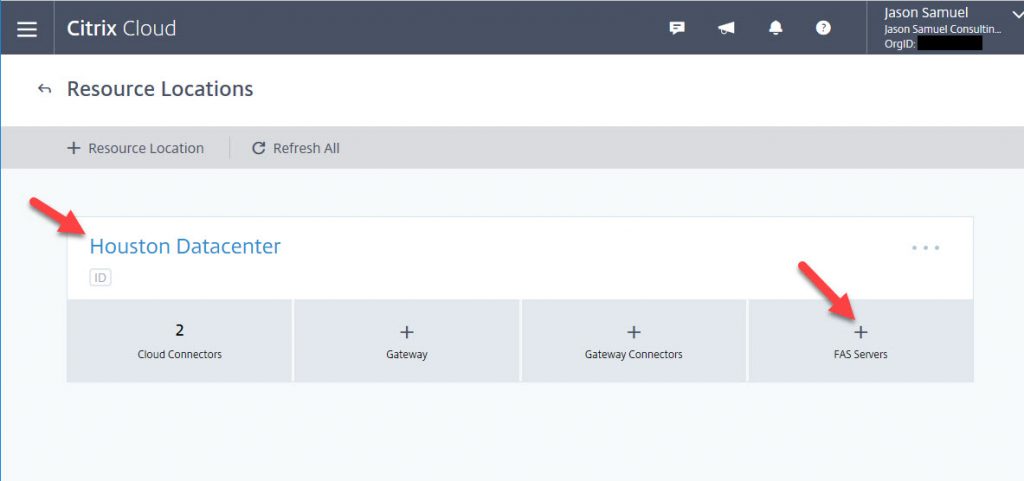
7. You will get a pop-up window giving you the ability to download FAS. This is a new version of FAS that can talk to Citrix Cloud. If you have an existing FAS environment, you can simply run this executable on your FAS servers and upgrade them this way. I will show you how to install and configure FAS as if were brand new to your enviornment in this guide.
Setup Citrix FAS for Citrix Cloud
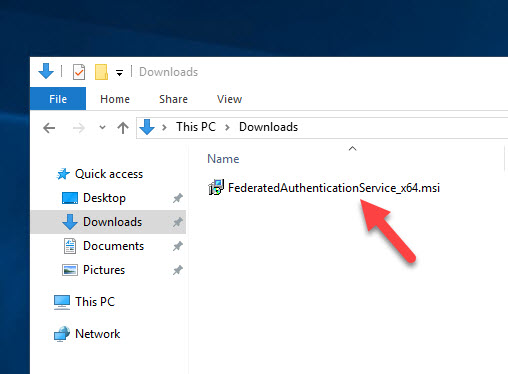
8. Log into a Server 2016 or Server 2019 VM in your datacenter or public cloud IaaS region in this particular Resource Location. Ensure it is a brand new clean server with no other things installed on it. Then copy over and double click the “FederatedAuthenticationService_x64.msi” file you just downloaded. It’s tiny at under 6 MB:
9. You may get this message saying .NET Framework 4.7.1 or higher is not installed:
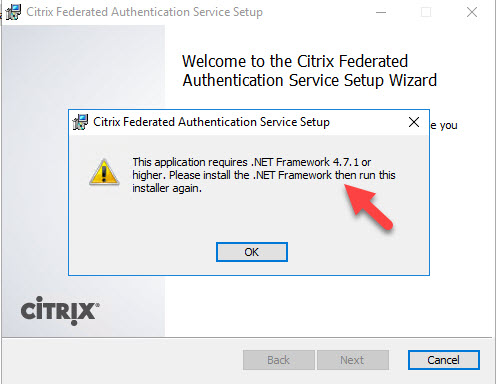
10. Go to https://go.microsoft.com/fwlink/?linkid=2088631 and download and install .NET Framework 4.8 which is the most recent version. This link is for the .NET Framework 4.8 Offline Installer so is a little larger at 70 MB:
11. Now re-run the FAS installer. Hit Next:

12. Accept the EULA and hit Next:

13. Hit Next on the Configure Windows Firewall screen:
Configure Citrix FAS for Citrix Cloud
16. And now you get to see Citrix FAS with its new makeover design. 🙂 Now even though I’m setting up a new FAS server from scratch for you, I’m using my existing Microsft CA I had previously done a FAS deployment on. So the necessary certificate templates are in AD and CA authorization template publishing is already complete. The FAS installer saw that and has green check marks next to these options. If you don’t see green check marks, click the “Deploy” and “Publish” options to run through those options. If you run into issues, look through my previous FAS install guide. You may also notice that the admin console was opened without an elevated prompt. If you see this, just close the console and re-open elevated. Update: As pointed out by David in the comments, you can just click the blue link as well and it will re-open FAS elevated:

17. Find it in the Start menu and use the “Run as administrator” option:
18. Now that message will be gone. Ensure you spend a few minutes to run through the Deploy and Publish steps first, then hit Authorize:
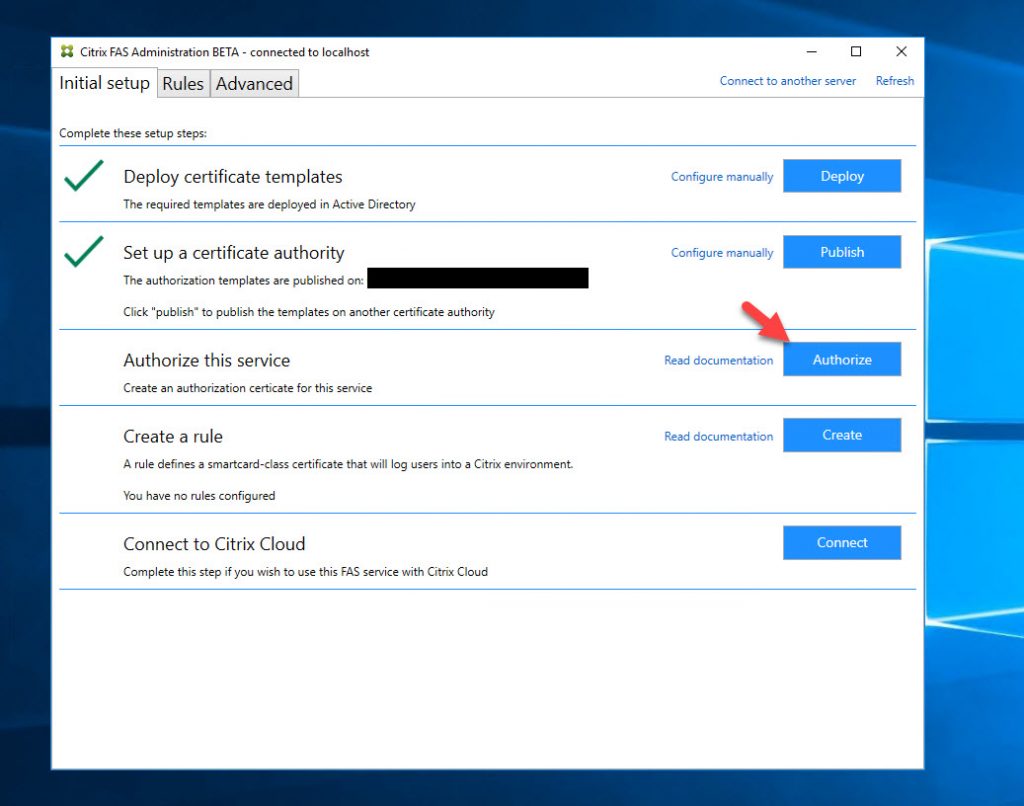
19. Click OK and this new FAS server will start talking to your Microsoft CA:
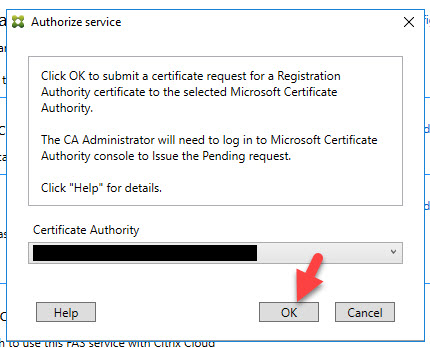
20. It will start spinning and say there is a pending authorization request on your CA:
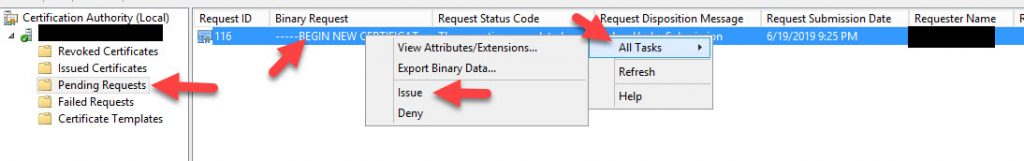
21. Log into that CA, open the Certificate Authority console > Pending Requests > right click on the request from your new FAS server > All Tasks > Issue:
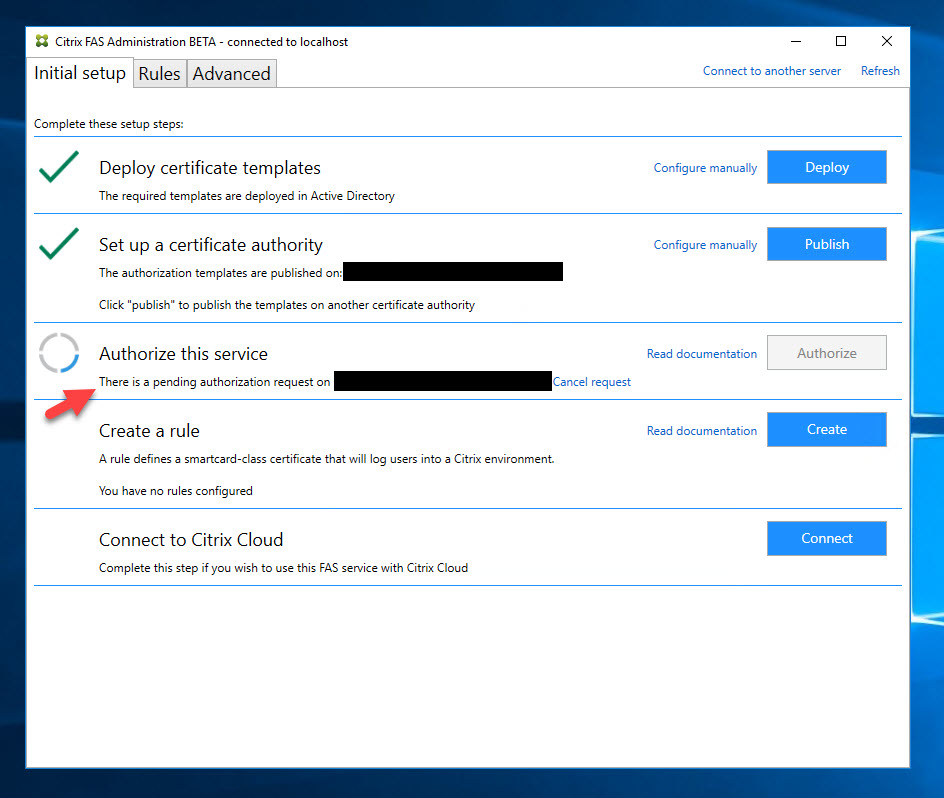
22. Now go back to your FAS server and within seconds it will go green with a checkmark:
23. The Create button can be used to create a rule to define the smartcard-class certificate that users will use to log into the Citrix environment when using an on-prem StoreFront environment or Citrix Cloud-based Workspace. If you would like to use StoreFront and Workspace in parallel for migration purposes, then you can go ahead and set up the rule now. I will skip it since this is a new FAS server and I’m only intending to use it with Citrix Workspace. Later on in another step, we will create this:
24. Now the fun part and something new for FAS. The “Connect to Citrix Cloud” option! Click Connect:
25. Click “Sign in to Citrix Cloud”:

26. IE or whatever default browser you have set will pop up asking you to log in. Go ahead and log in with your Citrix Cloud credentials:
27. Choose your Account Name and the Resource Location (the on-prem datacenter or public cloud IaaS region) that this FAS server will reside in:
28. You will get a message saying the FAS server has been added to the Resource Location you chose. Close this window.

29. The FAS installer will also say it has authenticated to Citrix Cloud. Go ahead and hit Next:
30. I didn’t have a rule created before. So I will switch the radio button to “Create a new rule when this wizard finishes” and click Next:
32. Now the Create a Rule wizard will pop up. Just hit Next to create a default rule:
33. Choose the “Citrix_SmartcardLogon (recommended)” template and hit Next:
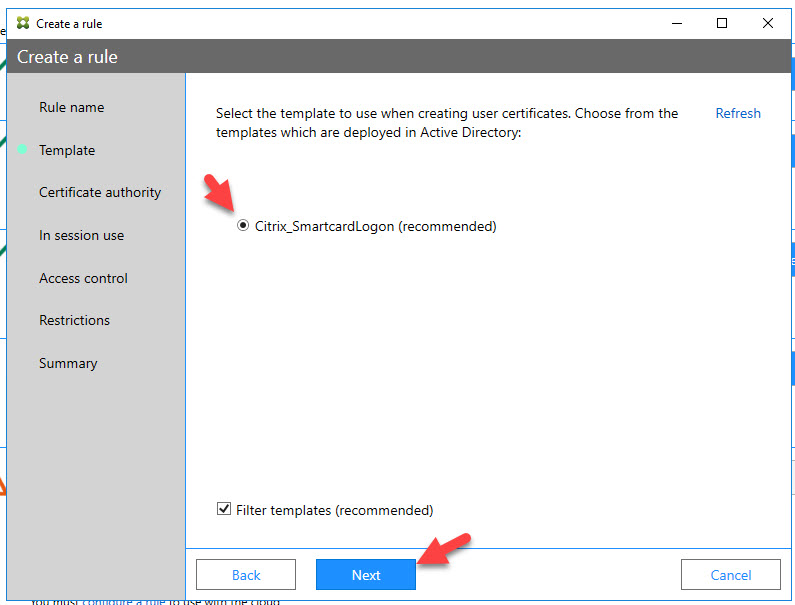
34. Select your CA and hit Next:
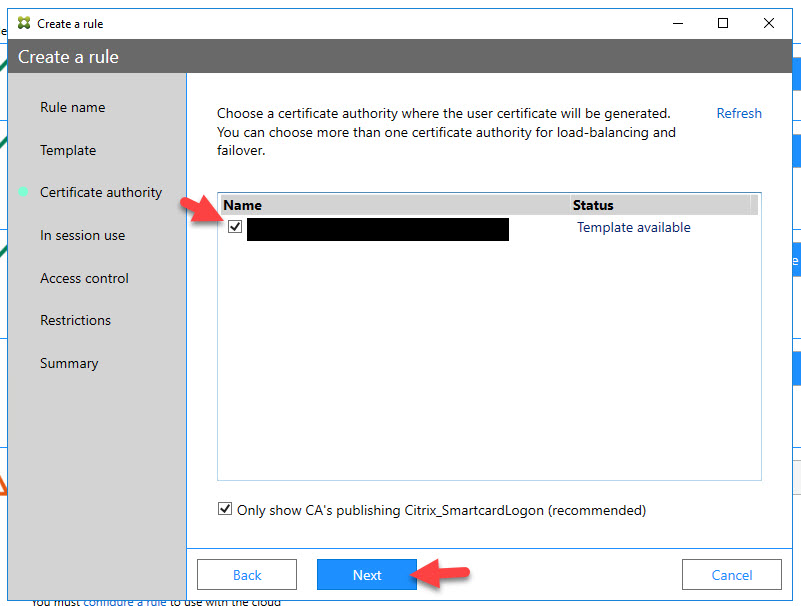
35. Check “Allow in-session use” and hit Next:
36. If you are going to use this FAS server with both StoreFront and Workspace, this is where you would grant access to StoreFront. I am not and will only be using this with Workspace so I am just going to hit Next here:

37. Click Next on the Restrictions section:

38. Hit Create
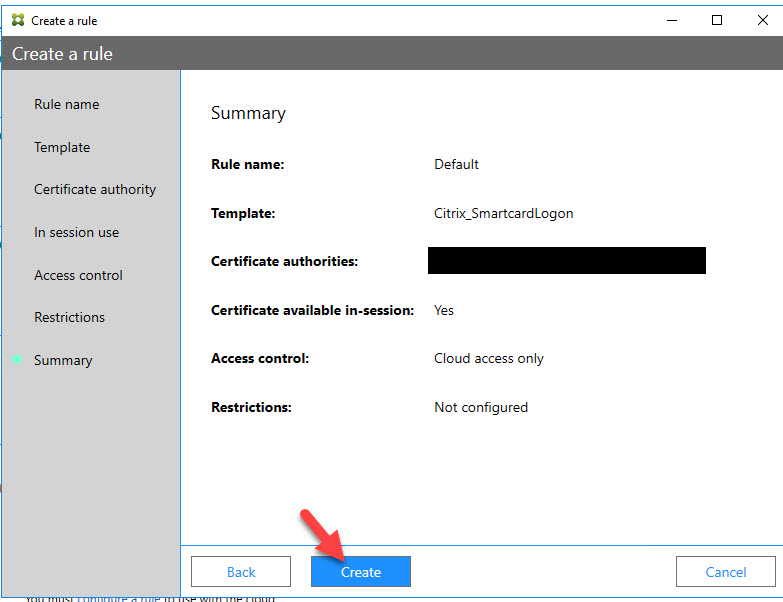
39. You may get an error message saying “Connected to the cloud but NOT available for use” like this. This is because we need to configure GPO to allow the VDAs. Click that link for instructions on how to configure your GPO and doing a “gpupdate /force” on your FAS servers once they are part of this GPO. Don’t forget to ensure this new FAS server you are standing up has been moved into an OU that is getting this GPO. If you already have a GPO for an existing FAS deployment, it may go green immediately and you do not need to run through this step:

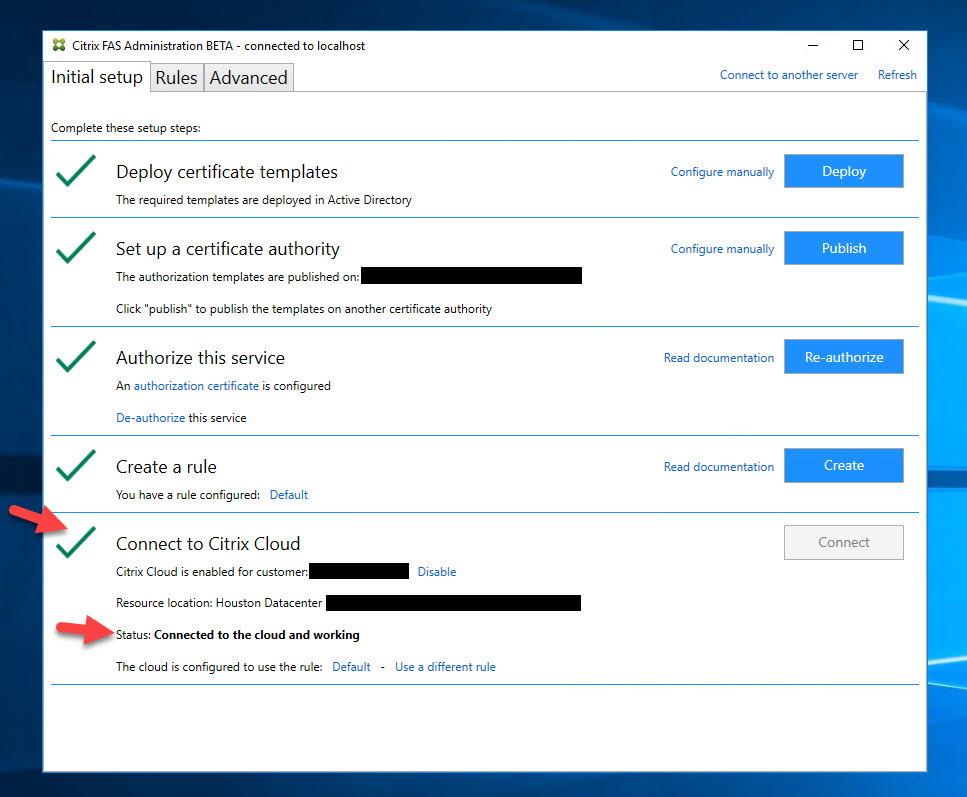
40. Now you will see a green check mark next to the “Connect to Citrix Cloud” option and it will say the current status is “Connected to the cloud and working”.

41. If you go back to Citrix Cloud and drill down to the FAS section of your Resource Location, you will notice the server is there and healthy now. It may warn you that you need 2 FAS servers. You should always have at least 2 FAS servers per Resource Location but for this guide, I am going to leave it at 1 for now and will add the 2nd server later.
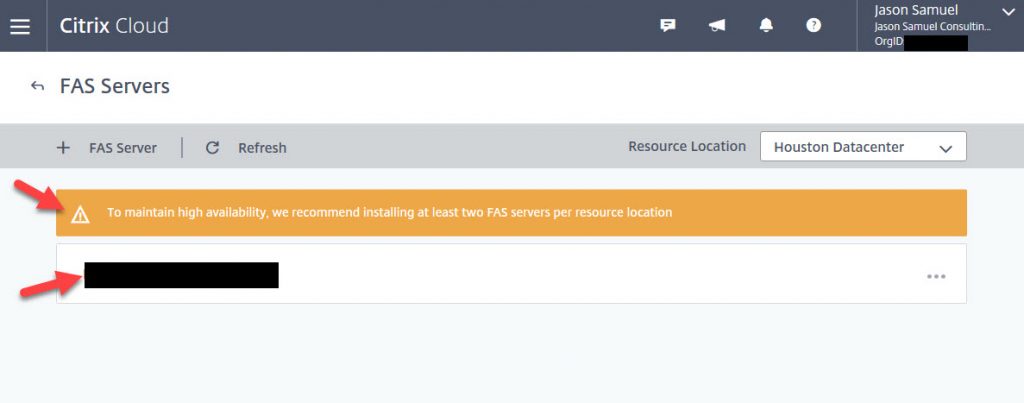
Using Citrix FAS with Microsoft Azure AD password-less authentication and Windows SSO in Citrix Workspace
42. Now navigate to your Citrix Workspace URL. You can use a web browser or Workspace app here if you wish, both will work identically. I use both personally with cloud enabled FAS but will use a browser for this example:
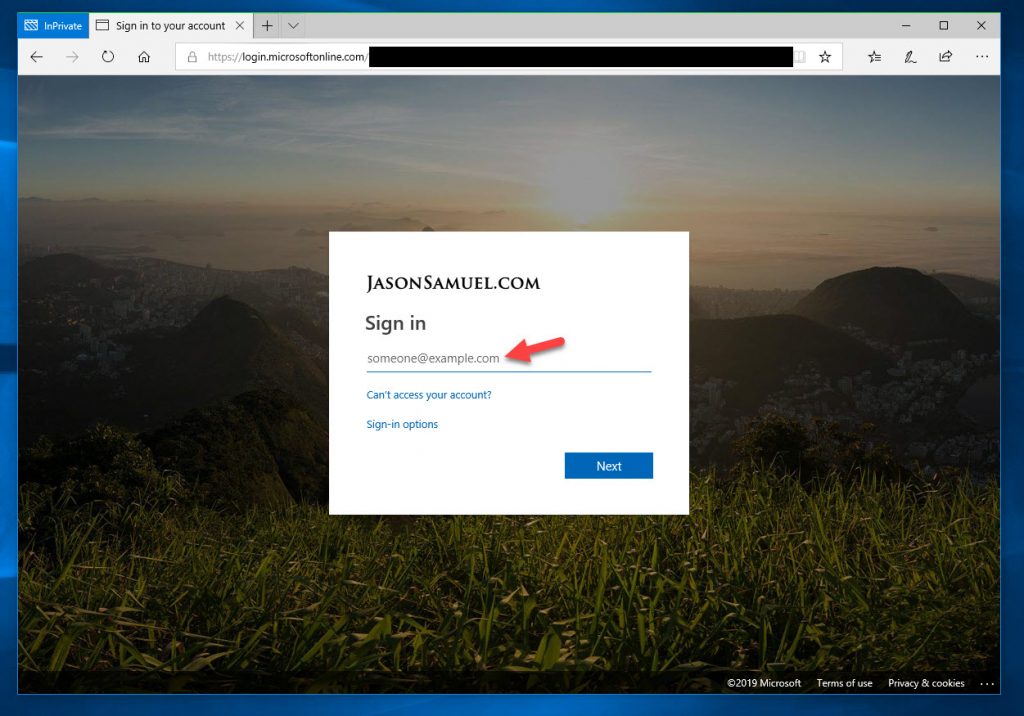
43. If you are using Azure AD like I am, you will see the Azure AD login page. Enter your email address (UPN) and hit continue:
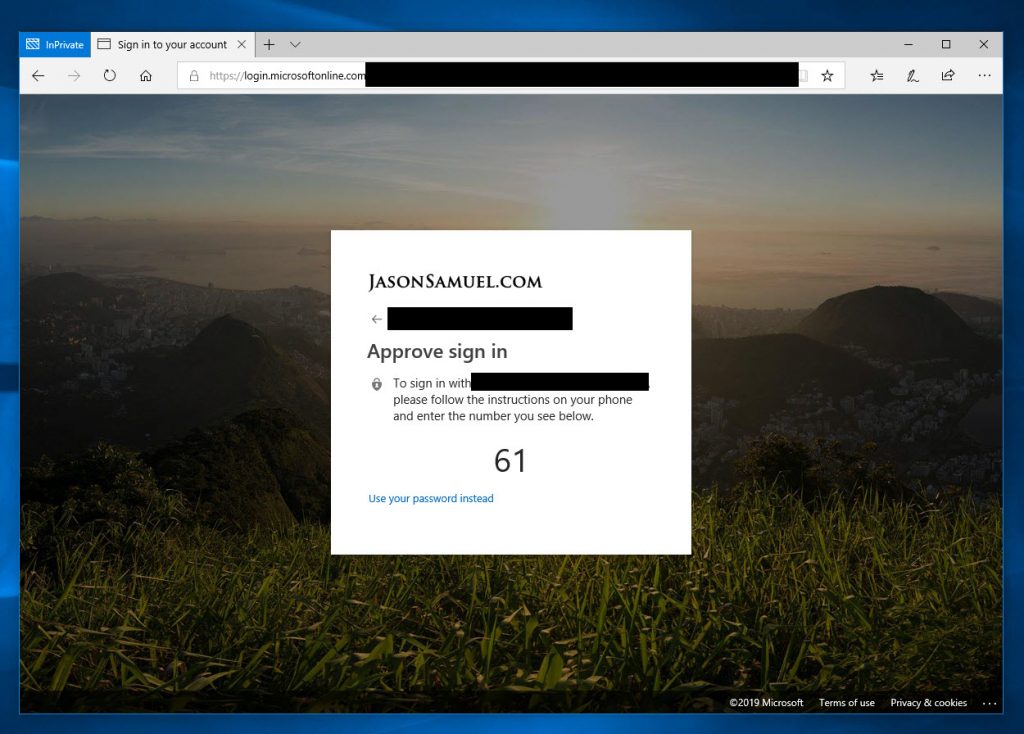
44. I am using password-less phone-sign with Microsoft Authenticator so I won’t even use a password to log into Workspace. I get a number match like below I use with Microsoft Authenticator on my phone as the 1st factor and use a biometric on my phone as the 2nd factor. If you want to know more about how to set this up in your Azure AD tenant check out my How to setup password-less phone sign-in authentication with Microsoft Authenticator, Azure AD, and Citrix Workspace guide:
45. Once I’ve completed my password-less authentication, I will now launch a virtual desktop:
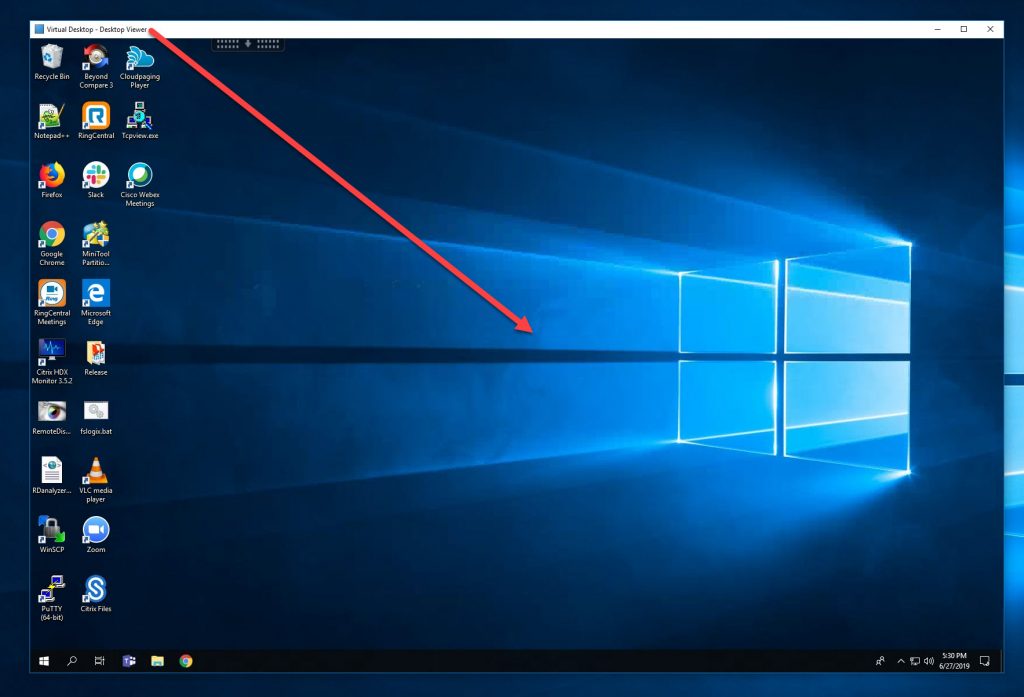
46. And there you go! 🙂 No Windows login screen. It will single sign-on right into the virtual desktop or virtual app. In this example, the virtual desktop I just launched has completed SSO and just sits at the desktop ready for me to get to work:
Verifying FAS, CA, and VDA are all working as expected
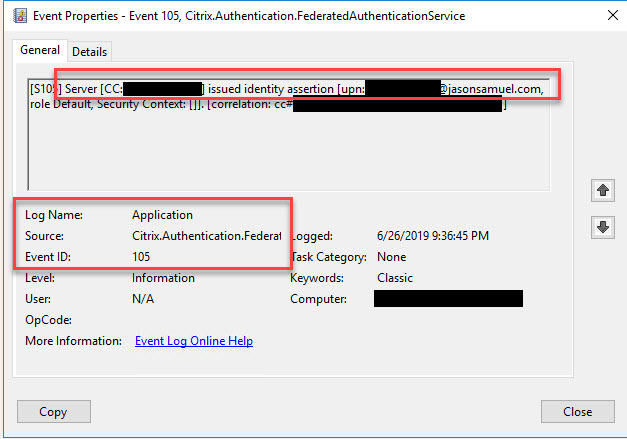
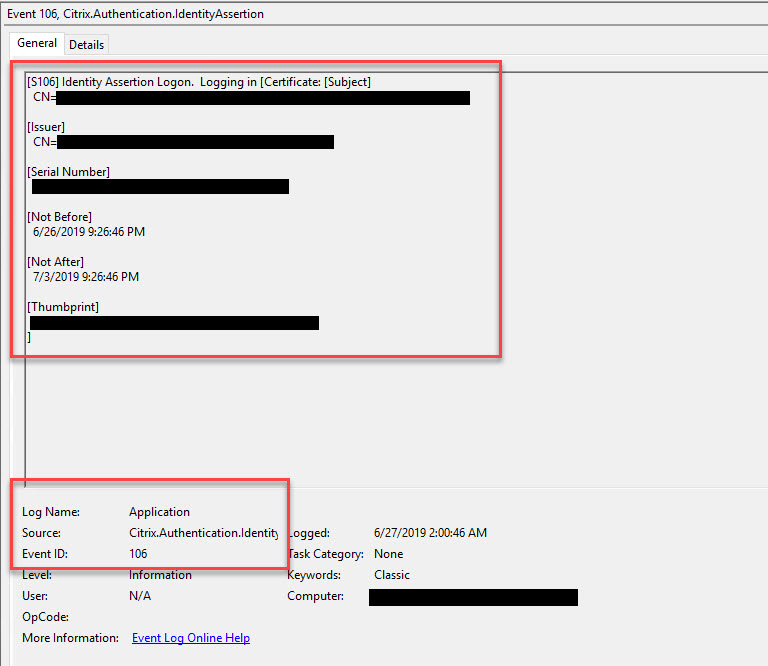
47. In your FAS server Windows Application event log, you will see Event ID 105, 120, 121, and 204 showing the user sign-in process. You will also see the cert being issued on your CA server. Lastly, on the Windows endpoint you are logging into (the VDA), you will see an Event ID 106 showing the user sign-in.
Event ID 105 – Identity assertion from Citrix Workspace and CIP for the user from your Citrix Cloud tenant:
Event ID 120 – Certificate issuance begins for the user:

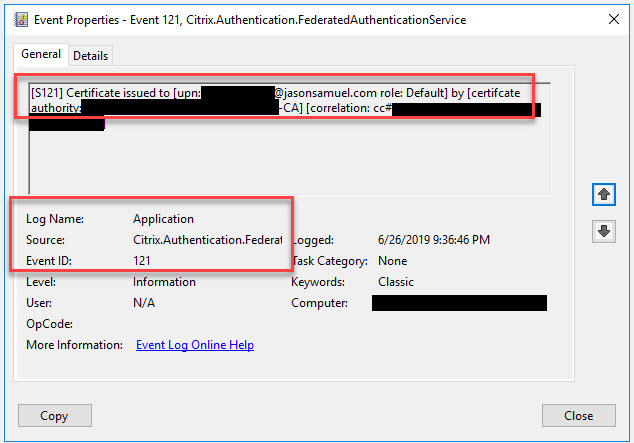
Event ID 121 – Certificate is issued by the Windows Certificate Authority (CA) for the user:
Event ID 204 – The relying party (the Windows VDA) uses the certificate to complete Windows single sign-on for the user as authorized by Citrix Workspace and CIP in your Citrix Cloud tenant. If you are using in-session certificate use in your FAS GPO you may see more than one 204 event from the VDA:
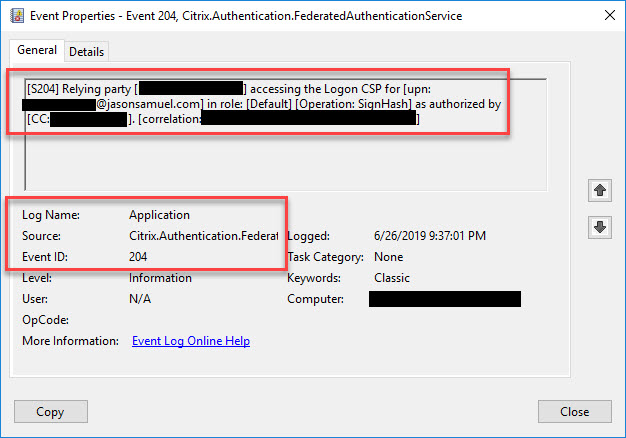
Issued Certificate – On your CA server under the Certificate Authority console > Issued Certificates node, you will see a short-lived cert with a 7-day default expiration issued for the user ID using the Citrix_SmartcardLogon certificate template:
![]()
Event ID 106 – On your VDA, in this case a Windows 10 virtual desktop, you will see the certificate from the CA that was issued for the user is being used for single sign-on everytime the user launches the virtual desktop through Workspace:
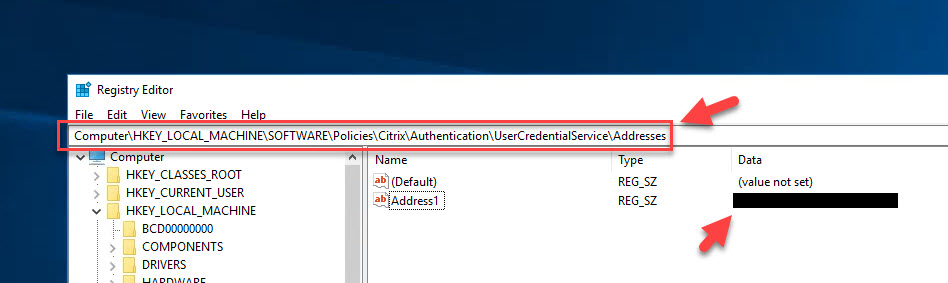
Windows Registry – You can also check your VDA’s registry to verify it is getting the group policy telling it to use FAS under:
|
1 |
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Citrix\Authentication\UserCredentialService\Addresses |
and
|
1 |
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Policies\Citrix\Authentication\UserCredentialService\Addresses |
You will see the name of your FAS server(s) listed like this in both registry locations:
Common Issues, Troubleshooting, and Resolutions
48. There are a few things to be pro-active on with a FAS deployment to ensure users have a good SSO experience. Monitor your event logs for the following event IDs:
Event ID 19 on Domain Controller – If some users see a “The request is not supported” message during Windows SSO:
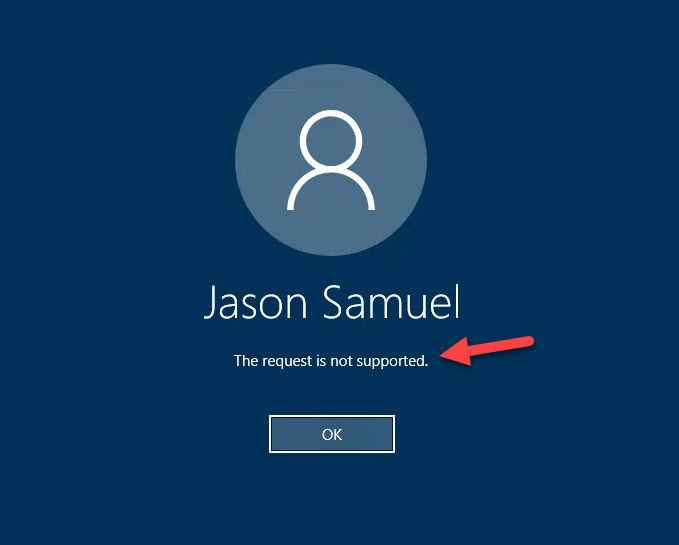
this is because the Domain Controller the VDA hit during logon does not have a Domain Controller Authentication certificate on it for the CA that is issuing certs for the user. This usually happens when you bring up new CAs for FAS but the DCs aren’t aware of them. If you go to the Event Viewer on the Domain Controller you will see an Event ID 19 error in the System event log from the Kerberos-Key-Distribution-Center saying “This event indicates an attempt was made to use smartcard logon, but the KDC is unable to use the PKINIT protocol because it is missing a suitable certificate.”
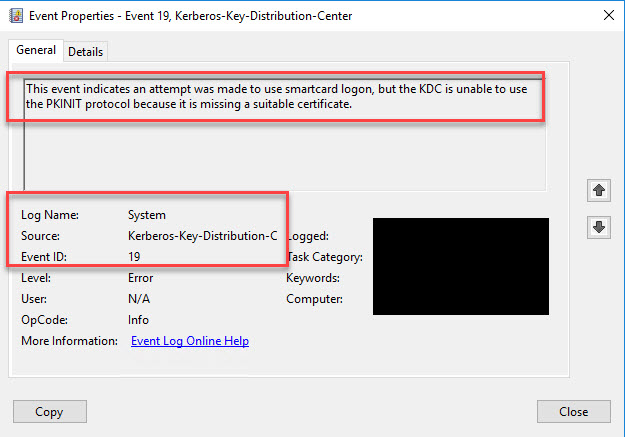
The more DCs and FAS servers you have, the easier it is to overlook this so ensure you check for this during deployment and setup monitoring for this proactively.
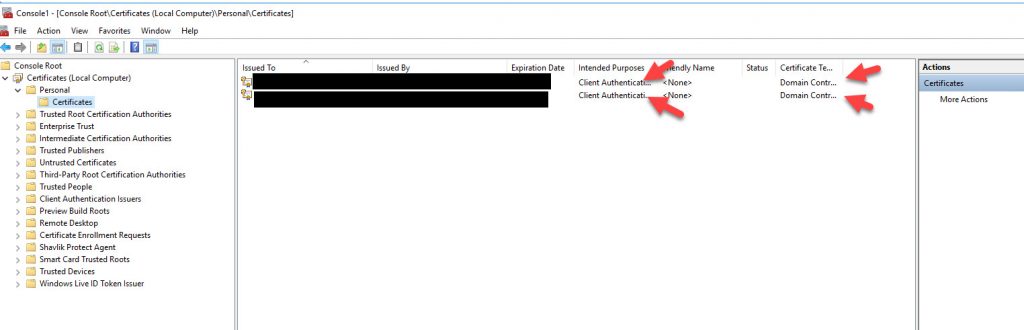
The resolution is logging into your Domain Controller and opening the Certificates MMC. Drill down into Certificates (Local Computer) > Personal > Certificates. One of your CA servers could be missing like in this example:
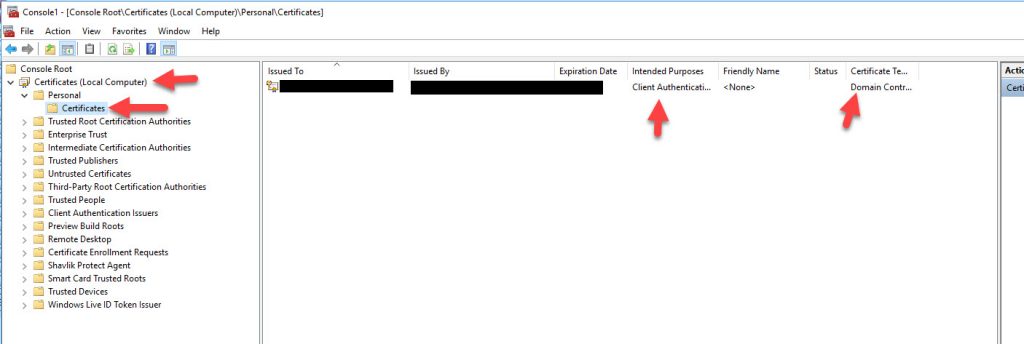
Just right click on Personal > All Tasks > Request New Certificate…

Hit Next to begin certificate enrollment:
Hit Next for the Certificate Enrollment Policy:

Hit the checkmark next to Domain Controller Authentication and press Enroll. You can click on details if you want to check or un-check specific CAs in your environment as the enrollment server:
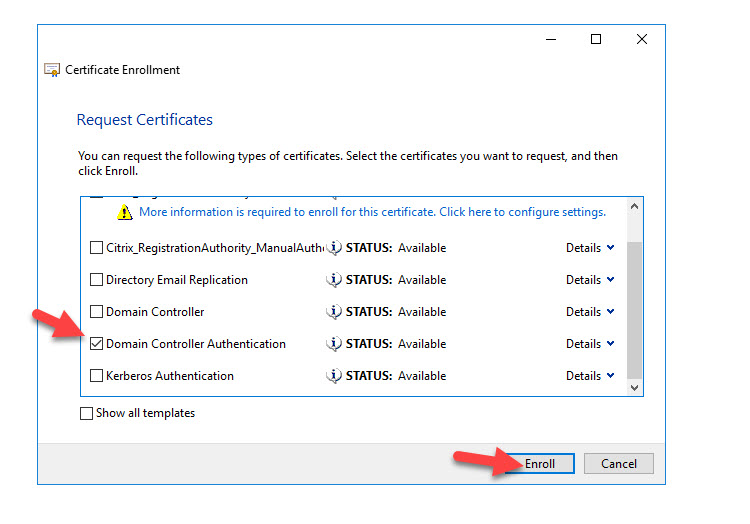
In this example, I will leave both CAs checkmarked:
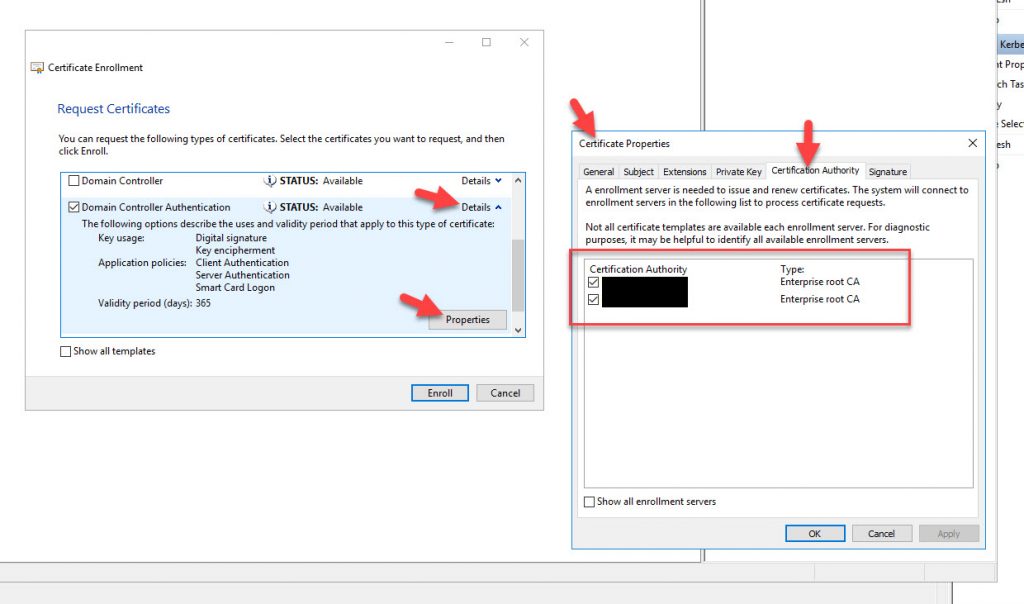
It will say “Succeeded” and the validity period for the certificate is 365 days. Now press Finish.
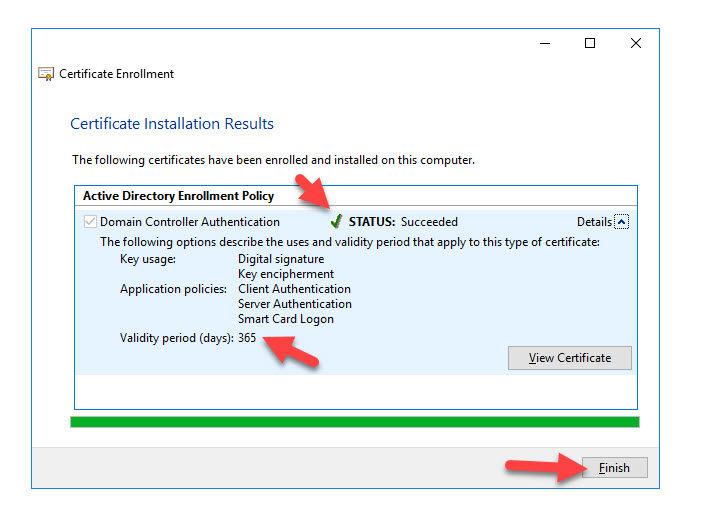
Now you will see all your CAs (Issued By column) with certificates issued to the DC you are on (Issued To column). Now your users will no longer see the “The request is not supported” error message and can complete Windows SSO successfully.
Final Thoughts
I hope this sneak peek of Citrix Cloud enabled FAS helps you plan your upcoming deployments with Citrix Workspace. As you saw, it’s quite simple to set up and configure. Public Preview is coming soon and I can tell you, this a highly anticipated feature for Citrix and they welcome feedback. Follow me on Twitter and I’ll post as soon as it goes Public Preview. A big thanks to Oscar and team for getting this feature delivered and for letting me take it for a spin. If you have any questions or comments please leave them below.
Jason Samuel is a visionary product leader and trusted advisor with a proven track record of shaping strategy and driving technology innovation. With extensive expertise in enterprise end-user computing, security, cloud, automation, and virtualization technologies, Jason has become a globally recognized authority in the IT industry. His career spans consulting for hundreds of Fortune 500 enterprises across diverse business sectors worldwide, delivering cutting-edge digital solutions from Citrix, Microsoft, VMware, Amazon, Google, and NVIDIA that seamlessly balance security with exceptional user experiences.
Jason’s leadership is amplified by his dedication to knowledge-sharing as an author, speaker, podcaster, and mentor within the global IT and technology community. Recognized with numerous prestigious awards, Jason’s contributions underscore his commitment to advancing technology and empowering organizations to achieve transformative results. Follow him on LinkedIn.






Vincent
July 2, 2019 at 5:42 PM
Hello Jason
Wow i have been waiting for this option for a while.
Great article.
David Williams
July 5, 2019 at 7:37 AM
Hi, just wanted to say that “Run this program as administrator” is actually a clickable link which will restart the FAS admin console as admin, so you don’t need to relaunch it.
Jason Samuel
July 8, 2019 at 8:06 AM
Thanks David! Good catch, will update the guide.
Oliver Wöll
September 23, 2019 at 12:30 PM
Hi Jason,
great article!
I have just activated the cloud FAS option from Citrix support, but I was not able to download the installation file for the FAS server. The link to the download directs to Citrix root website.
What I am doing wrong?
Regards
Oliver Wöll
Adam
October 29, 2019 at 12:02 AM
Is this feature available for GA? I talked to Citrix support and they said it’s still in Beta
Jason Samuel
November 6, 2019 at 10:55 AM
Correct, it’s not GA yet.
Dominik Szymanski
November 26, 2019 at 11:36 AM
Dear Jason,
really great article! This is what we have searched for.
Are there any updates regarding availability of this feature for
public? Is it possible to activate this feature right now for our citrix Workspace tenant?
Best regards
Dominik
Jason Samuel
December 11, 2019 at 7:12 PM
Citrix FAS with Citrix Cloud capability is now public Tech Preview. You can read the documentation and download it here: https://docs.citrix.com/en-us/citrix-cloud/workspace-federated-authentication
Adam
December 12, 2019 at 5:49 PM
Thanks Jason. I am testing it now but using Okta instead of Azure AD
Jason Samuel
December 12, 2019 at 6:18 PM
@Adam, You’re welcome. It will work with Okta or any other identity provider exactly the same. I happened to use Azure AD as my identity provider for this guide but I also use Okta as well. I can confirm cloud-enabled FAS will work perfectly with it.
Jaakko Tapio
January 14, 2020 at 7:00 AM
Hi Jason and thanks for excellent instructions. One thing puzzles me, how can you control what apps and desktops federated users will see? On traditional FAS you will need to have “Shadow Account” which need to be mapped with federated account. Is same kind of configuration possible using Cloud Enabled FAS?
I have done same kind of configuration that you have and I’m able to login using federated account, but I cannot see any remote desktop and apps, which is obvious, because I cannot grant any access rights to federated account
Jason Samuel
January 16, 2020 at 7:31 PM
@Jaakko, glad to help. If you are giving users that are not in your AD access to apps and desktops, then you will still need to use shadow accounts in your AD for them. It’s exactly the same as you would with FAS for on-prem in this regard. In my example above my user account exists in both AD and AAD and was given access to the delivery group which is why my Virtual Desktop icon appears on Workspace after logging in.
Jaakko Tapio
January 16, 2020 at 11:24 PM
Does that mean in practice then, that I need to have also StoreFront and optionally (ADC) in order to accomplish ShadowAccount functionality? Where else I could configure what account is mapped to what Shadow Account?
Jason Samuel
January 17, 2020 at 8:04 AM
You create the shadow account in your AD with a random long password and let it sync to AAD using AD Connect. The UPN must match the 3rd party UPN the user is going to login with. This is how it maps up. Then assign this AD account to the proper delivery group in Studio for the virtual app or desktop. StoreFront and ADC are not needed.
Jaakko Tapio
January 20, 2020 at 1:21 AM
I have tested that, but mapping doesn’t work. I can login using FAS account, but I only see resources that are assigned “allow any authenticated users to use this delivery group” and after launching app, it’s prompting domain username and password 🙁
T Reb
February 5, 2020 at 4:35 PM
When using FAS for authentication into the VDA, do Office 365 applications within the VDA support Azure Seamless SSO for authentication and activation?
We found with FAS on premise that Office 365 Azure Seamless SSO does not work since it’s a certificate based authentication and therefore needs ADFS . (dsregcmd /status reports AzureAdPrt : No). SSO into Windows works fine, just not O365.
Seabron S Wilson
March 26, 2020 at 2:42 PM
I have setup Azure AD support in the cloud and a FAS server local. When I atempt to launch an app I get the login screen for the VDA. If I look at the event on the DC I am getting an Event 21. The client certificate for the user “Domain\User Name” is not valid, and resulted in a failed smartcard logon. Please contact the user for more information about the certificate they’re attempting to use for smartcard logon. The chain status was : The revocation function was unable to check revocation because the revocation server was offline. Any thoughts?
Thanks
Seabron Wilson
Shashi
April 22, 2020 at 5:54 PM
Hi Jason, we are deploying citrix cloud with on-prem Netscaler Gateway and VDA’s. We are looking to use okta as idp (now out of tech preview) with on-prem FAS server for SSO. Is this doable?
Omar Hempsall
June 16, 2020 at 3:56 AM
Hi Jason, great article. – We’re finding that the Workspace App on endpoints works exactly as it should with FAS, but the AAD/SAML signin times out pretty quickly and users need to re-authenticate at least once a day. Is this your experience too?
davidowen
October 7, 2020 at 6:09 AM
Is there a way to get single sign on working to https://companyname.citrix.com workspace url when using Azure AD?? You’ve said it prompts you for credentials in your article, is there a way for azure AD to sign you in automatically?
Rakesh
November 24, 2020 at 12:01 PM
it’s a great article, we are using FAS on prim with citrix cloud, authentication works fine but can not launch any o365 application because we do have conditional access policy on azure to check whether the request is from domain joined machine or not but if i disable this policy then everything works fine, is there any possibilities to use FAS with azure with conditional access policy.
John
June 8, 2022 at 11:59 PM
Hi Jason,
Thanks for this.
Thank you for this article.
We follow the below youtube video and documentation of citrix to setup FAS for SSO.
https://www.youtube.com/watch?v=WQfn_rLyZWs
https://docs.citrix.com/en-us/citrix-workspace/optimize-cvad/workspace-federated-authentication.html
We use Azure AD as IDP, we are able to single sign-on to desktop/VDI experience but not on the virtual apps(web applications) who integrated to on- premise active directory. We ensure also that we set up UPN on the on-premise AD to sync it to the Azure AD.
This is the challenges we are facing right now,hoping for your response what are the things that we have missed? Thank you!
Regards