
It was an especially beautiful November week in 2017 when I visited Microsoft’s Redmond campus. Autumn in Redmond is such an amazing time. I’ve never seen such a variety of colors everywhere I stepped. Every fallen leaf felt like it was unique but somehow fit into a big beautiful pattern on the ground. I don’t know how anyone gets work done at Microsoft when it looks like this all over campus. While I did walk around like a tourist snapping pictures of leaves, I also spoke with a lot of people and you could tell there was a lot of excitement in the air. Microsoft Ignite 2017 had just taken place in October and Remote Desktop modern infrastructure (RDmi) was finally presented in more depth at the conference after having been announced earlier in the year. The world wanted more info and the IT community was clamoring for any morsel of knowledge to help plan where their EUC environments were going.
I was at the Redmond campus meeting with various product teams and leadership about digital transformation initiatives, including several RDS team members on what laid ahead for RDmi. What I heard as far as roadmap and had an opportunity to try out was going to be exciting for the EUC community. Something different than anyone could predict. It was going to spotlight and align a lot of critical areas for virtual desktop infrastructure (VDI) and server-based computing (SBC) which would progress End User Computing (EUC) as a whole for everyone in the industry very positively.
Less than 2 years later from my visit, RDmi evolved into Microsoft Windows Virtual Desktop (WVD) and became Generally Available on September 30, 2019. At Microsoft Ignite 2019, it was one of the top of mind items for many attendees. Every session was packed. As we enter 2020, many companies are looking ahead on what their EUC environment strategy is and how to use and incorporate Microsoft WVD with partner solutions. I want to give a rundown on what exactly Microsoft WVD is and how you can use it with your existing investments.
What is Microsoft WVD?
RDS and RDmi evolved
Remote Desktop Services (RDS) is a group of services built-into Windows Server OS and has been the foundation for SBC (server-based computing) and end-user computing over a remoting protocol for 20+ years. Remember Windows NT Server 4.0 Terminal Server Edition released back in 1998? Yeah, that was the beginning of the journey. Specifically, the Remote Desktop Session Host (RDSH) role allowed the server’s desktop sessions and apps to be virtualized over a remoting protocol for end-users to consume in a client-server model session on demand. In the enterprise world, we tend to extend RDS using Citrix Virtual Apps and Desktops (CVAD) or VMware Horizon as the most common ways to add tremendous business value to it that enterprises need. We even began to move beyond the Windows Server OS and use Windows Desktop OS starting with Windows XP to deliver one-to-one virtual desktops with some of these solutions.
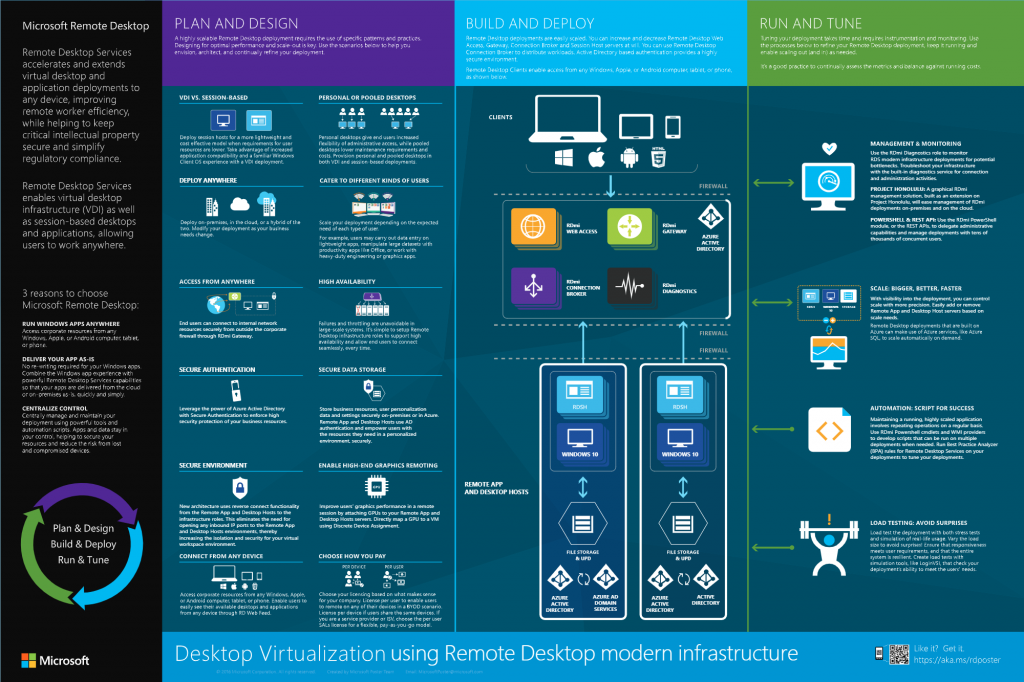
Remote Desktop modern infrastructure (RDmi) was to be the evolution of RDS. Microsoft and every other software vendor on the planet has been in the process of delivering cloud-based PaaS (platform-as-a-service) offerings to the enterprise in a subscription form. RDmi was to be an easy way for all the traditional RDS infrastructure roles to run in Microsoft Azure as a service without the need for Windows Servers so that customers don’t have to worry about deploying and maintaining them anymore. Windows updates, anti-virus, backups, etc all have software licensing and human capital costs where a PaaS offering eliminates this overhead so you can focus your time on more important business outcomes. For workloads, RDmi was designed to allow you to utilize Server OS as with RDS, but also add the capability to deliver one-to-one virtual desktops with Windows 10 OS. Here is the original planning poster for RDmi from 2017 I used to explain to people how it would work once it was released: https://docs.microsoft.com/en-us/windows-server/remote/remote-desktop-services/rds-poster
Over time, as the solution went through various Previews and became generally available, the name was changed to the more friendly Microsoft Windows Virtual Desktop (WVD) moniker. No more was the focus on infrastructure. We were now celebrating the end-user facing portion of the solution.
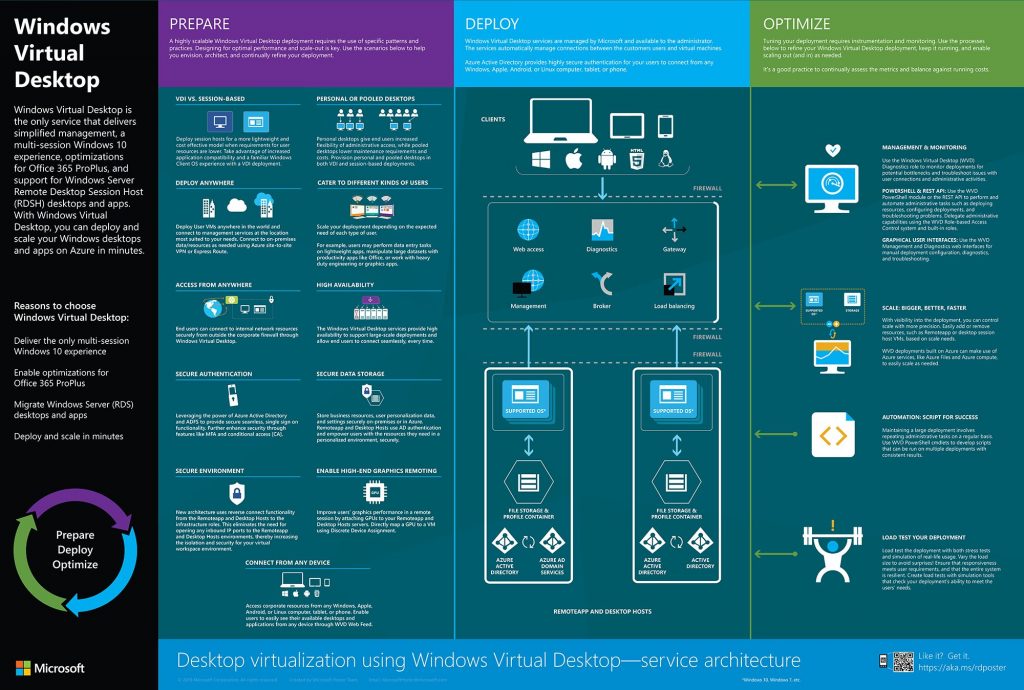
You can see the most up to date planning poster for Microsoft WVD is really all the same concepts and architecture we saw with RDmi.
So why am I giving you a brief history of RDS, RDmi, and the evolution to WVD? You need to understand the pedigree of the solution to fully understand what it is and how to use it. Rest assured, the concepts you were using throughout your career are all still there.
WVD Control Plane
The WVD control plane consists of the same infrastructure roles as you would have on-prem but are now in an Azure cloud-based service in Azure App Service. This way these roles can run as a PaaS (platform-as-a-service) solution instead of needing servers and you having to deploy and maintain them in IaaS (infrastructure-as-a-service). The components of WVD that you simply use and don’t ever manage or have to worry about are:
- Gateway – for remote access
- Web – for virtual desktop and RemoteApp virtual app enumeration
- Diagnostics – for event correlation
- Broker – for brokering
- Load balancing – for scaling load
- SQL – using Azure SQL instead of on-prem SQL Server to store the database
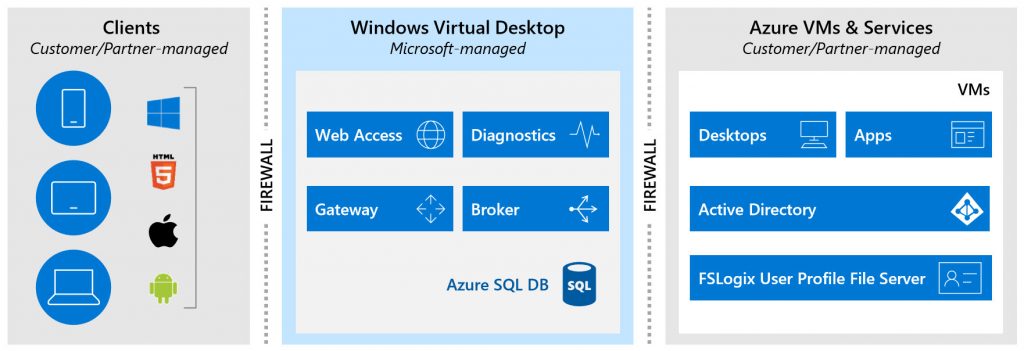
You can use the WVD Control Plane to manage workloads from the following OS types:
- Windows 10 Enterprise multi-session
- Windows 10 Enterprise
- Windows 7 Enterprise
- Windows Server 2019
- Windows Server 2016
- Windows Server 2012 R2
Yes, Windows 7 went end of extended support in Jan 2020, however, Microsoft is giving you an opportunity to move Windows 7 legacy apps into Azure temporarily as you figure out how to migrate them to Windows 10. You will have free Extended Security Updates (ESU) until Jan 2023 and can run Windows 7 in the cloud in a secure and isolated fashion you would probably have a hard time doing on-prem without considerable security risk.
PowerShell and Management console
Being successful in the cloud is all about automation and that’s what the focus is on with Microsoft WVD. The focus is very much on REST APIs and PowerShell before GUI functionality. This is nice because both partners and customers can extend and automate Microsoft WVD as they see fit. This approach benefited the solution since many ISVs (independent software vendors) and people in the community were able to shape Microsoft WVD value-add as they saw fit. Development time has to be prioritized and if Microsoft were to focus on releasing a robust GUI, this could have become a blocker for many ISVs as they waited for the APIs. Launching the solution with development prioritization on REST APIs opens up the entire platform.
There is a management tool but even in Microsoft’s documentation, they encourage you to download the code from GitHub and customize the tool ( https://docs.microsoft.com/en-us/azure/virtual-desktop/manage-resources-using-ui):
With all that said, there is a more robust GUI management experience coming for administrators and was shown off by Scott Manchester at a Microsoft Mechanics Live session at Ignite 2019. Watch this video and you can see it at the 14:05 mark. You might even catch me sitting in the front row with my head down looking at my phone, only because I was furiously posting all this breaking news on Twitter. 🙂
Microsoft Endpoint Management (Intune + SCCM) will also have support for Windows 10 Enterprise multi-session sometime in the future. You don’t need every feature of Intune for a VDI/SBC environment of course, but there are some key pieces that would be beneficial. It may even mean support for HAADJ (Hybrid Azure AD Join) as well since it is a requirement for Intune enrollment. This will help for things like Azure AD Conditional Access when using Azure AD protected enterprise apps within a virtual desktop session. Conditional Access is a key component of Microsoft’s Zero Trust security strategy and I’m really looking forward to what this MEM integration shapes out to be in the future. Any device, as shown below at Ignite 2019, should be a hint that parity is coming no matter the Windows 10 form factor or system state (persistent vs. non-persistent) hopefully. This is a really great time for EUC with all this alignment happening. 🙂
WVD Tenant and Host Pools
Host pools are groups of Windows Desktop OS and Server OS VMs you stand up in Azure that you will use to deliver a remoting session. To get started, you need to create a WVD tenant (also known as a WVD Workspace).
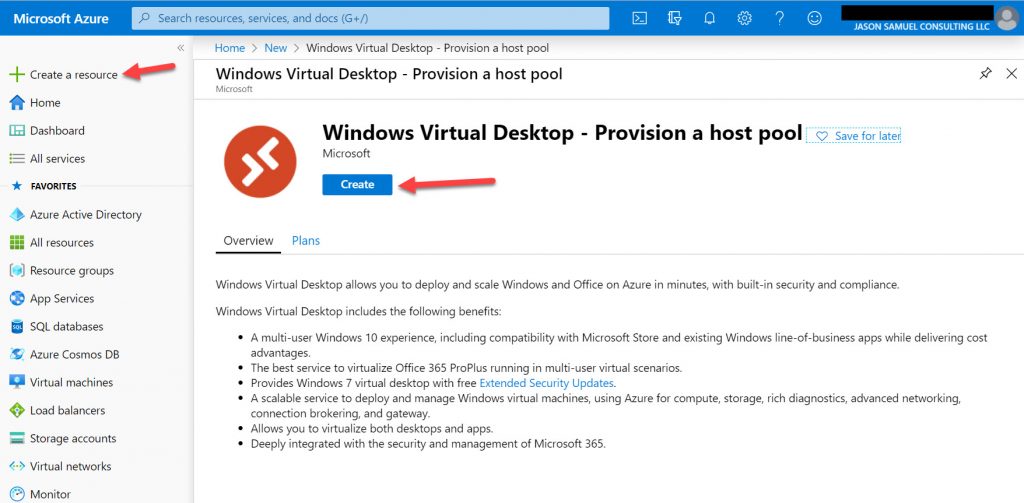
1. This can be accomplished by logging into https://portal.azure.com/ and click “Create a resource” in the left-hand navigation. Then search the Azure Marketplace for “Windows Virtual Desktop” and click on the result which will give you a screen like this. Click “Create” to get started. You can also use PowerShell of course but I find this UI to be the easiest when getting started and understanding WVD concepts:
2. Then you can begin setting up your first host pool, pooled vs. personal virtual desktop, what region you’d like to deploy in, etc.:
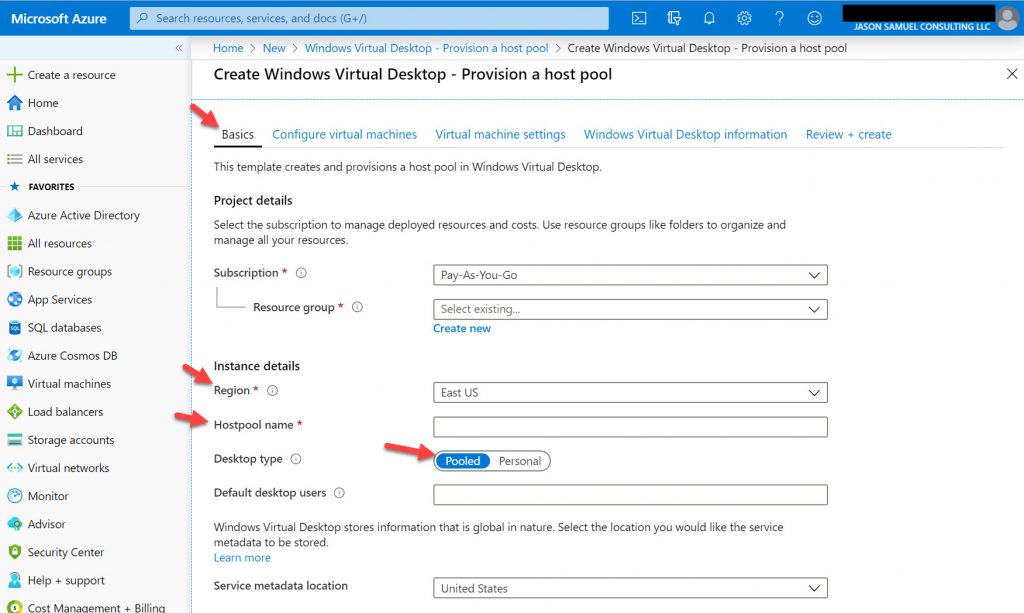
3. Next, you need to choose the type of user that will be using the virtual desktops. The default is Medium and will give you 7 of the D4s v3 VMs with 4 vCPU and 16 GB RAM that all will share. My standard for VDI is usually 4 vCPU and 8 GB RAM for a good experience so this Medium profile will likely be perfect for most users. Remember, a user can be a Medium user the first 3 days of the week and then on the 4th they may run some intensive end of month report that can really tax the system and classify them as a Power user. It is your responsibility to monitor and size up VMs or scale outward when you see users taxing their VMs. This is where tools like ControlUp can really help you determine the best fit for each user. If you choose the other profiles like Heavy and Power it will bump the number of VMs up (scale-out) to 25 and 100 VMs respectively when you go with the default 100 user option:
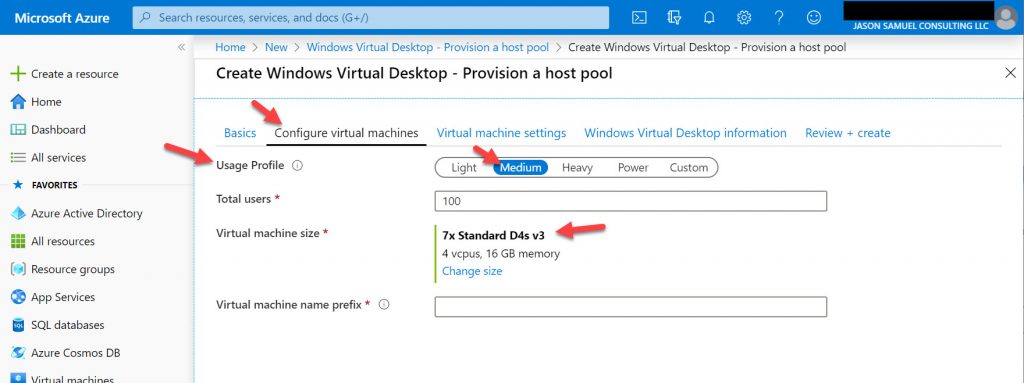
4. Now you select the image for the VM. The default will be Windows 10 Enterprise multi-session with Office 365 ProPlus already installed and optimized in the image. Honestly, I love this. Installing Office and dealing with KMS activations and other issues is a thing of the past now. The WVD team and Office team worked together to make this image so everything is going to work very well with this image. Also, make sure to leave the disk type as the default Premium SSD. Anything less and performance is not very acceptable for most users in my opinion:
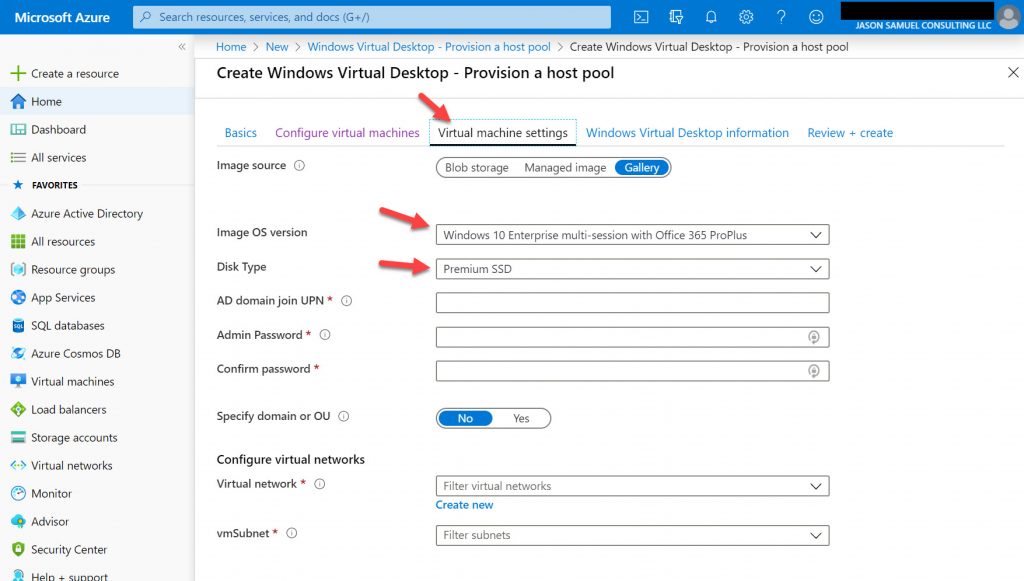
Other Image OS versions when hitting the drop-down for reference, again, choose the default with O365 ProPlus included for the best experience:
5. Now create your WVD tenant. Once you have entered your info and move on to the Review + create section, it will validate all your settings and begin creating your WVD tenant and all the VMs you specified earlier into a host pool. The amount of time it takes will be dependent on the number of VMs you are deploying:
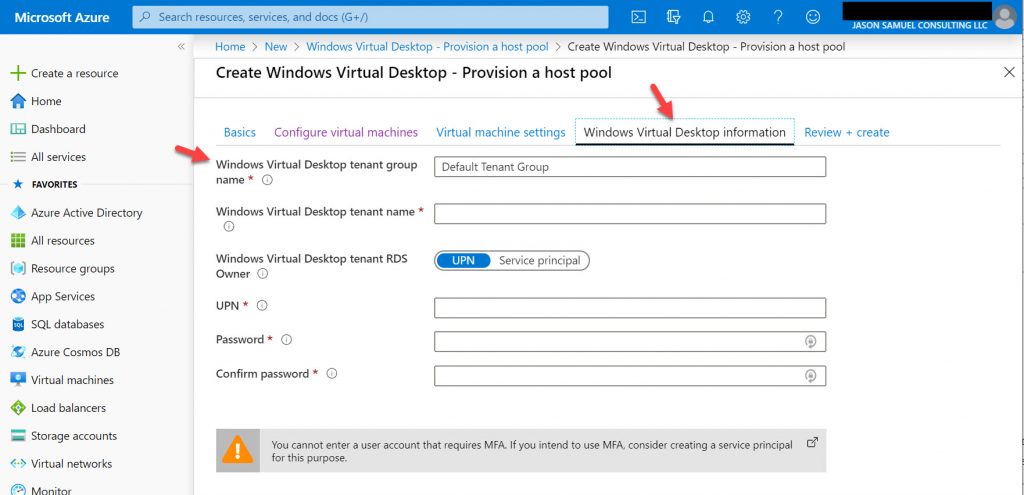
If you would prefer to get started with WVD using PowerShell and go deeper into these concepts, there is an excellent session Pieter Wigleven did at Microsoft Ignite 2019 here starting at the 6:05 mark covering this and the actual steps starting at around 13:18:
And his accompanying blog that he mentions in the video with step-by-step instructions is at http://aka.ms/startwvd. He has some excellent visuals and PowerShell here showing what the manual experience should be so you can simply copy and paste them as you follow along in the video above.
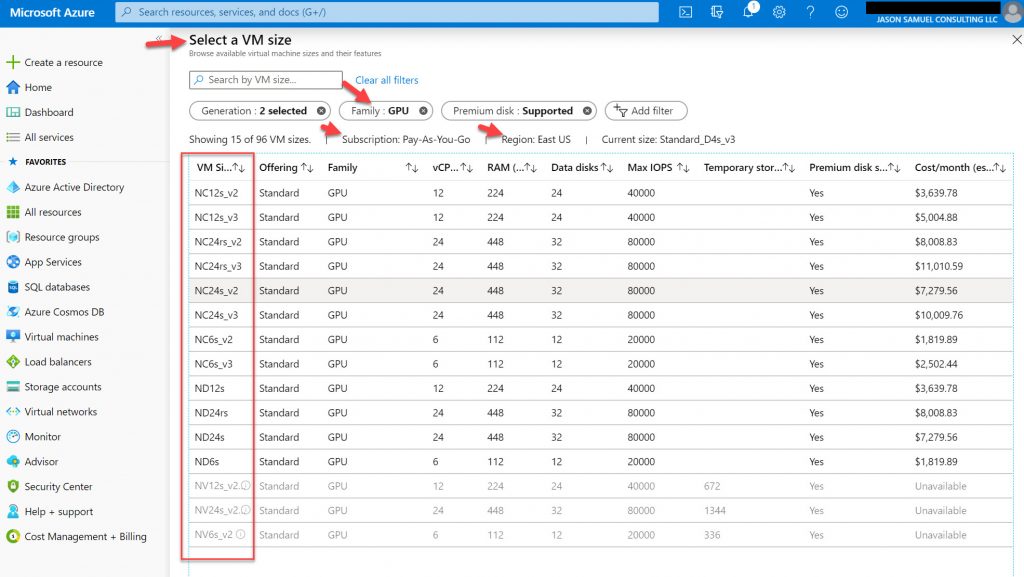
GPU optimized VMs
Yes, WVD supports NVIDIA GRID and AMD Radeon backed VMs as well for high-performance graphics workloads, one of the mainstays of EUC and remoting. Specifically, you will want to focus on the NV series VMs for your session hosts and what is available is dependent on the regions you are deploying the VMs in as well as what’s enabled on the subscription you have chosen during WVD host pool provisioning: https://docs.microsoft.com/en-us/azure/virtual-machines/windows/sizes-gpu. The AMD ones (NVv4 series) are only available in Preview right now in South Central US and West Europe but I’m sure will quickly expand to other regions as it gets closer to general availability. GPU optimized VMs are supported with Windows 10 and Windows Server 2016 onward. Using Azure Reserved Instances can save you considerably when running these or any VMs in general for your host pools.
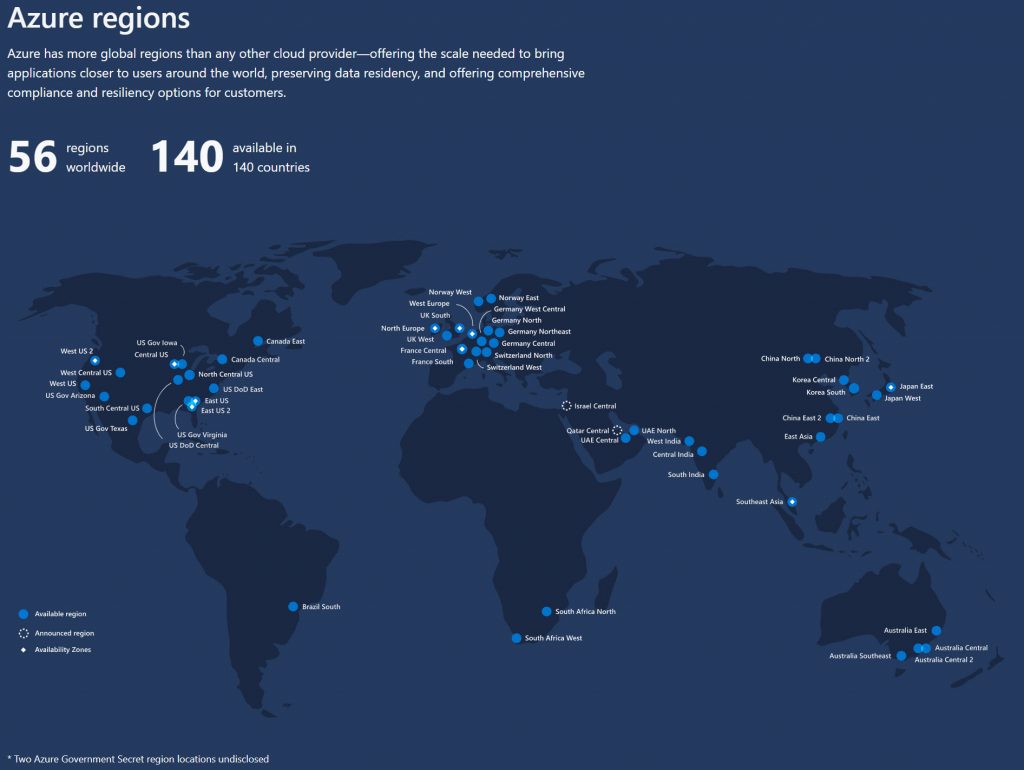
Regions
Microsoft Azure itself consists of 56 regions around the globe officially at the time of writing with more planned to come online this year. Mark Russinovich just tweeted last week it would be at 58 regions imminently. I was giving a presentation that same afternoon and had to scramble to adjust my slides that day to reflect this in the interest of accuracy. This map will be updated to reflect all 58 very soon I’m sure:
You can use the Windows Virtual Desktop Experience Estimator tool to figure out which region is best suited for your host pool workloads. You want to keep the workloads as close as possible to where the users are. Always use this tool when deploying anything end-user computing into Azure. The results are sometimes very interesting. For example, I may be closest to South Central US since I live in Houston, Texas but according to the tool there are 4 other regions that edge out performance at this moment in time, including Canada! This will change on many factors each time you refresh the page so don’t read too much into it for just a few ms. But if it’s 30 ms difference or more and it’s consistent throughout the workday and workweek, then you will want to probably deploy into the better performing region. I’m sure there will be more data points and telemetry coming to help you plan your deployments. This is currently a “just in time” tool but it would be nice to see it take data points for you over a period of time and report back to you. As with anything DaaS (desktop-as-a-service), you need to develop a DevOps mentality and constantly analyze and improve the service you are offering to your users:
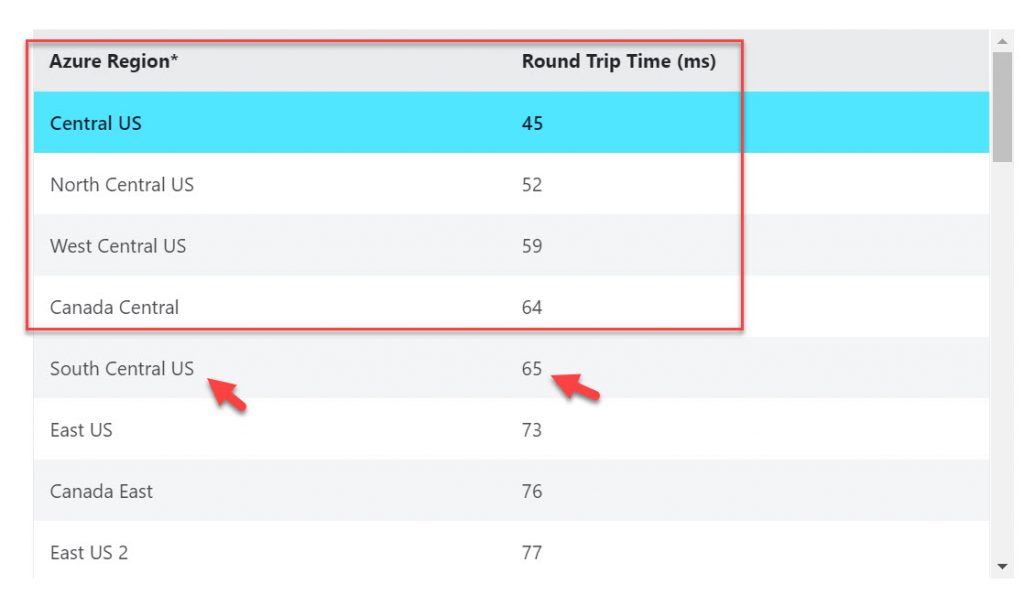
The management plane for WVD, really the points of presence (POPs) for user ingress via the WVD Gateway/WVD Web, are not available in every region yet but they will be over time. You should not worry about this too much. You have all 56 regions available to you for your workloads. Just put your IaaS workloads (host pools with your server or desktop VMs) as close to the users as possible and it will use the closest strategically placed management plane shown in the tool. Again, that list is going to cover all 56 regions over time anyhow so don’t worry about this too much.
Entitlement
You don’t buy Microsoft WVD. There is no SKU for it. It is an entitlement that comes as part of your enterprise agreement (EA) with Microsoft. You more than likely already own the benefit of being able to use it. The only cost to you is Azure IaaS consumption of your workloads in the host pools (CPU, RAM, and storage for the VMs and user profiles). You are eligible to access Windows 10 and Windows 7 with Windows Virtual Desktop if you have one of the following licenses:
- Microsoft 365 E3/E5
- Microsoft 365 A3/A5/Student Use Benefits
- Microsoft 365 F1
- Microsoft 365 Business
- Windows 10 Enterprise E3/E5
- Windows 10 Education A3/A5
- Windows 10 VDA per user
*Customers can access Windows Virtual Desktop from their non-Windows Pro endpoints if they have a Microsoft 365 E3/E5/F1/Business/A3/A5/Student Use Benefits or Windows 10 VDA per-user license.
For accessing Server OS (Windows Server 2012 R2 and newer desktops and apps) via WVD, you will still need RDS CALs with active Software Assurance (SA).
Clients and Protocol
Microsoft WVD supports a wide variety of clients on your users’ endpoints very much like we’ve been using in the Citrix and VMware world for years. Every form factor and OS is supported, as well as a completely web-based experience using HTML5 as well.
- Microsoft Windows 7, Windows 10, and Windows 10 IoT – use the Windows Desktop client
- Apple macOS 10.12 or later – use the macOS client
- Apple iOS 13.0 or later – use the iOS client on iPhone, iPad, and even iPod touch
- Google Android 4.1 and later – use the Android client
- Google Chrome OS 53 and later – use the Android client on Chromebooks
- Any device with a modern web browser – use the HTML5 based web client that is built into the WVD Web portal at https://rdweb.wvd.microsoft.com/webclient/index.html
The remoting protocol used for Microsoft WVD is Remote Desktop Protocol (RDP) which we have used for RDS environments for many years. RDGSP and RemoteFX concepts do not apply to WVD. Connectivity between your client and the WVD Gateway in Azure is over TLS using TCP port 443. I hope to see support for UDP sometime in the future as many remoting protocols are beginning to support UDP for better user experience over high latency connections.
Since WVD is using the RDP protocol, the same human interface device peripherals and USB redirection as you have used with the Remote Desktop Connection (RDC) client applies with the WVD Desktop client: https://docs.microsoft.com/en-us/windows-server/remote/remote-desktop-services/clients/remote-desktop-app-compare#redirection-support
On the backend in Azure, the Windows Virtual Desktop Agent is installed in your VMs you have brought up in your host pools. The WVD Broker running as a PaaS service controls access to them from the WVD Gateway which is also running as a PaaS service. To help you understand and draw a correlation, this is very much like many of the remoting solutions we have used in the EUC world such as Citrix Gateway (NetScaler Gateway) for Citrix VAD environments and Unified Access Gateway for VMware Horizon environments. The same reverse proxy concept where you are talking to the middleman “gateway” and the VM you are trying to get to is connecting back to this middleman as well so all traffic flows through the gateway. The connectivity between the WVD Agent and the WVD Broker/WVD Gateway is also encrypted using TLS over TCP port 443 and is called Reverse Connect.
Updates to the WVD Agent are automatic which is really nice and a welcome change from what we have seen in the EUC world in the past with agents. This will save admins considerable time. I’m a big proponent of turnkey these days. I just want things to work and not have to deal with versions of various components I have to keep track of and remember to update. DaaS (desktop-as-a-service) should quite literally be a service all the way through and we are seeing that type of simplicity for admins was very well thought out with WVD.
RemoteApp
Yes, you can use RemoteApp with WVD just as you have in the past with RDS. This means you don’t need to publish the entire desktop of the OS to the user. You can continue to publish just Windows apps only to the user if you wish. Sometimes a use case is to give users access to just an app within the datacenter and not expose and entire Windows shell environment to them. You accomplish this by creating a RemoteApp application group for the WVD host pool. In WVD terms, this is referred to as simply creating an Application Group and then assigning users to the apps in this group.
Windows 10 Enterprise multi-session OS
A server operating system was never intended to have end-users on them. But we did it for 20+ years for the sake of density, cost savings, and protecting our apps and data by keeping them contained to the datacenter. There were always pros and cons with the approach.
As part of your Microsoft WVD entitlement, you get the benefit of using the new Windows 10 Enterprise multi-session OS. This can only be obtained from the Azure Marketplace and can only be used within Azure. It will have Office 365 ProPlus already installed and optimized in the image. If you attempt to export it out of Azure and run it on-prem it will throw an error message. Likewise, if you attempt to install the Citrix VDA and it detects it’s not in Azure, it will also throw an error message.
The image can be deployed above as shown in your WVD tenant creation. Additionally, you can simply spin up a Windows 10 multi-session VM in Azure without having to tie it to a WVD host pool. This is great for just quick testing with the OS. For example, the other day one of my colleagues wanted to run a script against a baseline clean version of the OS to collect some system variable information and this how it was done quickly. Additionally, choose the Azure Spot instance option when deploying test VMs, this will save you a lot of money:
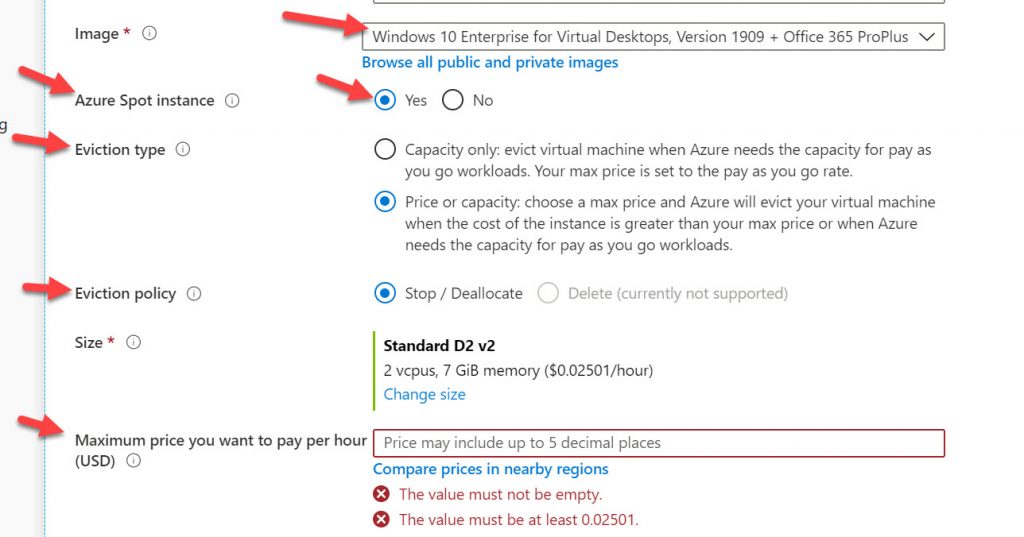
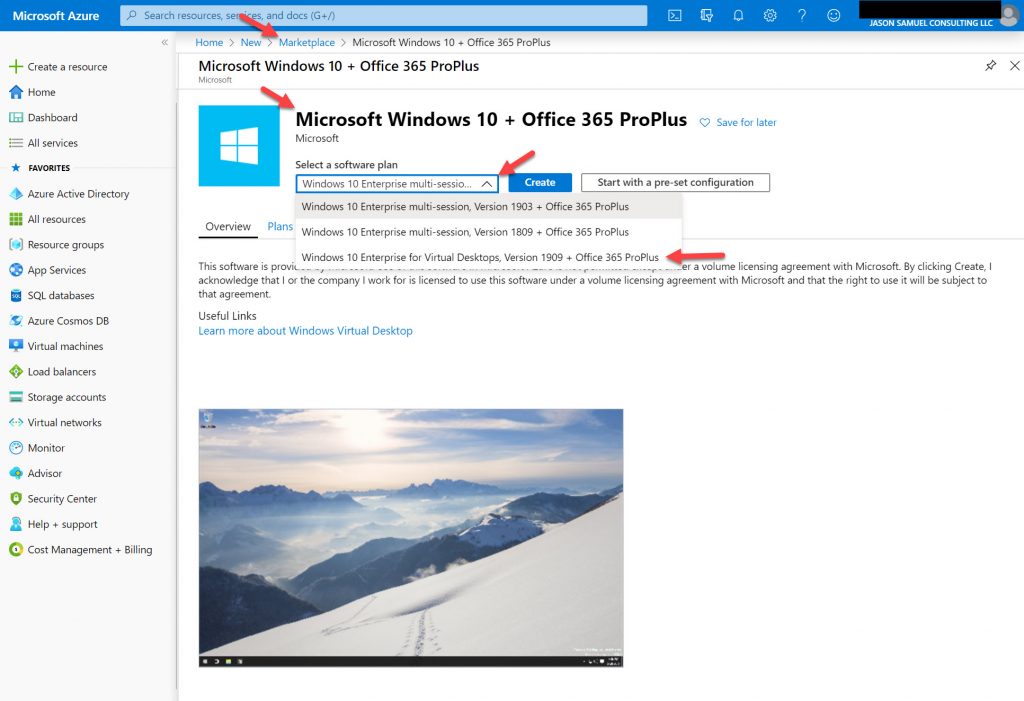
In the Azure Marketplace, you can use “Microsoft Windows 10 + Office 365 ProPlus” and choose Windows 10 Enterprise multi-session or Enterprise for Virtual Desktops depending on the build version in the drop-down box. At the time of writing there are 1809, 1903, and 1909 builds:
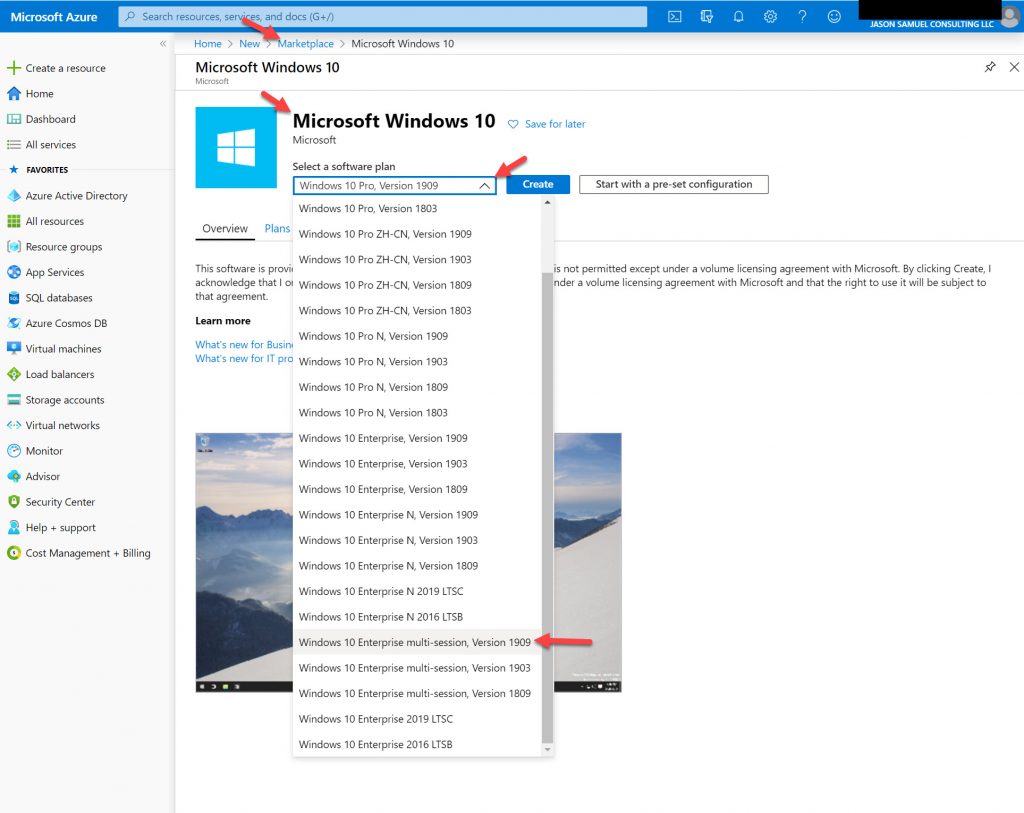
or you can use “Microsoft Windows 10” without Office installed and optimized in the image. I would recommend the latter with Office 365 Pro Plus installed, however, if you intend actually use it in production with users:
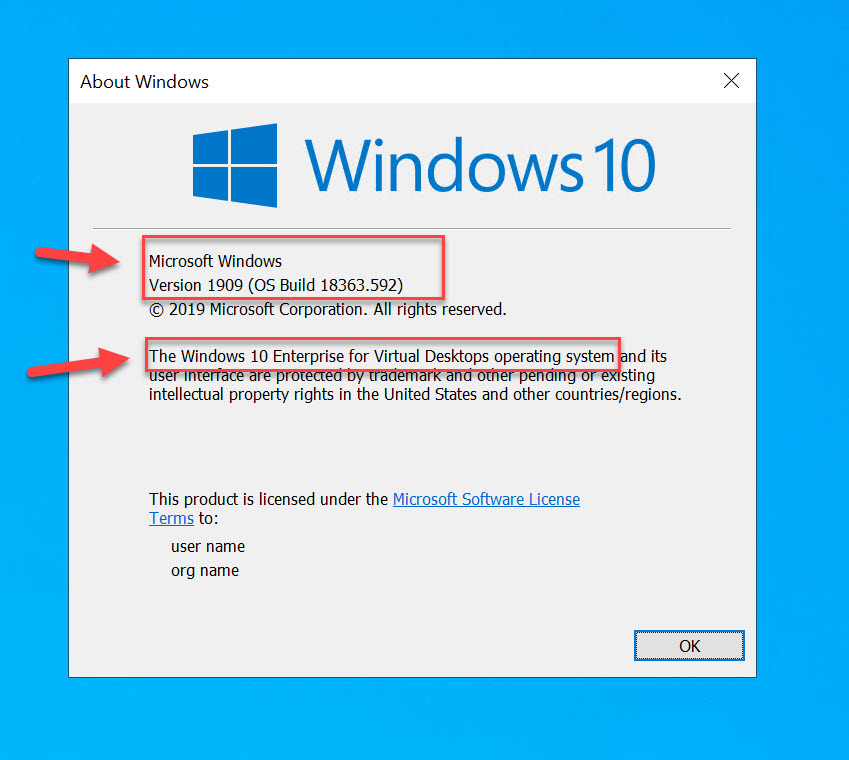
Yes, the “winver” command will say Windows 10 1909 Enterprise for Virtual Desktops (EVD) at the moment but the proper term is Windows 10 Enterprise multi-session and will likely be changed to reflect this. The point is, if you see or hear any of the terms “multi-session”, “multi-user”, or “enterprise for virtual desktops” used with Windows 10 Enterprise, don’t worry it’s the same thing and referring to this new OS flavor that can pile on as many concurrent users as you wish.
If you try to install software on Windows 10 multi-session, it will report a ProductType value of 3 back to the software installer. This means it is identifying as a Windows Server operating system. This means any apps you have installed on RDSH, Citrix Virtual Apps (XenApp), and Horizon Apps will all install and work the same way on this OS. You can go to the registry adn navigate to “Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Virtual Machine\Auto” to examine this value:
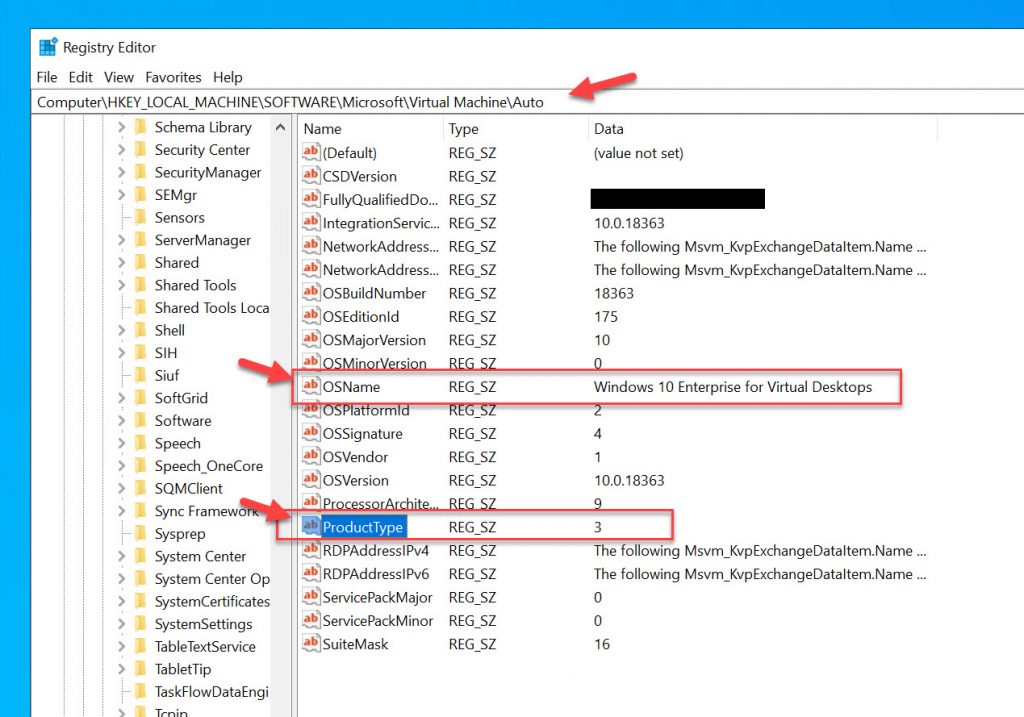
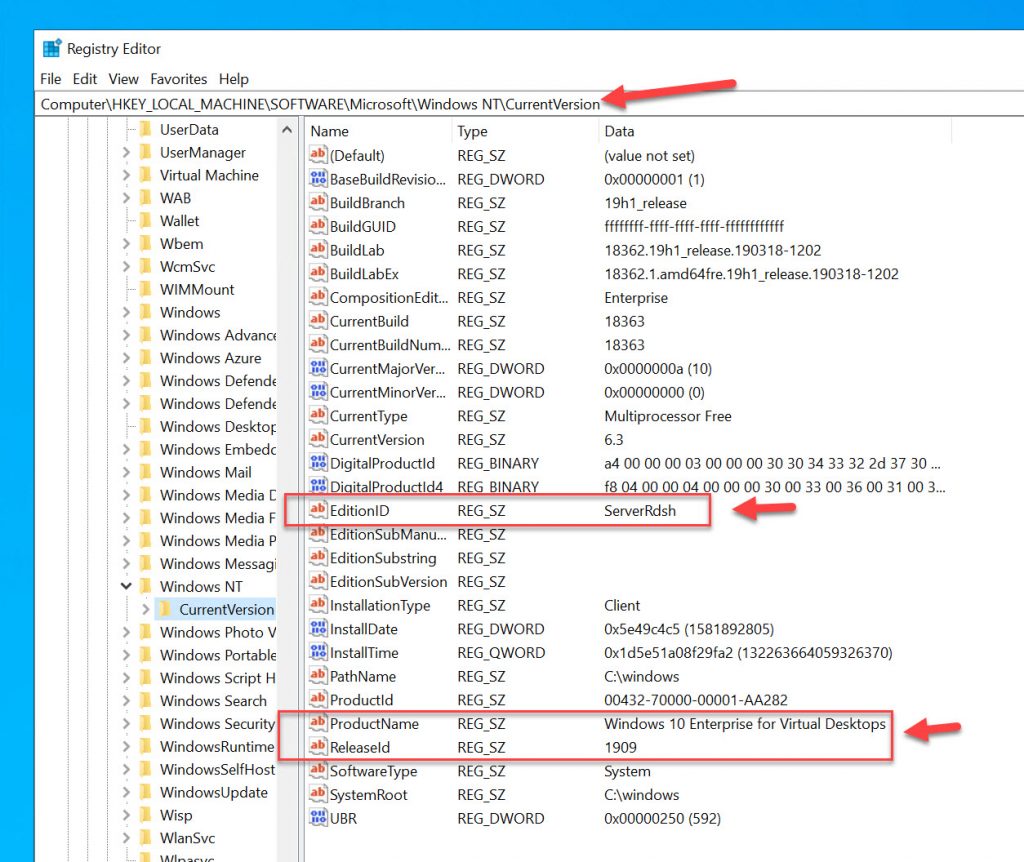
If you go to the registry and navigate to “Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion”, you will notice for EditionID it says “ServerRdsh” further showing its intended purpose for density:
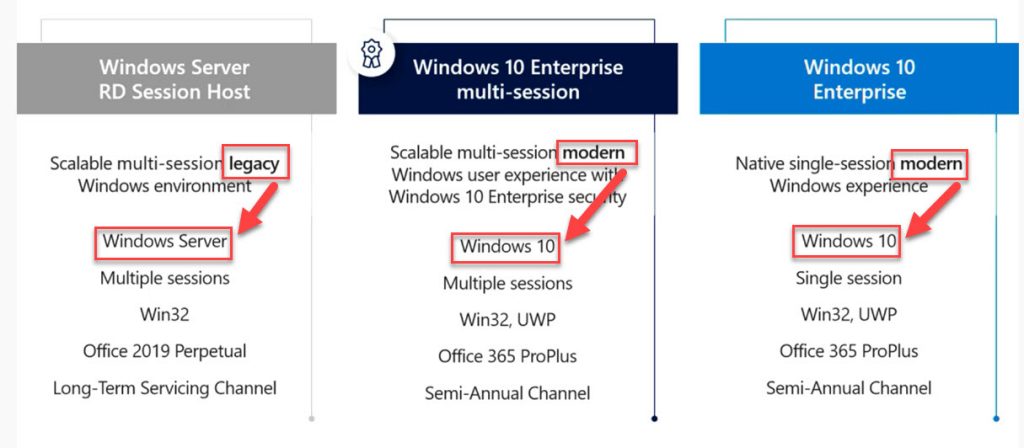
Also, note that Server OS for end-users is considered legacy now by Microsoft. Only Windows 10 Enterprise multi-session or the regular one-to-one Windows 10 should be used for EUC needs. For reference, here is Microsoft’s position on this. Notice the red boxes I’ve placed over the words legacy vs. modern, that should tell you all you need to know about the future of your EUC environment:
FSLogix
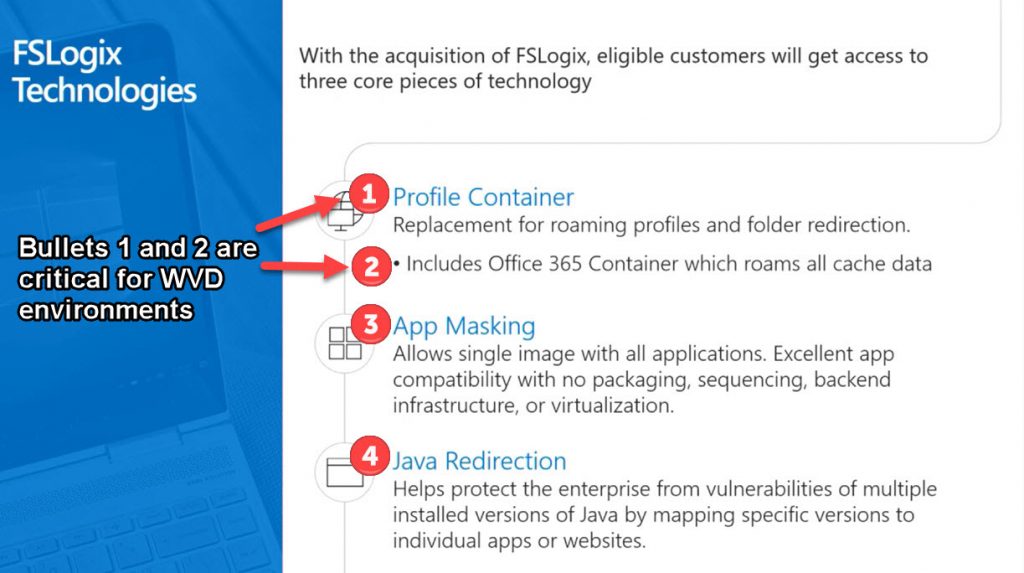
You are eligible to access FSLogix Profile Container, Office 365 Container (which is a sub-feature of Profile Container), Application Masking, and Java Redirection tools if you have one of the following licenses:
- Microsoft 365 E3/E5
- Microsoft 365 A3/A5/Student Use Benefits
- Microsoft 365 F1
- Microsoft 365 Business
- Windows 10 Enterprise E3/E5
- Windows 10 Education A3/A5
- Windows 10 VDA per user
- Remote Desktop Services (RDS) Client Access License (CAL)
- Remote Desktop Services (RDS) Subscriber Access License (SAL)
Many of us have used FSLogix for years for VDI environments prior to Microsoft acquiring the solution. You use it exactly the same way as before minus license files but plus many new validated storage options for increased scale. Bottom-line, you MUST use FSLogix Profile Container and O365 Container for your environment to be successful in my opinion. It’s free for most everyone and works extremely well so use it. App Masking and Java Redirection are nice and have been great for me in the past when I needed those features.
- FSLogix Profile Container – gives you roaming profiles and folder redirection capability via a filter driver that mounts the disk during session launch
- FSLogix Office 365 Container – gives you a place to store all the Office 365 cache data for VDI. Mainly Outlook .ost and OneDrive for Busines files are cached here. Everything in this container is disposable since it’s just cache data.
- FSLogix App Masking – install apps and only allow certain security groups (users) to see and use them while other uses are oblivious to them because they can’t see those apps in their session.
- FSLogix Java Redirection – install legacy insecure Java versions in your image for certain legacy apps in your company without exposing your whole environment to all the accompanying security issues with Java.
The storage options for storing the FSLogix Profile Container and Office 365 container .vhd / .vhdx files for each user need to be considered from a performance and availability standpoint. Microsoft has an excellent matrix here comparing Azure Files, Azure NetApp Files, and Storage Spaces Direct here: https://docs.microsoft.com/en-us/azure/virtual-desktop/store-fslogix-profile
Some of my fellow CTPs have excellent articles and tools that will help you with FSLogix availability, profile size, and profile compaction tools here:
- Architecting for FSLogix Containers High Availability by James Kindon (CTP)
- FSLogix Containers – Search Index Considerations and Troubleshooting by James Kindon (CTP)
- A Practical Guide to FSLogix Containers Capacity Planning and Maintenance by Aaron Parker (CTP)
- FSLogix Profile Compacting Tool by David Ott (CTA)
- FSLogix Profile Cleanup script by Aaron Parker (CTP)
- Other great writeups related to FSLogix that may come in handy for you by James Kindon (CTP)
- Heads up! The future of storing your Microsoft / FSLogix Profile Container on Azure Files as platform service (lowest TCO) for Windows Virtual Desktop by Christiaan Brinkhoff (CTP, vExpert)
- FSLogix S2E1 Configuring FSLogix Profiles and Office Containers for the enterprise by Jim Moyle (CTP)
MSIX app attach
MSIX is a Windows app package container format that borrows from all the benefits over the years of MSI, .appx, App-V, and ClickOnce. It is basically the future of modern application packaging for Microsoft Windows environments. MSIX can be used for both physical and virtual endpoints. MSIX app attach is a function of your WVD entitlement and meant to be used for virtual environments only. So think of it as purpose-built for Microsoft WVD and VDI/SBC needs. It is based on the same filter driver technology as FSLogix and mounts MSIX packaged apps that have been expanded into .vhd or .vhdx format during session launch. So dynamic app delivery per user completely independent of the operating system base image. These containers can be stored using the same storage infrastructure you choose for FSLogix Profile and O365 Containers. In fact, because the MSIX app attach .vhd is read-only, it will utilize the FSLogix Profile Container .vhd to store application state which means app state can roam between VM sessions as well. The solutions really complement each other in this way. MSIX app attach is currently in Public Preview at the time of writing this article.
Check out this video from Randy Cook and Joydeep Mukherjee‘s MSIX app attach session at Microsoft Ignite 2019. There are also some tidbits on a new high-performance read-only file system type for MSIX app attach that goes beyond .vhd that Randy mentions we should be on the lookout for at the 9:23 mark. I was in the audience that day and I tell you when I heard that, the brain just paused taking a second to process that, and then leap into action with one of my most furiously thumbed posts on Twitter from all of Ignite 2019. Sounds like yet another game-changer for app delivery that will benefit all of EUC:
App Assure
The little known benefit of your Microsoft WVD entitlement. Microsoft will fix all your legacy craplications for free. This is your magic bullet to eliminate all the problem apps in your environment and hopefully save your sanity. You know, the ones that the app owner says are not compatible with new OSes and says “don’t touch anything” whenever you bring them up in discussion. Use this service for free to uproot these boat anchors and move them into your modern EUC environment:

App Assure is part of the FastTrack Center Benefit. It also helps with any issues you may encounter with the new Chromium-based Microsoft Edge. You can make an app Assure service request here: https://docs.microsoft.com/en-us/fasttrack/win-10-app-assure
The key is there is no cost for this service. Microsoft is providing this service to enterprises for free. That takes so much pressure off of you for apps that have deadlocked or held hostage progress in your company. Bring this up with your IT leadership teams so they can socialize this any chance they get with the business. It truly is one of the most powerful tools in your arsenal and you don’t have to lift a finger. It’s instant augmentation of your EUC team for free.
WVD Automatic Scaling & Automation
Anyone can build a VM but in the cloud, everything is about scale and automation or you are doing it wrong. With WVD you can choose the number of VMs you want to deploy but they are going to sit there in a powered-on state costing you IaaS compute you are going to pay a lot of money for regardless if anyone is actually using them or not.
Microsoft released a new scale session hosts tool to be used with the Azure Automation service available here: https://docs.microsoft.com/en-us/azure/virtual-desktop/set-up-scaling-script
The scaling tool is a combo of Azure Automation PowerShell runbooks, webhooks, and Azure Logic Apps that create a job that runs periodically on a recurring interval. There is no GUI for it at this time. It can be used for the following on pooled session host VMs:
- Scheduling VMs to start and stop based on Peak and Off-Peak business hours.
- Scale-out VMs based on the number of sessions per CPU core.
- Scale-in VMs during Off-Peak hours, leaving the minimum number of session host VMs running.
The load balancing method can be breadth-first load balancing or depth-first load balancing:
- Breadth-first is the default setting and will distribute sessions across all available session hosts in a host pool. This setting is the default because it does not require you to maintain the setting and you only have to worry about having enough VMs in your host pool. It’s more of the set it and forget it type load balancing for this reason.
- Depth-first is more cost savings oriented and will distribute sessions to an available session host with the highest number of connections but hasn’t reached it’s max session limit threshold. This will give you the most density and lower costs in Azure with each VM running near capacity before another VM is needed. Depth-first requires additional configuration and you must be careful to tune this correctly as well as keep an eye on it from time to time to ensure the settings continue to make sense for your host pools and the workloads you are putting on them.
Running WVD on-prem with Azure Stack Hub
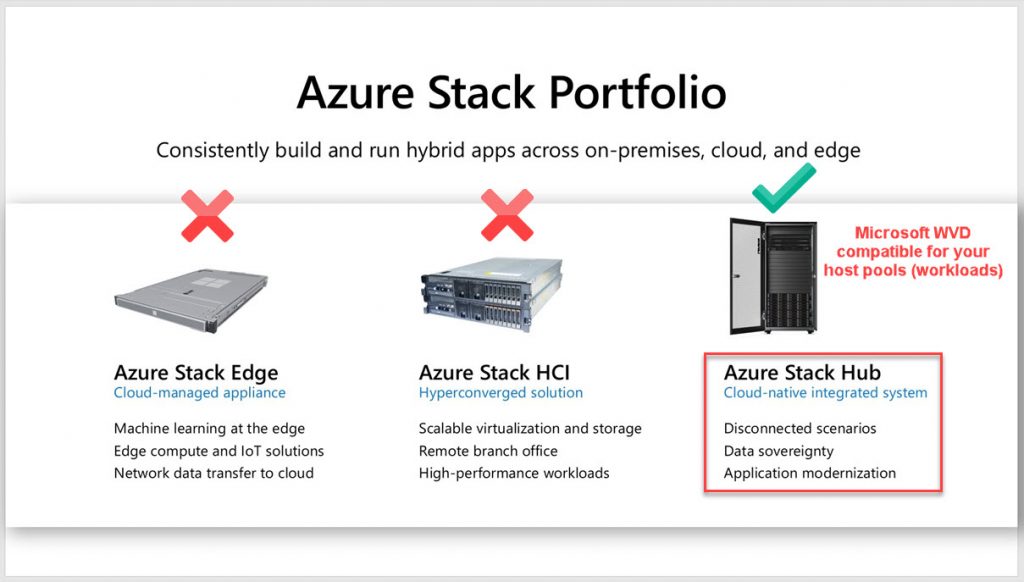
Microsoft WVD is a control plane that runs in Microsoft Azure. It cannot be run on-prem, it’s a PaaS offering. However, you can run host pools with Windows 10 Enterprise multi-session outside of Azure and control it all with the WVD control plane running in Azure cloud. Just not on your hypervisor and hardware of choice. It must be on Azure Stack Hub at this time. Perhaps in the future, that may change, but for now, it has to be Azure Stack Hub. This feature is in Private Preview right now and of course, you must shell out the cash for the Azure Stack Hub hardware as well as the pay-as-you-use consumption.
There are 3 options for Azure Stack: Azure Stack Edge, Azure Stack HCI, and Azure Stack Hub. So if you have Azure Stack HCI, you cannot run Windows 10 multi-session on it. You must use Azure Stack Hub which is designed for “disconnected” scenarios when talking to Azure cloud may be a challenge on low-bandwidth. If you are running Azure Stack HCI, then you more than likely have good connectivity to Azure itself so Microsoft wants you to run Windows 10 multi-session in Azure itself. Here is a diagram illustrating the 3 Azure Stack solutions and where WVD host pool workloads can go:
Here are a few pictures I took of Azure Stack Hub using HPE hardware at Microsoft Ignite 2019. It was basically a half-rack full of HCI that’s designed to be an extension of Azure cloud but running locally in your remote datacenter. I was hoping my home would count as a remote datacenter and the booth attendants would let me take it for a spin, but that carpet was a bit of an issue when I tried rolling it so I let it be. That esoteric blue on black “Microsoft Azure” logo on the front panel is just calling to me:





Azure Active Directory as Identity Provider
WVD supports Azure Active Directory. For example, you can navigate to the WVD web client at https://rdweb.wvd.microsoft.com/webclient/index.html and you will immediately see your Azure AD account can be used to enumerate resources (virtual desktops and RemoteApp applications). If you’re already logged in to other AAD protected services or are on an Azure AD Joined or Hybrid Azure AD Joined device as your client, then it will simply SSO you in using the existing authentication token when you visit that URL. Remember, WVD is a native Azure service so it was built with AAD in mind.
Azure AD Conditional Access policy can also target Windows Virtual Desktop:
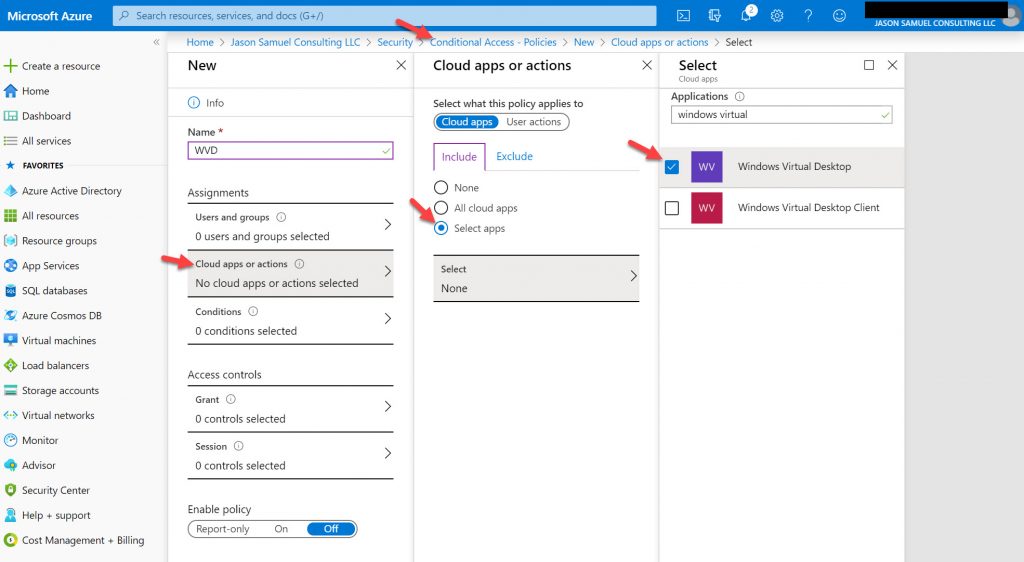
The VMs in your host pool acting as session hosts, however, must be Active Directory joined at this time against your nearest domain controller to where the workloads reside. Azure AD Join is not supported and Hybrid Azure AD Join is slowly getting support but only in certain scenarios as outlined here: https://docs.microsoft.com/en-us/azure/active-directory/devices/howto-device-identity-virtual-desktop-infrastructure
Passwordless authentication with Microsoft Authenticator phone sign-in
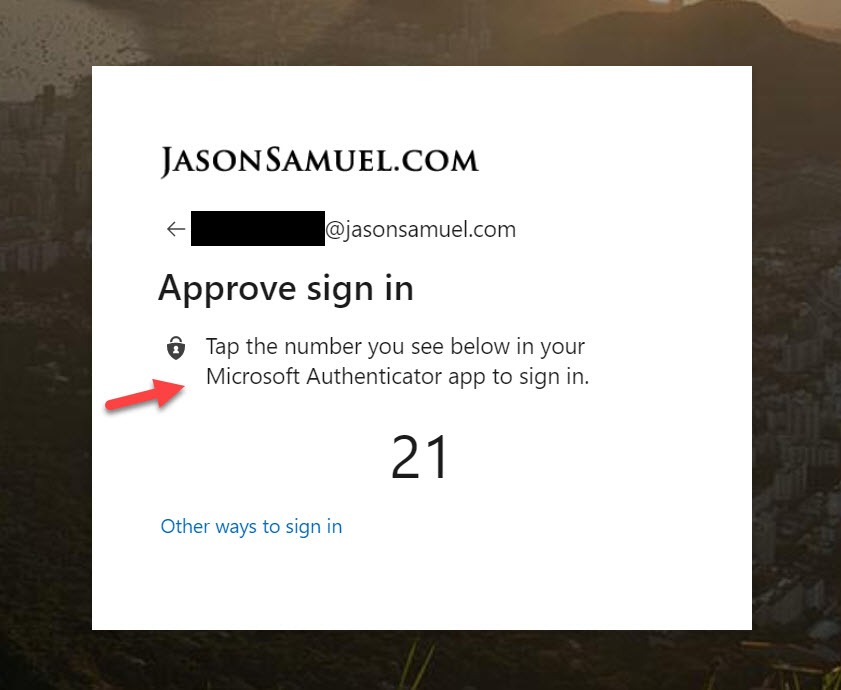
Microsoft Authenticator passwordless phone sign-in which I have talked about many times in the past is supported by Azure AD, therefore it is supported by WVD. Authentication happens before authorization and enumeration of the WVD service. Since WVD is a native Azure service, it is able to support Azure AD natively as a result. There is nothing you need to do to make this work. It’s already built-in, you just need to enable it under Azure AD in Authentication Methods for your users as I have previously discussed here.
Passwordless authentication with FIDO2 hardware security keys
FIDO2 hardware security keys which I have also talked about many times now are also supported by Azure AD, and therefore supported by WVD. For all the same reasons as Authenticator above. You enable it in the same spot in your AAD tenant.
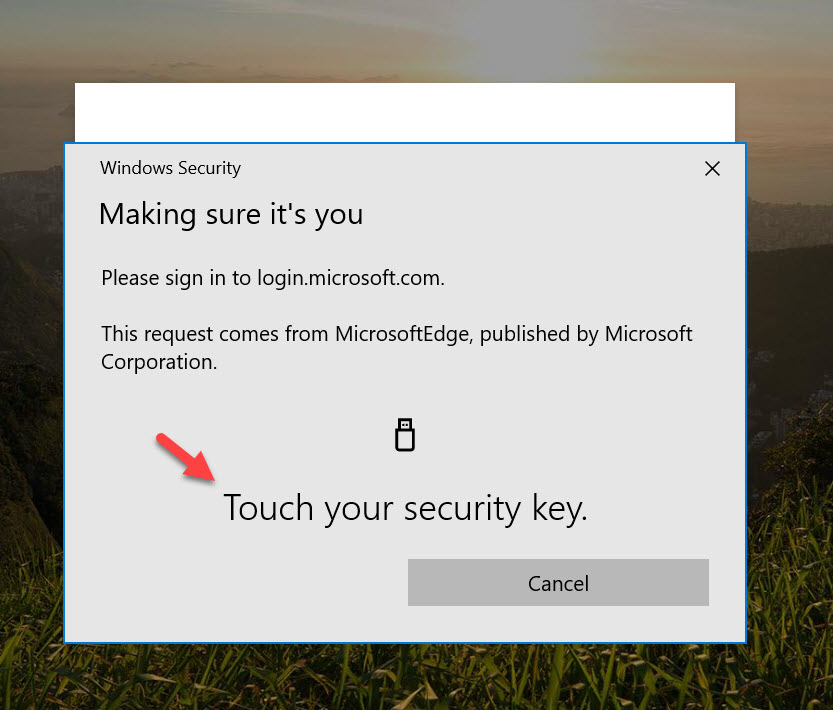
SSO into Windows with AD FS
If you’re a longtime reader you know how much I love SSO and authentication for end-user computing over remoting protocols. Microsoft WVD requires you to use AD FS for SSO using the ConfigureWVDSSO PowerShell script in the PowerShell Gallery. It works very similarly to Citrix FAS or VMware True SSO in the way a short-lived x.509 certificate is issued from your Microsoft CA to the user in order to trick the Windows 10 OS into thinking this “virtual” smart card is a physical smart card. In the case of WVD, AD FS will be the middle-man working with the Microsoft CA as opposed to FAS or True SSO in those respective brokering environments. I am hoping in time we will see the Windows core engineering team add a credential provider for both Windows desktop and server OSes where the needs of SSO over a remoting protocol is considered. Perhaps some sort of trust with the identity provider (Azure AD), credential provider, and WVD agent or partner agent. Who knows what the future holds but I’ll be sure to type up a guide as soon as we see features released here over time.
What’s coming next with Microsoft WVD?
Many Partners
These are the partners that currently extend or add value to Microsoft WVD deployments. The list is updated all the time so check https://docs.microsoft.com/en-us/azure/virtual-desktop/partners for the latest.
- Citrix
- VMware – Note, this is not GA at the time of writing but you can register for the Tech Preview of Horizon Cloud on Azure here
- 10ZiG
- Cloudhouse
- CloudJumper
- ControlUp
- deviceTRUST
- HP
- IGEL – Note, you can sign up for early access to the new IGEL Linux Client for WVD here
- Ivanti
- Lakeside Software
- Liquidware
- Liquit
- Login VSI
- Nerdio
- Numecent
- PolicyPak
- PrinterLogic
- Printix
- RDPSoft
- sepago
- ThinPrint
- Tricerat
- Workspot
Feature Velocity
There are WVD features seemingly coming out every few weeks. This is a great sign that Microsoft has a very well resourced and agile engineering team behind the scenes providing this development velocity. Thus far we have seen a very heavy development in capability for WVD. In my opinion, it has succeeded in providing the user experience portion of DaaS. It now needs a little more simplicity for the admin experience portion for more of a full turn-key DaaS platform. I am sure we will continue seeing this developed throughout the year as well as the partner solution ecosystem extending the capabilities further.
Additionally, we are seeing a lot of features coming for the Azure ecosystem and other Microsoft products themselves that are designed to support WVD. Everything from computing and storage in IaaS, to PaaS services like Azure AD and Azure Files, to entire suites of products like Office and Windows 10 itself…they are all aligning to help virtual desktops. Virtual desktops are front and center now at Microsoft when many years ago it was considered a niche. These benefits and progress are not just exclusive to the WVD control plane. Many of these benefits progress on-prem EUC environments with workloads in Azure and on-prem environments in your datacenter no matter which partner technologies you use.
VDI and DaaS is not turnkey…you still have a job
While you can use a DaaS (desktop-as-a-service) control plane that may be turn-key, there is still much work for the EUC engineer to work on in order for the environment to be successful. One of the fears I keep hearing from people is “Will I still have a job?” when parts of what is usually administered by them on servers they have built by hand is now a service running in the cloud.
Fear of the future is caused by the unknown. And I hope this guide has helped give you some knowledge on how the solution works. The value an EUC engineer provides the organization is learning and deploying new services that deliver a better user experience and increased security in a very flexible manner for your business. It’s not maintaining software components on servers as we used to years ago with VDI control planes on-prem. Those days are gone for many organizations as they embrace cloud-based services. If yours hasn’t already, it will at some point soon so it’s in your best interest to begin understanding these technologies now so you are better prepared for the future, either at your current company or some company you may be working at in the future. The last thing you want is to be told by a superior is that your org is moving its EUC control plane to the cloud and you’ve got a ‘deer in the headlights’ look. Instead, imagine yourself saying “Great! I know all about it!”. That’s a promotion right there.
I maintain a cheat sheet here called “The How to Build A Windows Virtual Desktop (VDI) Experience Properly Cheat Sheet” which at the time of writing this article has 55 considerations you need to be aware of that I’ve come across in my career building these types of environments for enterprises. Note, when I mean “Windows Virtual Desktop” in the title of this cheat sheet, I don’t mean the Microsoft solution. I mean a general Windows-based virtual desktop experience. Yeah, even generalized that’s 55 considerations. So don’t worry, your job is not going anywhere. Sure there’s a learning curve with the WVD solution, especially as Microsoft is releasing features for WVD at this velocity as are the partners that extend WVD value. Over time, the solution is going to get easier and ultimately make your life easier as an EUC engineer. We are all learning all the time.
In my next set of articles I’m working on, I’ll explain how you are able to use your WVD entitlement with some of the partner solutions I referenced above you may already have an investment in.
When in Redmond…
…of course, you have to take a picture in front of the Microsoft sign! No trip is complete without it. 🙂 Love those leaves!

Also, this Microsoft Azure-powered Intelligent Kiosk powered by Microsoft Cognitive Services and Azure Machine Learning thought I was a Border Collie. It’s a weird feeling knowing the cloud I work on is quietly judging me, but I’ll take it! 🙂
I hope this article has helped you and feel free to leave a comment below if you have any questions or need clarification on anything I’ve covered.
Jason Samuel is a visionary product leader and trusted advisor with a proven track record of shaping strategy and driving technology innovation. With extensive expertise in enterprise end-user computing, security, cloud, automation, and virtualization technologies, Jason has become a globally recognized authority in the IT industry. His career spans consulting for hundreds of Fortune 500 enterprises across diverse business sectors worldwide, delivering cutting-edge digital solutions from Citrix, Microsoft, VMware, Amazon, Google, and NVIDIA that seamlessly balance security with exceptional user experiences.
Jason’s leadership is amplified by his dedication to knowledge-sharing as an author, speaker, podcaster, and mentor within the global IT and technology community. Recognized with numerous prestigious awards, Jason’s contributions underscore his commitment to advancing technology and empowering organizations to achieve transformative results. Follow him on LinkedIn.






Mikael Jones
March 2, 2020 at 3:38 PM
Awesome writeup! When it comes to Passwordless with Authenticator app and FIDO2 key, I assume your screenshots appear when you access the WVD portal and gets a list of available apps. When the user then starts an app, do they need to authenticate again or are they SSO’d?
Jason Samuel
March 2, 2020 at 4:06 PM
@Mikael, thank you! That is correct. If you use a private browser (so starting fresh with no prior login) and go to https://rdweb.wvd.microsoft.com/webclient/index.html you will see the typical AAD auth flow and be able to use Authenticator passwordless phone sign-in or FIDO2 key. Once authentication is completed then you will see the portal with icons for available apps and desktops. When the user starts an app, for Windows SSO to work you will need AD FS configured or they will be prompted to authenticate again. This is a limitation of the Windows OS, it does not understand OIDC (web authentication) natively and needs something in the middle to translate this authentication into something Windows understands and can use for SSO (certificate).
Mikael Jones
March 3, 2020 at 1:13 AM
Thanks for the detailed response. Is your guess we will get SSO (without ADFS) all the way once we get the Windows 10 Multii-session Azure AD joined (as mentioned they are working on)?
I’d also like to see the possibility to login using B2B accounts. We have many environments where we want external users (in other Azure AD) to login without requiring us to create users in local AD. I can’t find any solution for this in native Windows, even with ADFS, can you? The only solution I’ve found is using 3rd party Citrix Federated Authentication Service (FAS).
Andy Grover
March 3, 2020 at 12:50 PM
Hi Jason that’s a really excellent blog about WVD and I feel your excitement for what is possible. What are your thoughts on those organisations that have client/server applications and how they can integrate WVD with their on prem backend services ?
Jason Samuel
March 11, 2020 at 12:00 AM
@Mikael, it is hard to say but AD FS is not a PaaS service while everything else with WVD is. So it makese sense to do Windows SSO using PaaS instead of having to rely on an on-prem or IaaS based AD FS and CA. Ideally I would love to see Azure AD and some kind of CA-as-a-service capability in Azure to help with Windows SSO needs.
B2B accounts is a great ask. I get that a lot as well. Right now with most solutions you still need to create a shadow account in your primary Active Directory which is a bit of overheard even when used with Citrix FAS. It would be nice to see 3rd party accounts no matter the IdP work natively with a Windows login over a remoting protocol without the need for FAS or other similar solutions but I’m not sure how far we are from something like that.
Jason Samuel
March 11, 2020 at 12:06 AM
@Andy, thank you. That’s exactly what Microsoft WVD, Citrix VAD, VMware Horizon, etc. are designed to do. Keep the clients and servers in the data center in close proximity and just stream the visualization dow to the remote user. It’s a solid tried and true approach. Especially these days with Coronavirus and increased work from home policies many enterprises have adopted.
Mikael Jones
March 11, 2020 at 2:08 AM
@Jason: Thanks for your detailed response again. So when it comes to enable “federated” users to login, if you’re using only AD/AAD/RDS/WWD only, it seems you’re out of luck – they simply have to get their own local AD account. But if you’re using Citrix, you can use Citrix FAS, but this is complex (many servers/services involved) and in the end you still need to create a shadow account. Would that be the short conclusion as it looks today?
But it’s a very exciting area and I hope that we can see it evolve in the upcoming months, especially with WVD. I really hope they will start enabling Azure AD authentication and login with SSO – that would be awesome. Once that’s fixed I’m sure Azure AD B2B is not far away.
Andy Grover
March 11, 2020 at 11:57 AM
@Jason apologies I wasn’t clear in my question – the scenario I’m considering is a customer who moves their desktops to WVD (so they are in Azure) and they have client server apps where the back end app/database servers are in their own DC, either on-prem or with another IaaS provider but not in Azure. Is the connectivity now good enough to allow this with minimal latency, would you need some special connectivity into Azure, or could you just rely on Internet VPN etc.
Jason Samuel
March 11, 2020 at 5:51 PM
@Mikael Jones, yup you got it, that is accurate today.
@Andy Grover, when you move the desktops (clients) to Azure, the backend app/database servers should move as well. Azure, AWS, GCP, on-prem data centers are all data centers at the end of the day and you want to keep users, their clients, and servers/databases as close as possible to said data center for the best user experience. If you move the desktops to Azure, you still need Azure ExpressRoute or site-to-site VPN to your on-prem datacenter if the backend is there. Performance may or may not be acceptable, depends on the app and its tolerance with the backend. The actual ExpressRoute circuits themselves are very good and very low latency. It’s when you try to split the front end from the back end on some apps that problems occur. Some apps are chatty and need their database close by. WVD and its remoting protocol is for end-user to the virtual desktop running in Azure. It will not help you with virtual desktop to backend server latency issues. Most companies have moved to ExpressRoute to help with this and also usually have plans to move the backend servers/database into Azure to keep them close to the virtual desktops. Azure Site Recovery (ASR) is great to leverage for this migration purpose.
Arpit
April 14, 2020 at 9:34 PM
Hi, I have few questions related to WVD. Apologies if these questions are basic but u am new to this WVD/VDI technology
1. How Antivirus definitions gets updated in Non persistent VDIs , considering Antivirus Console is On Prem?
2 How Patching gets updated in Non Persistent VDI ?
3. Can we leverage SCCM from Onprem to deploy patches?
4. How Apps r being tested for W10 multisession and VDI readiness? Is there any specific tool available?
5. Apart from TCP Protocol , 443 port, is there any additional security layer while external user login to Azure To access their desktops? I have read above responses, but not clear.
Ranj
July 13, 2020 at 4:05 AM
Fantastic article. I have been learning a lot about WVD in the last few weeks but this article really put those pieces together, some great info here, thank you.
I did try to access the scaling script in the article, just to let you know the link has since expired and it gets a 404. The link again is here: https://docs.microsoft.com/en-us/azure/virtual-desktop/set-up-scaling-script
Thanks, great work, keep it up.
Sam Goud
October 14, 2020 at 4:24 AM
Jason, many thanks for this very informative and useful blog!
If I buy a Microsoft Action Pack Subscription will I be able to use WVD for personal learning purposes? MAPS contains RDS CALs, Win 10 licenses, O365 E3, but no Microsoft or Windows E3/E5 or VDA.
BR!
Mael
June 2, 2021 at 9:53 AM
Hi Jason,
Great write up.
I know I am a year and a bit too late but I cannot find the image: “Microsoft Windows 10 + Office 365 ProPlus” in the Marketplace… as it been removed or replaced?
Thanks, Mael
Suman
August 8, 2022 at 11:31 PM
Can you please publish article on how to use MSIX app attach with Citrix cloud?
I am eagerly looking for it.