A few months ago I was invited to speak at the FIDO Alliance‘s inaugural Authenticate conference by Citrix and the FIDO Alliance. A big thanks to Mark Howell and Andrew Shikiar for the opportunity to join them and share knowledge with the identity and access management community. When I started working with this strong passwordless authentication standard years ago I never thought I’d be presenting on real-world strategy integrating this standard into Fortune 100 ecosystems years later to so many people.
The FIDO Alliance is 260+ companies aiming to solve authentication challenges we all face daily and the body responsible for creating the FIDO2 open authentication standard that’s progressing the Internet forward. You might recognize a few logos: https://fidoalliance.org/members/. This is not companies getting together trying to sell you something. This is a consortium trying to positively change the world and make both your personal life and enterprise life secure and easy to use across the Internet down to your computing device using an open standard. FIDO2 is as groundbreaking for the Internet as HTTP going to HTTPS many years ago in my opinion. The session recordings are available for on-demand viewing I especially liked some of the stories from various organizations’ strong authentication journeys as well as what to look forward to with the FIDO2 standard coming soon. Fabulous speakers and it was a real honor to be a part of this inaugural conference.
Since this event, I’ve received a few questions on enabling strong passwordless authentication for Citrix delivered apps and virtual desktops. Citrix has always supported passwordless authentication in the form of smart cards (x.509 certificates) and this feature is widely used in many business sectors. Modern passwordless authentication with FIDO2 uses web authentication with an underlying core WebAuthn standard developed with the World Wide Web Consortium (W3C) is what many organizations are wanting to move to for a variety of reasons I covered in the session. Modern passwordless authentication capabilities using FIDO2 was a feature Citrix worked on very early as the standard was being established by the FIDO Alliance. Most of this information is covered in more detail in some of my previous articles as well so I won’t go too deep into the technicals. I just want to summarize the capability.
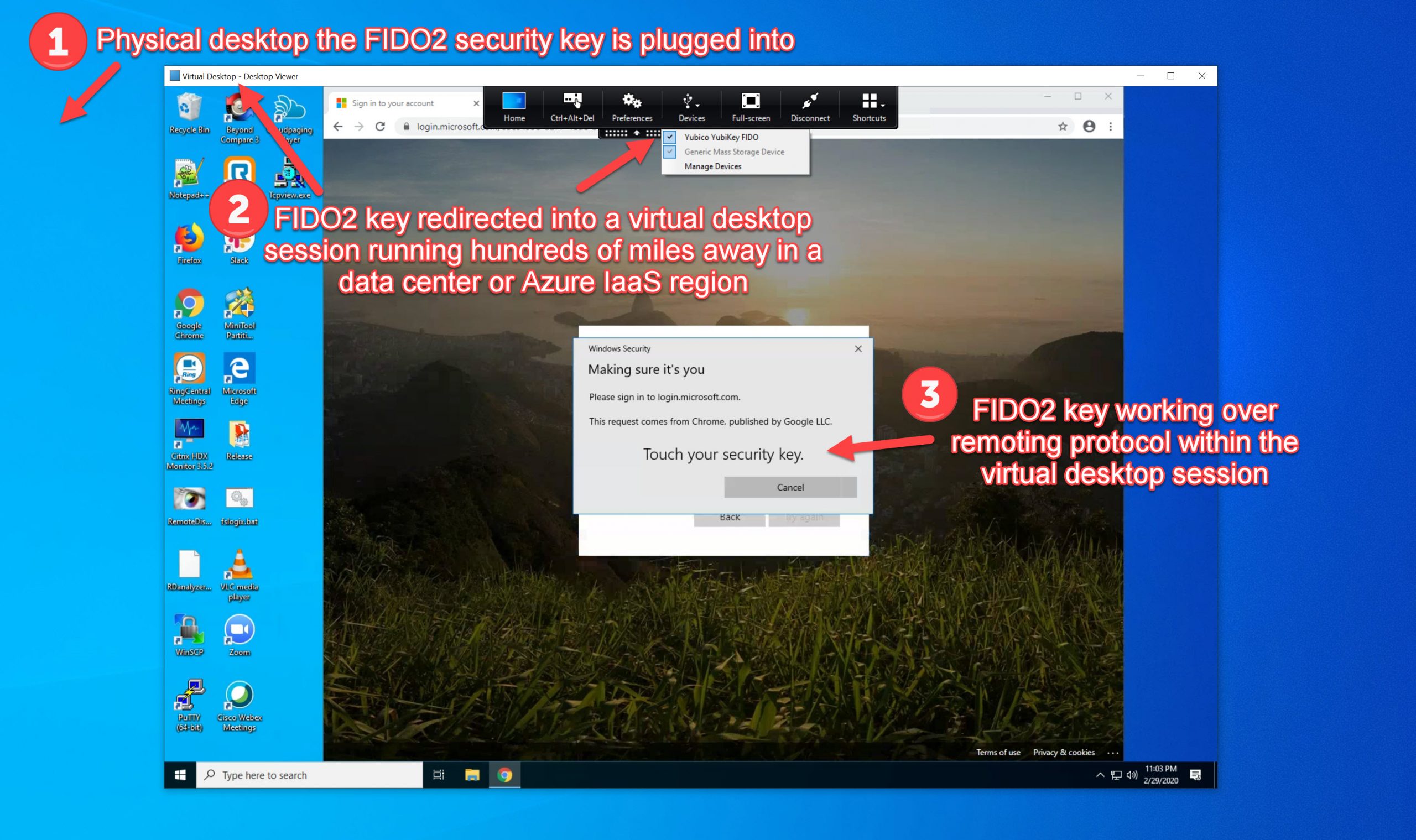
FIDO2 is fully supported on Citrix. Citrix Virtual Apps and Desktops Service in Citrix Cloud is the modern end-user computing offering from Citrix and should be the core of your hybrid multi-cloud EUC strategy since things you need to deliver to your users can be on-prem in your datacenters all around the world or any cloud provider. CVAD Service is designed to have leading-edge features that your security organization is interested in including 1-click enabling authentication with modern cloud identity providers. On the front end, CVAD Service and the Citrix Workspace can integrate with any FIDO2 capable identity provider such as Azure Active Directory or Okta for example and I’ve written several articles demonstrating this. It is usually preferable to use OIDC (OpenID Connect) but any SAML 2.0 capable identity provider can be added to Citrix Workspace in minutes as well. For the remote virtualized Windows desktop and server OSes, Citrix FAS translates modern web auth into just-in-time generated certs to complete the Windows SSO seamlessly for end-users. Lastly, and the newest innovation, Citrix created an optimized virtual channel for HDX so your client machine’s Windows Hello fingerprint reader, IR web camera, as well as FIDO2 hardware security keys you plug-in or use wirelessly with Bluetooth can be passed through into the virtualized Windows OSes and be used within the remote virtual session that is running hundreds of miles away in a datacenter or cloud region. And there will be even more innovations coming as the FIDO Alliance continues to evolve the standard. To summarize a few of these capabilities point by point:
- You can use FIDO2 to login to remote Windows servers, desktops, and Windows applications since Citrix Workspace will integrate with any FIDO2 capable identity provider. FIDO2 is composed of 2 underlying technologies called CTAP2 and WebAuthn. As long as the client device you are on (your laptop, phone, etc) supports CTAP2 (Client to Authenticator Protocol) you are in good shape to authenticate with any WebAuthn supported identity provider or service. Many enterprise identity providers, as well as consumer services, support it already and the list is growing every month. Your device needs to have Windows Hello for Business enabled or you must use a plug-in or wireless FIDO2 hardware security key or card when logging into Citrix Workspace.
- Post login after you have launched a remote session, you want to use your authenticator for other purposes just like you would any other computer peripheral. The Citrix session will pass through your local authenticator down into the remote system via an optimized WebAuthn HDX virtual channel. Not only the built-in authenticator in your laptop and plug-in USB ones but also wireless authenticators using Bluetooth and NFC. The list of supported OSes includes Windows 10 single session and multi-session virtual desktops as well as Server 2019 multi-session published desktops and apps for example. So any desktop or server OS can be used as soon as you install the latest Citrix VDA on them.
- Citrix allows you to use FIDO2 with ANY Windows application instantly. This is very important to understand. This means anything from your brand new Windows apps or SaaS apps all the way down to your legacy 20+ year Windows apps everyone is afraid to breathe on because there is no support but it still somehow makes your company millions of dollars a day. YOU DO NOT need to modify anything on your Windows apps to make FIDO2 work with them. Citrix does the heavy lifting for you and your Windows apps continue to use Kerberos on the back end completely oblivious. It’s instant passwordless authentication for your ENTIRE end-user computing environment when you use Citrix Workspace with FIDO2. A lot of my recent conversations have been around organizations just realizing they can protect their entire end-user computing estate with passwordless auth in minutes and not with some several months to years-long project.
- Citrix has a custom virtual channel to handle both Windows Hello for Business and FIDO2 WebAuthn channels. Web authentication is what modern passwordless authentication is built on. Deep dive into it here: https://www.jasonsamuel.com/2020/11/11/a-deep-dive-into-the-citrix-hdx-fido2-and-windows-hello-optimized-virtual-channel-with-virtual-desktops-and-apps-using-usb-nfc-ble-and-built-in-authenticators/
- You can use FIDO2 and smart card certificates concurrently with the same FIDO2 hardware security key if it supports multi-protocol (such as on a Yubico YubiKey 5 series key as one example). This helps bridge modern passwordless and legacy passwordless for environments that are transitioning from x.509 certs to FIDO2 and Windows Hello for Business. Citrix supports it all. You can even use Citrix virtual apps or the Citrix Gateway Service SaaS functionality if you need to extend certificate management safely to external users for self-service onboarding of certificates to these multi-protocol FIDO2 keys.
I hope this quick summary of these capabilities helps with your own conversations and feel free to leave any questions below.





xd
March 22, 2021 at 3:17 AM
Hi
is it planned for citrix to use Fido with Netscaler ?
thanks
Jason Samuel
March 24, 2021 at 4:01 PM
Hi, for FIDO you can use the newer FIDO2 standard (usernameless/passwordless via security key) and the older FIDO U2F standard (username + password + security key as 2nd factor). Just make sure you are using OIDC or SAML as the IdP configured with Citrix ADC (NetScaler) and that it supports these standards. FIDO2 is preferred and your IdP may refer to it as FIDO2 or WebAuthn in their console.