FIDO2 is as groundbreaking for the Internet as HTTP going to HTTPS many years ago in my opinion. Right now there is a consortium of 260+ companies you may recognize trying to positively change the world and make both your personal life and enterprise life secure and easy to use across the Internet down to your computing device using this FIDO2 open standard. Just as SSL 1.0 has evolved over the years to TLS 1.3 that much of the Internet relies on today, FIDO2 is actually the natural progression of many specifications over the years and will have the most monumental positive impact for you and your end-users. FIDO2 is not a fad, your users will begin using it without even knowing it if they haven’t already! FIDO2 doesn’t mean just physical security keys! That brand new Windows laptop you just issued to a user is a FIDO2 authenticator. So as a good steward of your IT environment, it is best to understand and begin moving toward FIDO2 today so you can support this modern open standard across any form factor and across your wholistic computing environment.
I wrote about how to extend your FIDO2 security key from your client device to your virtual desktops and apps running 1,000s of miles away in a public cloud provider like Azure or your private datacenter here:
Well, I’m happy to tell you Citrix has been innovating like crazy and now has an optimized HDX virtual channel for FIDO2! This is incredible because it supports more than just USB! You can now use USB FIDO2 keys, NFC FIDO2 keys, Bluetooth FIDO2 keys, employee badge form factor FIDO2 keys, and Windows Hello for Business meaning your laptop’s built-in fingerprint reader or IR camera for fingerprint or face logins! ANY AUTHENTICATOR. ANY DEVICE. ANYWHERE!
Requirements
Here are the requirements based on my testing:
- Windows 10 1909 minimum, 2004 or greater is the best
- VDA 2009 or greater
- Workspace app 2009.5 or greater
- Machine Catalog functional level VDA version set to 2003 or higher
- Citrix FAS so you can complete Windows SSO without a password during virtual desktop or app launch. If you need config help here’s my deep dive FAS article.
- Citrix Cloud Workspace with Azure Active Directory set as the identity provider
- In the VM, works with all browsers: new Chromium Edge, old Edge, Chrome, Firefox, Brave
- Citrix Cloud-based Monitor (Director) won’t show this new virtual channel yet, but it is there and working great!
And of course, have a Windows Hello for Business enrolled laptop or a FIDO2 security key. Here are some of mine that I’ve personally tested and all worked great with Citrix Cloud-powered Citrix Workspace and Azure AD:
Pictured from the top row to bottom with a penny for size comparison:
- HID Omnikey 5022 CL contactless USB reader with HID Crescendo C2300 FIDO2 smart card employee badge
- Feitian All-In-Pass K33 Bluetooth and NFC FIDO2 biometric security key
- Yubico YubiKey 5 NFC FIDO2 security key
- TrustKey Solutions (eWBM) G310 USB FIDO2 biometric security key
- Feitian BioPass K26 USB-C FIDO2 biometric security key
- Ensurity ThinC-AUTH FIDO2 biometric security key
- HID Crescendo USB FIDO2 security key
- Yubico YubiKey 5Ci USB-C and Apple Lightning FIDO2 security key
- Feitian BioPass K27 USB FIDO2 biometric security key
Configuration
None! Unlike my FIDO2 using USB redirection method, this new optimized virtual channel simply works out of the box. There is no configuration involved to get it working. Just make sure if you were using my USB redirection rules in my previously mentioned article that you have turned off that HDX policy. It is no longer needed with this new optimized virtual channel.
FIDO2 inside the virtual desktop session
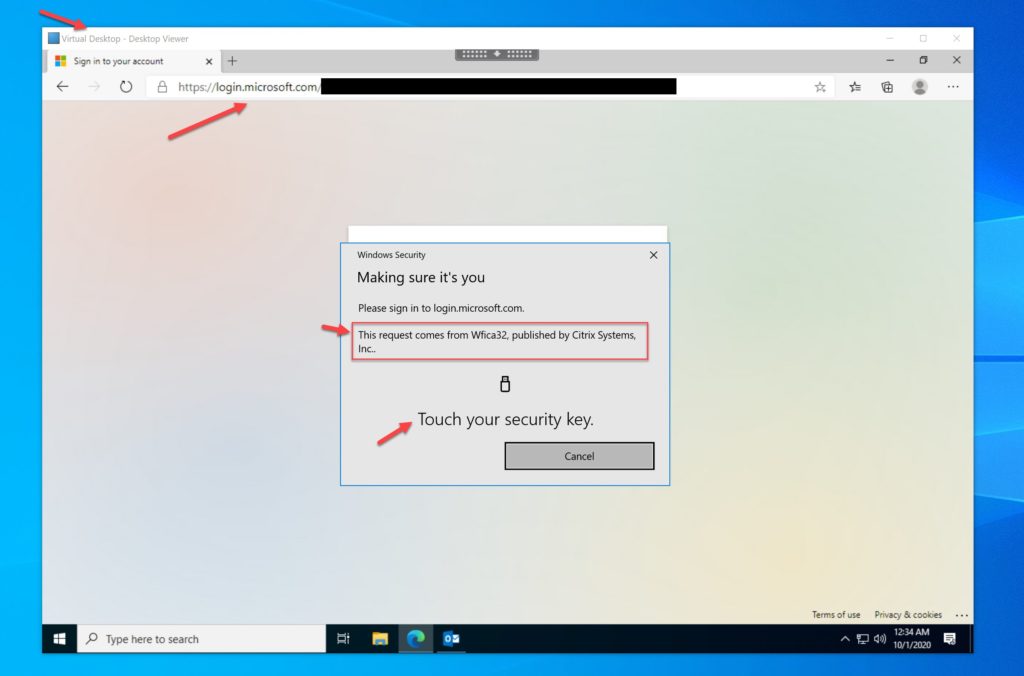
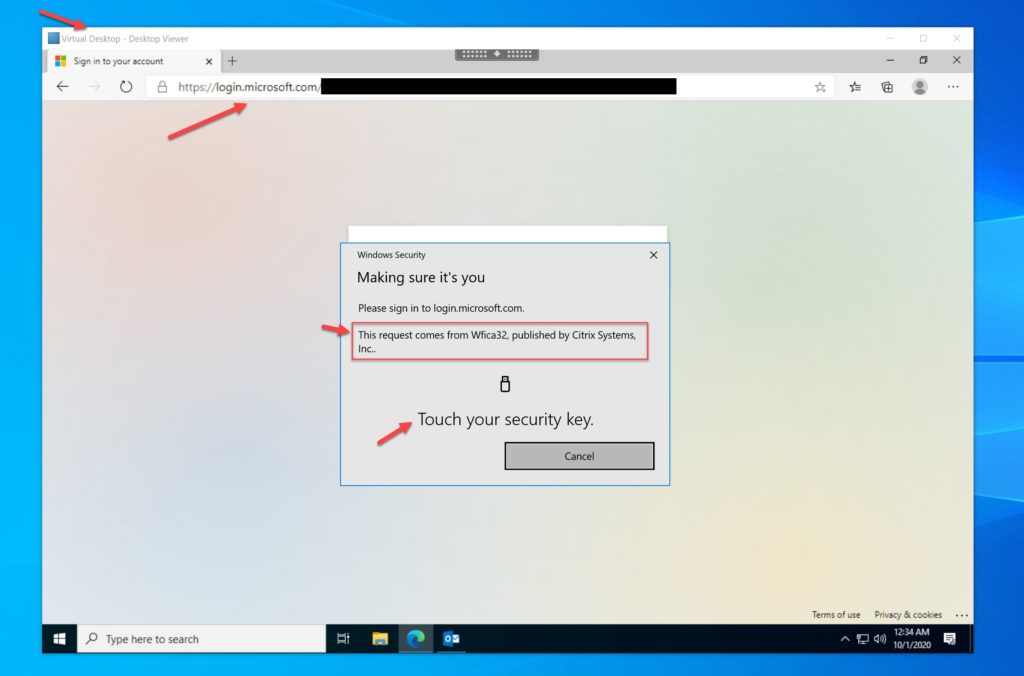
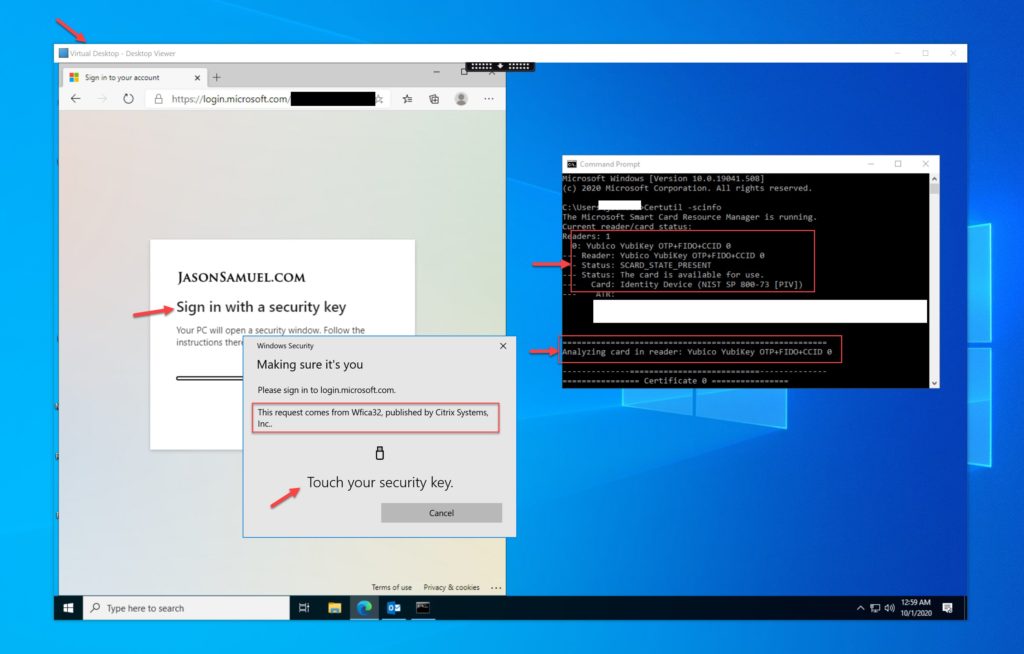
After you launch a Citrix virtual desktop or virtual app, if you have a Hybrid Azure AD Joined (HAADJ) VM you may not get prompted to authenticate within the session for Azure AD protected services due to the PRT (primary refresh token). This will depend on your exact configuration. If you do not use HAADJ VMs or your configuration does indeed require AAD authentication against an AAD protected website within the session, you will notice you can now use the FIDO2 key plugged into your computer within the session. It works extremely well.
This is a little bit different from USB redirection because this prompt is actually coming from your physical machine on behalf of the Citrix Workspace app. This is why the prompt is saying the request is on behalf of Wfica32 published by Citrix Systems Inc. You can actually drag around the Windows Security prompt asking you to interact with FIDO2/Windows Hello outside of your virtual desktop session because it’s actually coming from your physical machine and being translated down the FIDO2 optimized virtual channel.
The interaction from the Citrix Workspace app down the optimized virtual channel is using the client machine’s Windows core OS capability behind the scenes. The previous USB redirection based method I had demonstrated was much more of an all or nothing blunt instrument. Good for peripherals but not for multiprotocol authentication devices. This new capability is much more refined with the ability to use multi-protocol FIDO2 keys and ensure that FIDO2 and smart card/certificate/PIV functionality go down their respective virtual channels from that single key. Very innovative indeed, kudos to the Citrix team responsible for creating this functionality!
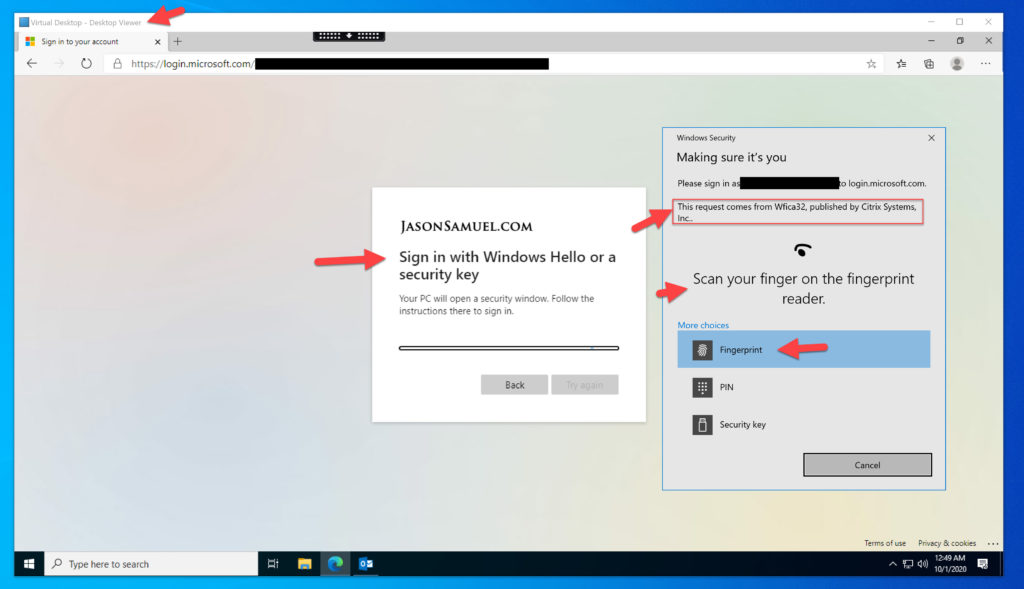
Windows Hello for Business inside the virtual desktop session
Windows Hello for Busines works equally well! Yes, that trust you’ve created between your laptop’s TPM chip (trusted platform module) and Azure AD is now extended into the virtual desktop session! You can see here in my screenshot I can use the fingerprint reader on my laptop within the virtual desktop session. If you have an IR camera on your laptop or external USB webcam that supports Windows Hello and can be used with your desktop/laptop like the Logitech Brio 4K webcam, you can use those as well:
FIDO2 and PIV (x.509 certificate) concurrently inside the virtual desktop session using multiprotocol FIDO2 USB keys
The best part about this FIDO2 optimized virtual channel is that it does not compete with the smart card optimized virtual channel. You can simply plug-in your multiprotocol key (like the YubiKey 5 NFC) with a certificate on it and enrolled in Azure AD, it will just work out of the box. The x.509 certificate for PIV functionality will be available in the virtual desktop session using the optimized smart card virtual channel and the FIDO2 functionality will be available using the optimized FIDO2 virtual channel.
Inside the virtual desktop session, open up a command prompt and type in:
|
1 |
certutil -scinfo |
which will enumerate the certificates on your multiprotocol FIDO2 key that is plugged into your physical laptop or desktop. As you can see in this example it is returning the Yubico YubiKey with OTP+FIDO+CCID which means all interfaces are enabled. Notice how the status is “the card is available for use” and NIST SP 800-73 (PIV) is specially called out. This means you’re in good shape! If you scroll down in this window you will see details on all the certificates installed on the YubiKey.
My screenshot here is inside the virtual desktop session, with FIDO2 happening on the left and the YubiKey with certificates being enumerated in the command prompt on the right. Isn’t that amazing! Modern web auth + legacy certificate auth at the same time! This is the true bridge for passwordless strong authentication for many state and federal government agencies and large organizations that depend on certificate auth but need something more modern with more user-friendly form factors.
Additionally, I want to point out that if you use the OTP feature of a YubiKey that will also work natively here as well in the session just like FIDO2 and PIV. Open up Notepad and then press the YubiKey. It will generate and paste a 44 character OTP into Notepad like this. Here I’ve pressed it 3 times so it has generated 3 unique OTPs into Notepad inside my virtual desktop session:
How the FIDO2 optimized virtual channel works under the hood
This new capability is designed to work with the following web browsers inside the virtual desktop or virtual app VM:
- Edge (Chromium-based)
- Edge (old)
- Chrome
- Firefox
- Brave
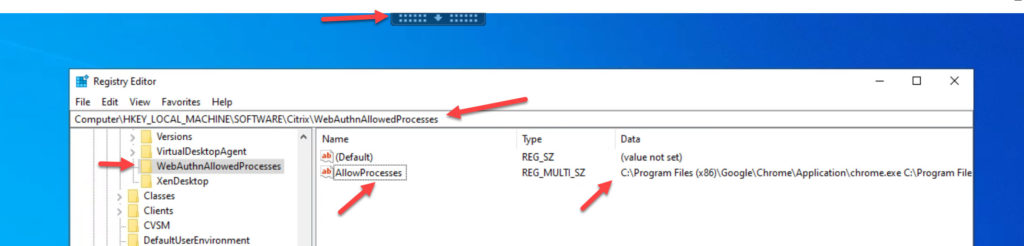
On the VM with the VDA installed, you will notice a new WebAuthn registry key at:
|
1 |
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\WebAuthnAllowedProcesses |
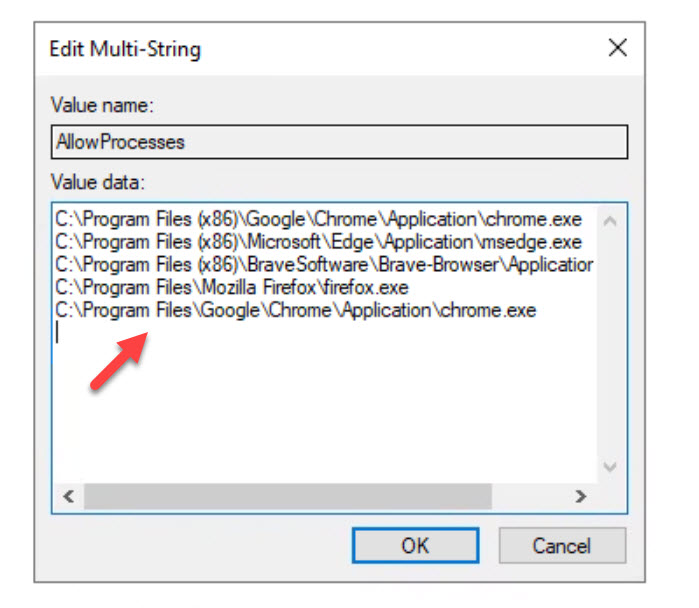
Double click on the “AllowProcesses” multi-string value and you will notice it will include the paths for the following browsers by default:
|
1 2 3 4 5 |
C:\Program Files (x86)\Google\Chrome\Application\chrome.exe C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe C:\Program Files (x86)\BraveSoftware\Brave-Browser\Application\brave.exe C:\Program Files\Mozilla Firefox\firefox.exe C:\Program Files\Google\Chrome\Application\chrome.exe |
This is how the VDA whitelists the installed web browsers to where they can talk down the optimized virtual channel to your physical endpoints with your FIDO2 key/Windows Hello and the Citrix Workspace app on your physical endpoint.
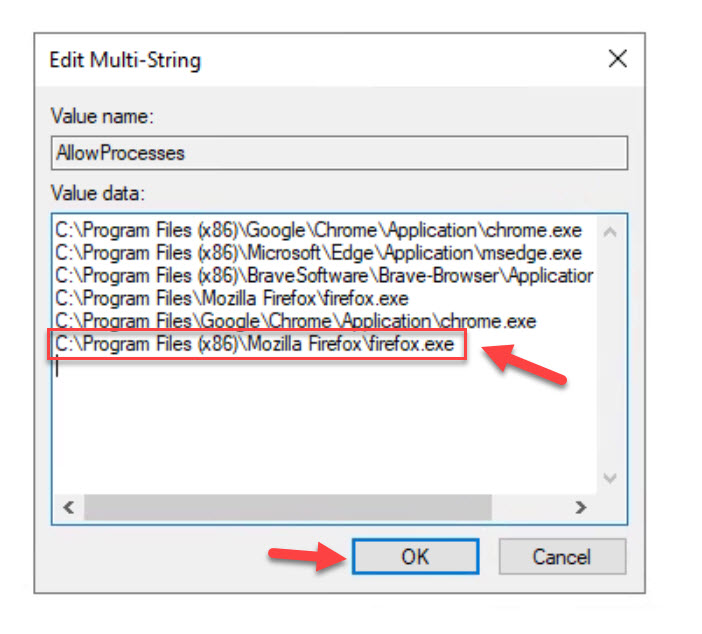
If you need to add additional browsers or change your install path, just add a line to this value. In my case, my Firefox was up to date and 64 bit yet it was installed here to an x86 path (likely due to an older installer) so I had to add an extra line for it:
|
1 |
C:\Program Files (x86)\Mozilla Firefox\firefox.exe |
You do not need to restart the VM or relaunch your session. This will take effect immediately after you close and re-open the browser you just whitelisted inside the virtual desktop session.
Additionally, as with many persistent virtual desktops or Remote PC machines out there, Google Chrome if downloaded by the user will allow the user to install Chrome even without local administrator rights. It will install into the user’s AppData folder. If you install Chrome as a local administrator as you normally would when creating a master image, this is not an issue and it will install to the default Program Files folder. This particular VM I was testing on had Chrome installed on the fly by a non-local admin account to the AppData folder. When I attempted to whitelist Chrome as a test, it would not work with this path:
|
1 |
C:\Users\username\AppData\Local\Google\Chrome\Application\chrome.exe |
The solution was easy. Simply un-install Chrome and re-install it with local admin rights. It will install to the Program Files folder and the default paths that the VDA installed will work. Don’t worry, your history, extensions, etc. will all persist when you uninstall and re-install Chrome so there is no loss in productivity if you ever have to do this for a persistent desktop user or Remote PC user.
Another question you may ask is what about native Windows apps that use web views for authentication? Some of them may call on the local default browser and some may come with their own embedded Chromium browser. These will need to be whitelisted at the process level here as well with one additional key at:
|
1 |
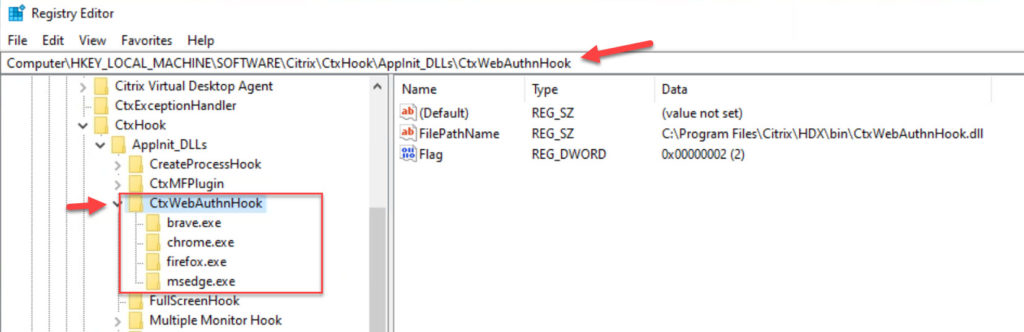
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\CtxHook\AppInit_DLLs\CtxWebAuthnHook |
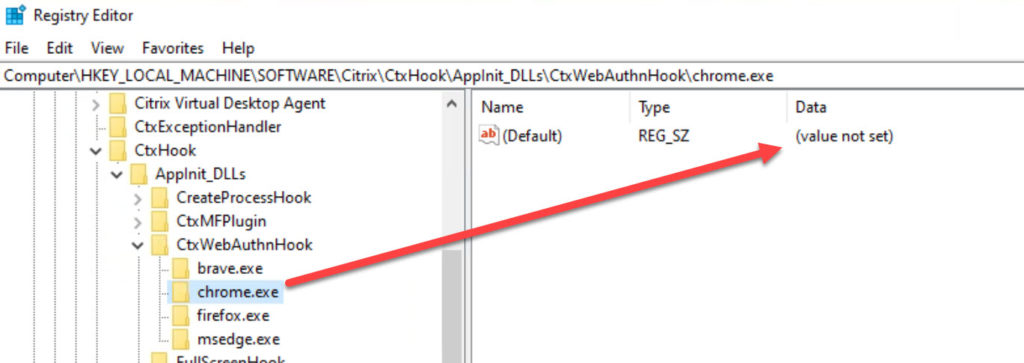
You will notice each process has a key created under the CtxWebAuthnHook key. The ones that are in there by default are very simple with no values. If you have additional browsers or native Windows apps, all you need to do is add a key for the process name and leave the value empty. Here is an example of the chrome.exe key:
Some native apps I tried call on other processes. A great example of this is the WVD client or Teams which I have installed inside my virtual desktop. They use the Microsoft.AAD.BrokerPlugin.exe to do the web view to login to Azure AD. This is located at
|
1 |
C:\Windows\SystemApps\Microsoft.AAD.BrokerPlugin_cw5n1h2txyewy\Microsoft.AAD.BrokerPlugin.exe |
There is some additional work that needs to be done to whitelist this so I will expand upon this in a future article.
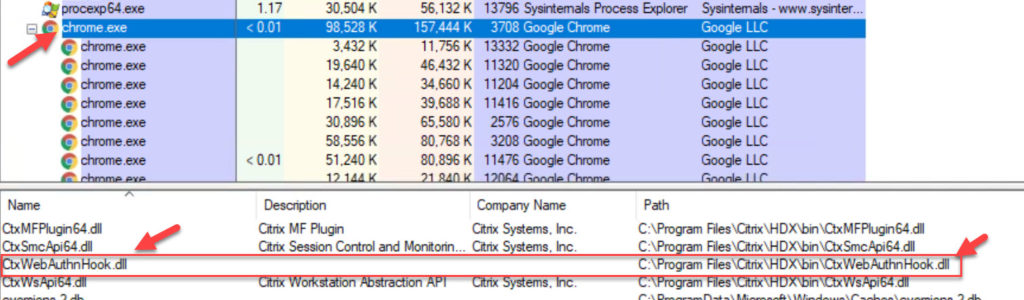
So now that we have our browsers whitelisted, how can we verify the Citrix VDA is actually hooking into these processes to allow for FIDO2/Windows Hello from the physical endpoint? Just use Process Explorer. Open Chrome and Process Explorer inside the virtual desktop session. In Process Explorer, click the main chrome.exe process. Then in the toolbar click View > Show Lower Pane. Then hit the toolbar again and click View > Lower Pane View > DLLs. In this list at the bottom, you will see “CtxWebAuthnHook.dll” which is the Citrix WebAuthn Hook DLL. This means that the process is hooked into the optimized virtual channel and can talk to the external or platform authenticator from your physical machine:
FIDO2 authentication using web browser vs. Citrix Workspace app differences
I want to clear this up for everyone as I know there’s been a little bit of confusion and I’ve helped clarify this on Twitter. The release Citrix has done here is for the FIDO2 optimized virtual channel. It does not add FIDO2 for the Citrix workspace app login itself.
However, if you are using Windows 10 2004 on your laptop or desktop, you will see a web view if using Azure AD. You may think it works just like a web browser login but it does not. There is a workaround I want to share until we see Citrix release the full FIDO2 login flow capability.
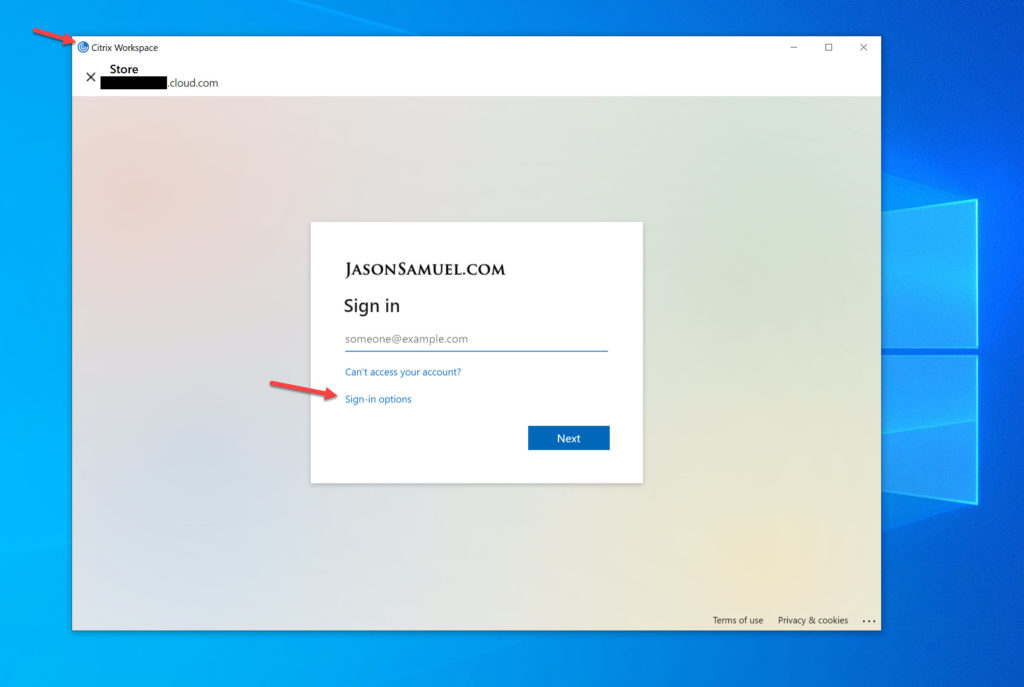
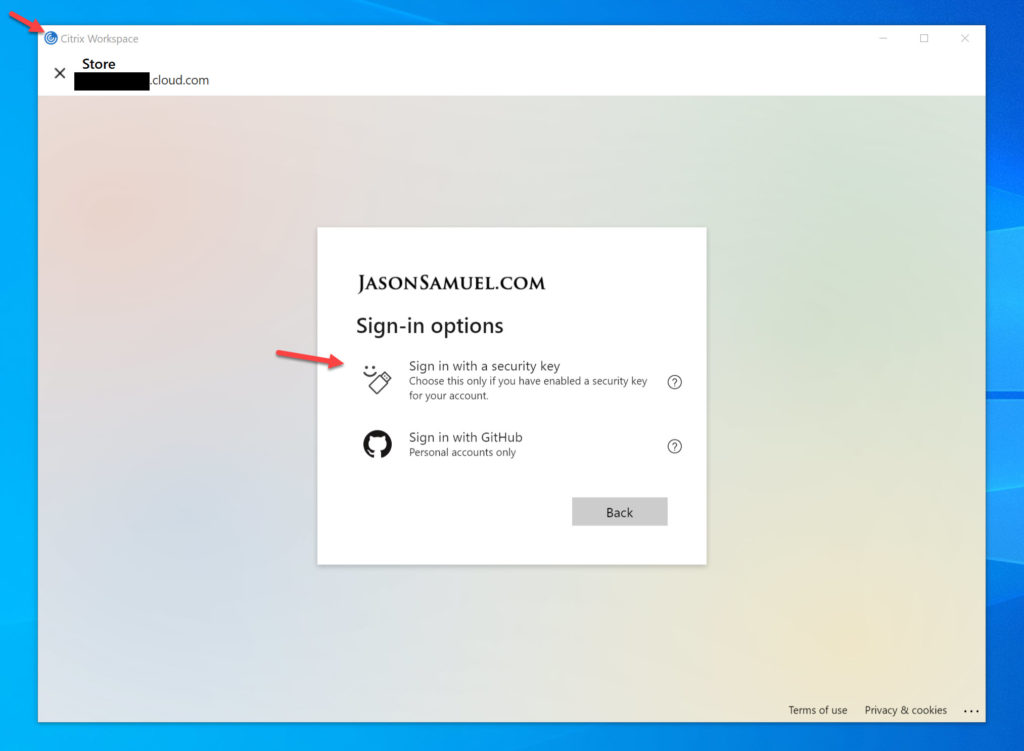
1. Go to Sign-in options as you do in a web browser for the full user name-less and password-less FIDO2 experience:
2. Choose sign-in with a security key or Windows Hello (what the Azure AD verbiage will say here will depend on your computer’s capability as I’ve explained in previous articles):
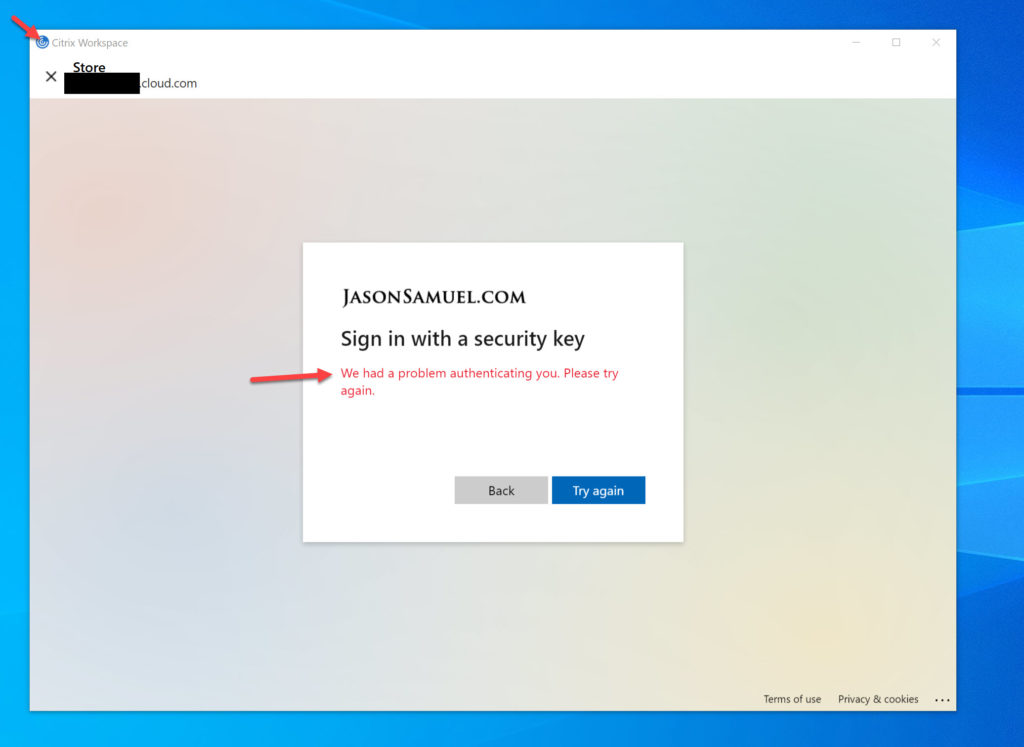
3. You will notice instead of the expected Windows Security prompt to interact with your FIDO2 key, you will instead see this red error message saying “We had a problem authenticating you. Please try again.”
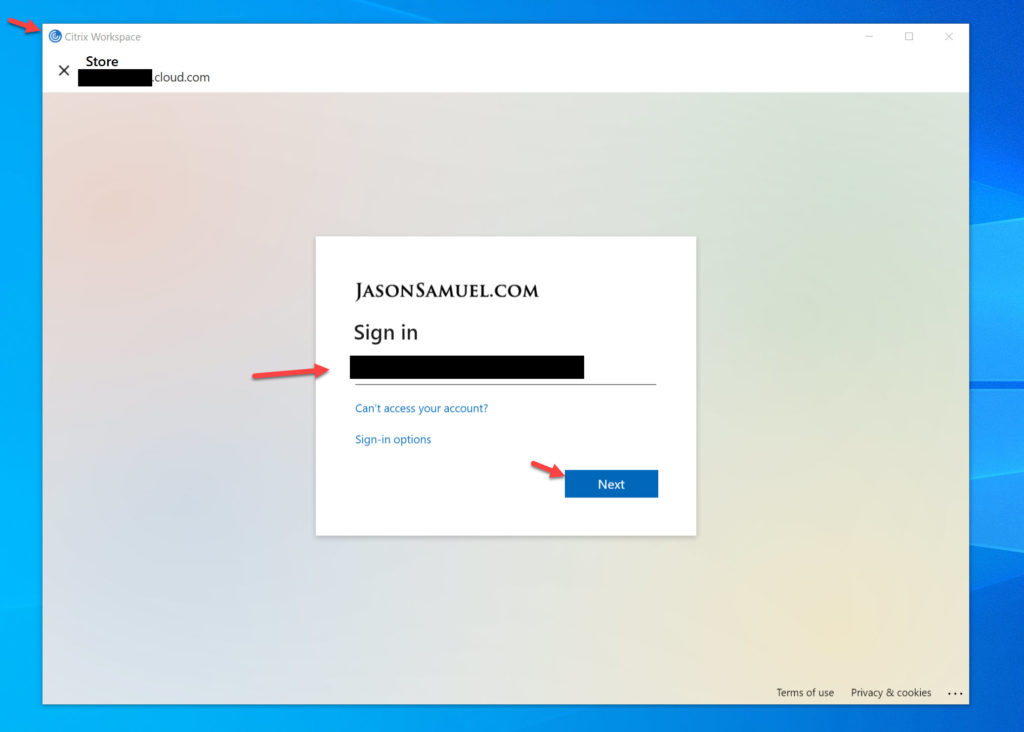
4. Yeah I know, it’s a different user experience that in a web browser and I do expect Citrix will release the full FIDO2 login flow soon that matches the web browser login experience. However, for now, I have a workaround for you. Hit the back button and enter your email address (your user name). I know it’s not the ideal FIDO2 experience but it is a good workaround for now. Hit Next to proceed.
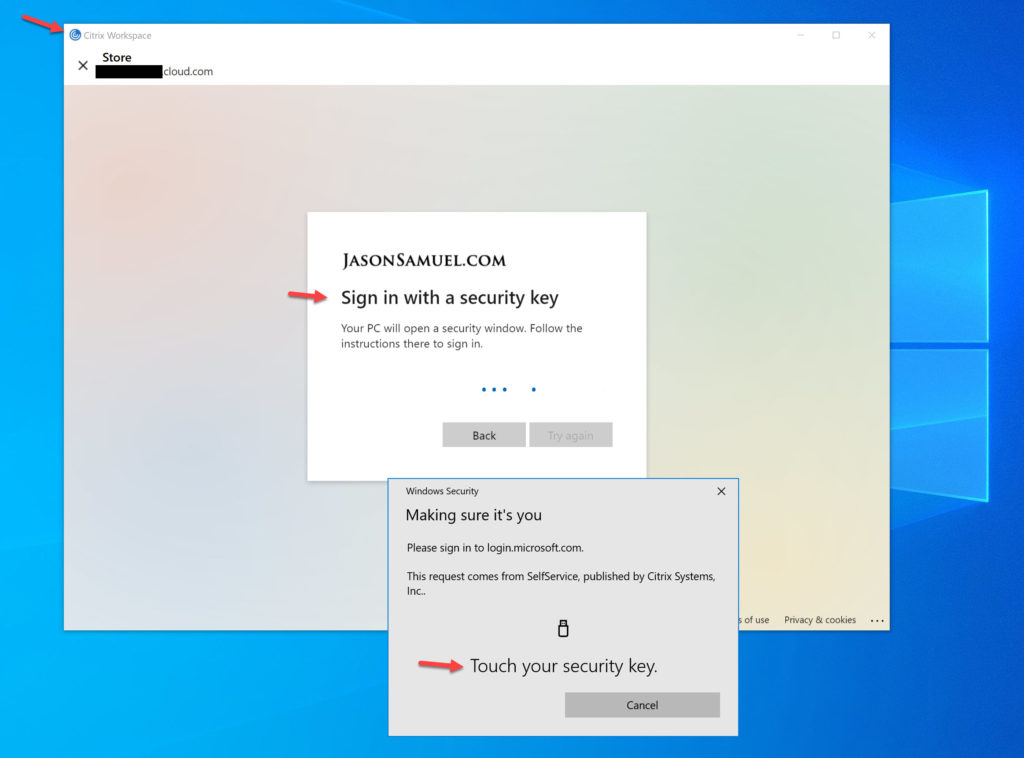
5. And look at that, the FIDO2 key works with the Citrix Workspace app login flow!
6. You may ask if Windows Hello for Business can be used with the Citrix Workspace app login flow as well like the FIDO2 key I demonstrated above. Unfortunately, the answer is no at the moment. No native applications I’ve tried such as the WVD client, Teams, Citrix Workspace app, etc. will work with Windows Hello. There appears to be some kind of hook between the Windows 10 core operating system and the web views used for Azure AD by native web applications that is missing something as I’ve covered in a previous article. I expect a future Windows update should bring this capability.
So for now:
- LOGIN = You can use Windows Hello for Business for the authentication portion using a web browser only, but a FIDO2 security key can be used in both the web browser and the native Citrix Workspace app.
- IN-SESSION = After you have launched a virtual desktop or virtual app session you can use Windows Hello for Business or a FIDO2 security key within the session with no issues down the new optimized virtual channel. What you authenticated with into the Citrix Workspace app has no bearing on what you can use inside your virtual desktop or virtual app session. Two completely different things. Hope that clears things up for everyone.
Monitoring the FIDO2 optimized virtual channel
At this moment, neither the Citrix Cloud-based Monitor (Director) nor the standalone HDX Monitor tool is aware of the FIDO2 optimized virtual channel. I do expect both will get the ability to view the FIDO2 virtual channel similar to how you can view the smart card virtual channel today.
Final Thoughts
It’s just incredible to me all FIDO2 form factors and Windows Hello are now available in a virtual desktop session! Any future FIDO2 key released by a manufacturer will automatically work with virtual desktops and virtual apps since it’s all based on a standard that Citrix is conforming to and presenting to the remote session, an excellent design approach for this feature. With COVID-19 and everyone depending on high identity assurance as part of their zero trust strategy in their remoting environments, having the ability to authenticate and use a strong authentication mechanism like FIDO2 keys and Windows Hello for Business is paramount. That’s your true perimeter. That high identity assurance is the difference between productivity for the end-user vs. a very bad day for your IT department and potentially millions of dollars in impact from a breach, data exfil of intellectual property, tampering, or whatever an attacker may be able to do via your end-user computing remoting environment.
A big kudos to the team at Citrix for getting this out so fast and making it so easy to use for end-users. An especially huge shout out to Jason Vega and Mark Howell for the many hours of feedback sessions and for giving me an opportunity to test out this capability early throughout this year. Any Authenticator, Any Device, Anywhere. This is the kind of stuff that truly changes how people work and I’m thankful to be able to share all this with the community.
Jason Samuel is a visionary product leader and trusted advisor with a proven track record of shaping strategy and driving technology innovation. With extensive expertise in enterprise end-user computing, security, cloud, automation, and virtualization technologies, Jason has become a globally recognized authority in the IT industry. His career spans consulting for hundreds of Fortune 500 enterprises across diverse business sectors worldwide, delivering cutting-edge digital solutions from Citrix, Microsoft, VMware, Amazon, Google, and NVIDIA that seamlessly balance security with exceptional user experiences.
Jason’s leadership is amplified by his dedication to knowledge-sharing as an author, speaker, podcaster, and mentor within the global IT and technology community. Recognized with numerous prestigious awards, Jason’s contributions underscore his commitment to advancing technology and empowering organizations to achieve transformative results. Follow him on LinkedIn.
Disclaimer: Views expressed here are his own and do not reflect the views of his employer, past or present, or any organizations he is affiliated with. Content is for informational or personal purposes only.






Michael
May 20, 2021 at 12:59 AM
Hi Jason, great article, i’ve switched from the redirection method to leverage the new fido2 virtual channel but have hit issues with native apps, particularly teams, are you able to expand on the complexities around whitelisting Microsoft.AAD.BrokerPlugin.exe?
Jason Samuel
May 21, 2021 at 3:13 PM
Hi Michael, yes this is still a challenge today but the team is aware. Will reach out to gather more info on your setup. It is helpful to hear from folks that need this capability. Very happy to see more people embrace FIDO2. 🙂
Miguel Rodriguez
December 16, 2021 at 4:01 PM
Hi Jason, quick question: is the FIDO2 HDX channel available also in ICA?
Richard Powell
January 27, 2022 at 5:30 AM
Hi,
Great article, has helped me a lot!
Have used your article to configure this for some of our security team testing MFA products, the YubiKey in our example.
First had it tested via Citrix Policy for redirection, then removed this policy.
Using this newer method now, we are unable to register the YubiKey via the Citrix VDA.
The issue we now see is without the redirection policy we are unable to resgiter the new security device via login.microsoft.com, do you know how to resolve this?
Andreas Mariotti
September 19, 2022 at 8:16 AM
Hi Jason,
I try to use a Yubikey5 with an certificate inside a Citrix HDX session, the Yubikey is in PIV mode, FIDO2 & OTP is disabled via Yubikey Manager, Citrix DCs and VDAs are running on 1912 LTSR CU5, VDAs and clients are running Win 10 2009 and Citrix Workspace App version is 2207.
The smartcard is redirected into the HDX session but access to the smartcard is not working as expected. “certutil -scinfo” shows always “SCARD_STATE_INUSE The card is being shared by a process” and I don’t get prompted for the PIN and get other consequential errors.
Your article is about the Citrix version 2009 because of the new FIDO2 support, but I use PIV only and FIDO2 is disabled, I would expect this to work even with 1912, but it doesn’t. Do you think my problem is related to my slightly older Citrix version, or any idea what the problem could be?
Dmitry
January 7, 2023 at 11:26 AM
Another great article. Thank you for sharing with community.
Quick question about browser security popup while inside Citrix session. I have YubiKey redirecting just fine through Citrix (using your article), but occasionally web browser security popup never comes up. Even if I use Yubico.com demo page, which should popup even without keyfob being plugged in. I can’t figure out what is blocking it. I could get a prompt when physically connected to same system and session andif Citrix into it from internal network from say a thin client or another system. If I Citrix in over Netscaler, security prompt never shows up and I get a timeout error. Already tried enabling all Citrix vchennels. But again, this prompt typically comes up regardless of the keyfob being plugged in or redirected. And does work if I reconnect to same session over intranet and use same web browser process (same pid). Are there any web browser policies that could be blocking webauthn prompts in the web browser that are not covered by the article?
Kaleem
April 26, 2023 at 7:54 PM
Hi Dmitry, I’ve the same issue popup not coming up. Did you solve yours? What is the solution? I have 2022 server and windows11 client. AAD auth works on physical machine but not with published rdp app on Xenapp farm. Thx
Cesar Reyes
December 14, 2023 at 12:51 PM
I’m with Richard Powell and Andreas Mariotti. Things work if I do it the USB redirection way, but not with the FIDO2 virtual channel.
Environment:
Citrix Cloud for Delivery Controller/Studio
VDA 2203 LTSR CU4 on the clients.
YubiKey 5 series with only the FIDO2 interface enabled.
Web browsers can detect when I touch the YubiKey, but I get a “OOps!… The operation either timed out or was not allowed. See:…” when testing using demo[.]yubico[.]com/webauthn-technical/registration, and I get a “We couldn’t verify you or the key you used. If you are using a security key, make sure this is your key and try again” when I try to log in to Microsoft 365 using a web browser and an already registered Yubikey.
I started a case with Citrix support and after sending them screenshots and even videos of the Yubikey working on a physical Desktop but not on a virtual Desktop, their response so far is “we’re stumped”.
Any help/guidance is appreciated.