Every month it seems more and more organizations are embracing modern passwordless strong authentication in their end-user computing environments. Just in the last 3 months, I’ve noticed a significant uptick in people asking questions which is a great sign that passwordless authentication is being embraced by organizations. Recently I’ve had a lot of people ask me about smart cards when used with the Citrix Virtual Apps and Desktops Service in Citrix Cloud. I’ve written several guides now on using Yubico YubiKeys as well as many other manufacturers of FIDO2 security keys for modern passwordless authentication. Many of these FIDO2 keys are also backward compatible with smart card certificates (x.509 certificates) and can be used as a smart card replacement. I’ve even shown some smart cards that actually double as a FIDO2 capable employee badge. For example, the HID Crescendo C2300 is one that support both FIDO2 and PIV/x.509 smart card certificates as well as being NFC which means just wave over or lay on top of an NFC capable contactless smart card reader to login. No need to insert into a smart card reader. I have an HID OmniKey and Feitian Contactless Reader on my desk which are both great contactless smart card readers for those company’s respective cards/keys. Both of these readers also work well with other manufacturer’s keys like the YubiKey 5 NFC to read the x.509 certificates on it as well as use it for a pure FIDO2 contactless login by just laying the key on top of the reader. There’s a lot of great choices and capability out there so find what’s best for you.
My advice is to pick your favorite key, all FIDO2 security keys work great with Citrix and is how I have been logging into my virtual desktop daily since 2019! And the WebAuthn optimized HDX virtual channel extends FIDO2 capability into the virtual desktop session. FIDO2 is the passwordless authentication standard your organization SHOULD be using. However many orgs are still using legacy x.509 certificates since they have been around in Windows computing for over 24 years now (yeah, way back in 1997 with the PC/SC 1.0 specification and its backward compatibility down to Windows 95). They are much more secure than using passwords but also have many limitations for modern end-user computing. Some security keys like the YubiKey 5 series which I will use as an example today can support both FIDO2 and smartcard logon (x.509 certificates / PIV).
The focus of today’s article will be on the smart card functionality and how Citrix can help you reduce operational overhead by enabling you to maintain the lifecycle of your x.509 certificate compatible security keys remotely. While at the same time increasing your organization’s security posture by avoiding less than ideal workarounds when your users are remote. For example, you never have to worry about your remote workers with a close-to or already expired cert calling in that often leads to your IT Service Desk having to scramble and temporarily give them a password to login to a system. This reduces security now having to keep track of that temp password for a period of time when a human user knows it and make sure it actually gets scrambled again afterward in AD. Or how about the user friction that comes from having to mail the user a new security key with an updated cert which can have significant impacts on user productivity in the interim.
Many organizations may have had 1 year certificate expiration policies on authentication devices and are now approaching 1 year of these employees being out of the office working from home without line of sight to PKI infrastructure to perform certificate renewals. Organizations probably didn’t take pandemics and prolonged time away from an office network into the equation when establishing a certificate expiration policy which has made certificate-based authentication lifecycle a real challenge.
Accelerating modern passwordless authentication initiatives using Citrix and multi-protocol hardware security keys
If your organization is still using legacy passwordless authentication using smartcards (x.509 certificates) that’s okay, it may take some time to get your org to fully move to FIDO2. There needs to be a middle tier that can help fill the gap as users move from legacy PIV based authentication to modern passwordless web-based authentication. A lot of these orgs want to use multi-protocol FIDO2 keys that also support x.509 smart card certs which helps fill this gap. This puts the smartcard in a much easier to use USB form factor rather than a badge hanging off your hip that requires integrated smartcard readers in your laptops/desktops or USB smart card readers to work. We’ve done that for 24+ years, time to move on. If you’ve read my past articles, the whole “one key to rule them all” motto is very wise to bridge your orgs legacy auth with modern auth in an easy pocketable way for your users. There are both security keys and employee badges that are multi-protocol and can support FIDO2 and smart card x.509 certs together, I’ve written about several of these I’ve used to launch my virtual desktop through Citrix Workspace.
The key takeaway is you can have a single user using multiple form factors if they wish, leave the choice up to them that fits their work style. Don’t get hung up on the form factors too much. The more important thing for IT to consider is that those authentication devices the users are using provide high identity assurance every time they are used (using PIN or biometric). I won’t go into the difference between external roaming authenticators and integrated platform authenticators as I’ve covered that before but no matter what, you can use modern FIDO2 based standards in a variety of external or integrated ways. All the user has to do is remember a PIN or my favorite and what I use predominately with my FIDO2 keys and Windows Hello enabled laptop, a biometric (my fingerprint). A biometric has the highest identity assurance possible today making security teams happy and the highest user satisfaction with end-users because they make logging into things so incredibly fast/easy it feels like magic.
The biggest challenge is that many of your applications in your organization simply don’t understand modern web authentication and are still Kerberos based so you’re deathly afraid to touch anything to prepare them for modern web auth. If you talk to app owners they don’t want to re-engineer anything either. These apps could be responsible for bringing in millions of dollars into your business and there are much bigger priorities for the app teams than potentially breaking something by trying to enable modern web auth on them. The good news is, that’s okay. Citrix can help you instantly modernize all your legacy apps and you don’t need to touch them at all. You can choose to use x.509 certs or FIDO2 to login to the Citrix Workspace depending on the identity provider you choose to pair with it and from there Citrix FAS will help assist to seamlessly perform the necessary backend Windows SSO as users launch the remote apps and desktop so you don’t need to change anything on your existing systems. Instant secure webification of your Windows apps. Users use modern auth, apps continue using Kerberos, and the users have no idea because it’s all seamless to them. They think you’re a wizard.
I have helped advise several large organizations not only bridge the gap but accelerate their modern passwordless initiatives as a result of this Citrix functionality. It is a really nice feeling when you listen to the feedback from users and IT leadership at these companies on how happy they are using easy to use passwordless authentication. The success of many modern authentication projects was due to Citrix enabling the flexibility to use whatever authentication standard a user needs at the moment in time with whatever form factor authentication device and whatever form factor client they have in front of them. You can’t anticipate what each user in your org will need from day to day so Citrix coupled with a multi-protocol hardware security key solves that challenge for you.
When users are remote and spread all over the world, it’s hard to be able to get a YubiKey to talk to a Windows CA in order to get a cert on there. I want to show you the power of the Citrix HDX virtual channels that allow optimized smart card as well as modern auth with FIDO2 and Windows Hello for Business to communicate remotely with your other IT systems. Hopefully you can use some ideas demonstrated here to help simplify your smart card lifecycle leveraging your Citrix environment.
Mail your users a YubiKey and use Citrix to self-service a certificate onto them remotely
Citrix has an optimized smartcard virtual channel and a nice new WebAuthn virtual channel that supports FIDO2 and Windows Hello for Business. I’ve shown how easy it is to enroll a FIDO2 key remotely with a FIDO2 capable identity provider like Azure AD in the past so I won’t dive into that right now. Let’s focus on the smartcard virtual channel. If a user is remote which pretty much everyone is these days, you will need to mail them a YubiKey or have them purchase one from a retail outlet like Amazon. Then you need to expose your PKI infrastructure (Windows Certificate Authority) to them in order to enroll an x.509 certificate onto the YubiKey. Ideally you want it to be self-service so the user handles all this in their user context rather than having an administrator in your IT department manually touch each key and put a user cert on there for them prior to shipping to the user. In order to expose your CA, you would need to either setup a credential/card/certificate management system (CMS) or smart card management system (SCMS) portal and expose it to the Internet. Or you can sign up with a SaaS based smart card certificate management system service to extend the functionality of your Windows CA a bit more securely in a proxied fashion. This can be a one-off or a part of a larger certificate lifecycle management (CLM) system. All these options have a cost and there are not a whole lot of players in the PKI market that can do this in a modern flexible way that may fit all your business criteria.
The easier low-cost way is to simply use your Citrix environment to assist with onboarding YubiKeys for the remote users over the HDX optimized smart card virtual channel:
- On a Server 2019 VM with the latest Citrix VDA here in my example, I install YubiKey PIV Manager (https://developers.yubico.com/yubikey-piv-manager/Releases/). Please note that YubiKey PIV Manager is no longer actively developed on. However, I still use it because the successor YubiKey Manager (https://developers.yubico.com/yubikey-manager-qt/) does not have an easy GUI-based way to enroll certificates instantly from your Windows CA. The newer YubiKey Manager only allows self-signed certs and CSR-based cert creation in it’s GUI. I would actually recommend you install both of these on your VDA for testing purposes so you understand the capabilities of both as you test things. If you are script inclined you can build your own custom PowerShell script with a nice text-based step-by-step UI front end for your users and use the certutil and certreq commands in Windows for the backend. They can assist with the backend processing against the Windows CA and getting the cert onto the key. There are other use friendly ways to self enroll as well which I’ll cover further down below. In the past I have had to install the Yubico YubiKey Smartcard Mini Driver (https://www.yubico.com/support/download/smart-card-drivers-tools/) on the VDA to get the YubiKey to process certs correctly but in this quick example I did not and everything works great as-is without the middleware software using the Windows native smartcard cryptographic service provider (CSP) modules. It’s usually a pretty good idea to have the smart card vendor’s middleware installed on your VDAs though to avoid any unforeseen issues.
- Now use the Citrix Virtual Apps and Desktop Service to publish YubiKey PIV Manager to your users.
- And this is how it will look to your users in their Citrix Workspace. You have now just basically created a smart card management system (SCMS) capable of doing remote onboarding using Citrix. 🙂
- Have the users launch the YubiKey PIV Manager. In my example screenshots below I have published the entire desktop of the Server 2019 VDA and launched that just to illustrate that I’m doing everything over Citrix HDX. Just the published app alone would look like it was locally installed on my Windows 10 laptop in screenshots and I want to make sure you understand it’s all happening remote from Server 2019 over HDX. For a general purpose SCMS available to your employees, contractors, and vendors it may be better just to publish the YubiKey PIV Manager app as I did above and lockdown via Citrix Workspace Environment Manager (WEM) Service in Citrix Cloud to manage Windows AppLocker rules so the entire Windows shell is not exposed. It’s always a good security practice to offer the least amount of attack surface as possible. This goes for all virtual desktops and virtual apps in general, always lock down these environments to prevent any processes (even powerful built-in Windows tools) from being run unless you explicitly allow them to. This prevents attackers from breaking out of the virtual desktop and perform lateral movement attacks across your network. The process management and privilege elevation capability of WEM can help you with this without creating an inflexible overly locked down/poor user experience for the users. The YubiKey inserted into my laptop is lighting up as the YubiKey PIV Manager in the VDI session is reading it. As you can see I have one certificate on it already:
- Now you can have the user generate a new certificate. Please ensure that your CA has a working smartcard template on it already. In my example I created this “YubiKey” one based on the Smartcard User template. Here are some great instructions to create one by Marci Tenpas: https://pivkey.zendesk.com/hc/en-us/articles/115002505111-Setting-up-a-Smart-Card-Template-for-Self-Enrollment-Server-2012-R2-2016-
- Back in the YubiKey PIV Manager, I just went ahead and deleted the cert I had on there just to show you how it would look to a new user with a new YubiKey. Have the user click Certificates:
- Have the user click Generate new key:
- Now we are going to request a new certificate from your Windows CA to write into slot 9A of the YubiKey. This is the slot that holds certificates and depending on your model of YubiKey can hold a varying amount of certificates. Click on “Request a certificate from a Windows CA” and type in the certificate template name exactly as you created it on your Windows Certificate Authority server. Case does matter or it will error out. Make sure it is exact. For the subject it will automatically have populated the signed-in users user ID. Once done hit OK.
- Now have the user enter a PIN. I had already create a PIN earlier and you user would be prompted to create one if they haven’t already. This PIN is used for certificates only and can be different from the PIN they use for FIDO2 logins:
- Now the YubiKey plugged into your laptop will suddenly light up as YubiKey PIV Manager begins the process to contact your CA and create the certificate:
- YubiKey PIV Manager will invoke certreq and the user can now select the CA servers that you have the YubiKey template published on. In my example I have published on my 02 CA server so will select that. Again I want to point out that all this is happening inside my Citrix virtual desktop session on my published Server 2019 desktop that is remote in the same datacenter/cloud IaaS region as my Windows CA. My laptop and YubiKey can be hundreds of miles away from them and it will work just like this:
- And it’s done. YubiKey PIV Manager has installed the private key and certificate onto the YubiKey that is plugged into your laptop potentially hundreds of miles away from your datacenter that your CA is located in. Congratulations! You just created a zero cost smart card management system (SCMS) using Citrix! 🙂
- Once you hit OK it will confirm the details of the certificate. You can just go ahead and and close out of YubiKey PIV Manager at this point. If you have published just the YubiKey PIV Manager app closing PIV Manager will end the remote session. Nice and easy for your users.
- From here, we need to talk about what you should encourage your users to do with their new certificate powered YubiKey. I would highly encourage you to use Azure AD, Okta, or any modern identity provider to use FIDO2 with your Citrix Workspace. Citrix Workspace has one click integration with OpenID Connect (OIDC) based Azure AD, Okta, as well as other SAML 2.0 providers you may be using that can support FIDO2:
- Added bonus, you can also publish YubiKey Manager to your users and allow them to use that over HDX as well. Here I have published my entire Server 2019 desktop again as an example just to prove to you I’m over an HDX session and performing both read and write operations on my YubiKey over the smartcard virtual channel. You can delete the certificates, delete the private key, generate new self signed or CSR based ones, set a new PIN, etc. all over HDX just fine. You can see here as soon as you open it the YubiKey will light up and be detected as the model, firmware, serial number are read and populated. Click Applications and select PIV to manage x.509 certificates:
- You can see the 1 certificate from before is visible, click Configure Certificates:
- It will read Slot 9a on your YubiKey and show details on the cert in the Citrix session. You can perform write operations to create self-signed certs, CSR based certs, set a PIN, etc. here if you like but only the older YubiKey PIV Manager we covered above will talk directly to your Windows CA:
- If you don’t want to use YubiKey PIV Manager or write scripts another way to test things is directly with your Windows CA. Neither are user friendly so should really only be used for your own testing. Go to http:///certsrv and follow the prompts with your elevated account. Or you can use an MMC with the Certificates snap-in as well from any domain-joined system. HID documents both processes on their website well: https://docs.hidglobal.com/crescendo-tools/MiniDriver/issue_smartcard.htm .
- For a more user-friendly self-service approach, Yubico has a really detailed guide on setting up a certificate auto-enrollment group policy: https://support.yubico.com/hc/en-us/articles/360015668979-Setting-up-Smart-Card-Login-for-User-Self-Enrollment. You can point a GPO like this at your VDAs and allow self-enrollment via a virtual desktop which can be a much more user-friendly experience. The users will get a notification prompt like this in the bottom right system tray upon logon to begin the cert enrollment process:
If the user ignores it then it will just prompt them again 8 hours later upon their next login so will work fine for both non-persistent and persistent virtual desktop environments. This would be an ideal experience for employees who you want to give a full virtual desktop to though it may not be best in other remote user scenarios. For example, if you are only wanting to expose just a single secure virtual app to let’s say 3rd party contractors or vendors. In this scenario you may not want to give them a full-blown desktop so publishing a single app or script may be a better approach. Ensure you lock down the session to prevent breakout as described earlier and put these VDAs on a different network segment. Hardening and network segmentation is very important as access control architecture is usually classified as a control plane (what we used to call Tier o) in the Enterprise access model. I would recommend treating these VDAs similarly as an extension of that access control plane and not in a data/workload plane where a VDA may typically sit.
Visibility into the smart card HDX virtual channel
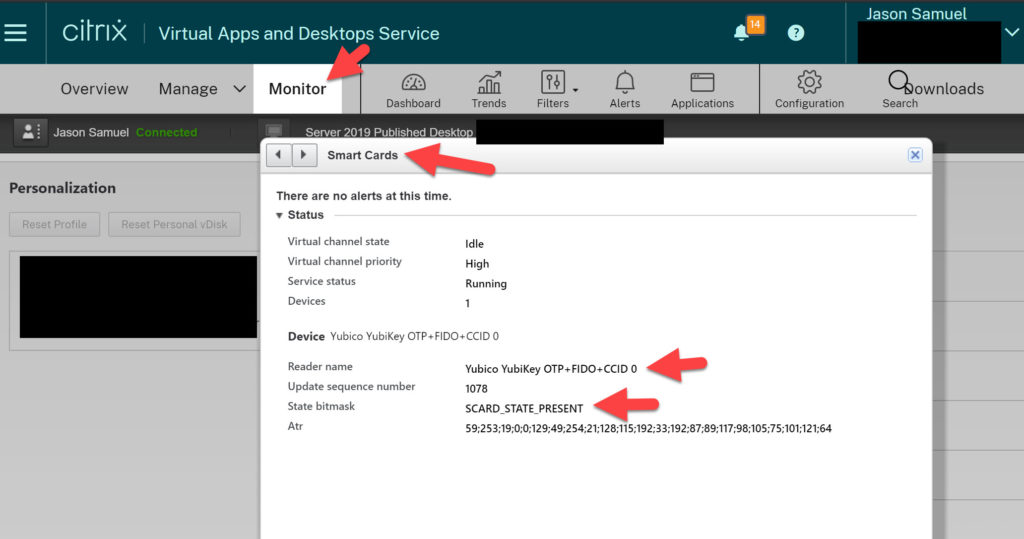
You can use the Citrix HDX Monitor tool (https://cis.citrix.com/hdx/download/) to monitor all the read and write operations happening to the smart card in real-time as you use the YubiKey Manager or YubiKey PIV Manager within your HDX session. Click Smartcard, make sure you are looking at the YubiKey in case you have other x.509 certs on your client system including “virtual smart cards” on a TPM in your laptop for example, and you will see this smart card Calls number continue to rise as you use the YubiKey x.509 cert:
The Citrix Monitor in CVAD Service also allow you to view and report on smart card usage in your environment though it doesn’t pull in all the real-time call metrics since you can imagine how much data that would be:
If you see something other than SCARD_STATE_PRESENT you can always reference the chart here to pinpoint the problem: https://docs.microsoft.com/en-us/windows/win32/api/winscard/ns-winscard-scard_readerstatea
You can also use the “certutil -scinfo” command inside the virtual desktop to enumerate all the certs on the YubiKey as well:
Final Thoughts
I hope this has helped you to understand some of the Citrix capability with smart cards, multi-protocol hardware security keys, and the HDX protocol. They can help accelerate strong authentication initiatives within your organization whether using old or new authentication standards. This combination is extremely powerful to the point you can create your very own SCMS (smart card management system) for your YubiKeys in a pinch to assist with certificate lifecycle for remote employees and contractors! 🙂 Your certificate on your YubiKey can be used for general purpose computing on virtual desktops as well as step-up authentication for admin credentials in separate dedicated jump box/bastion host virtual desktops seamlessly as just one example where this can come in handy. A whole slew of scenarios are possible for better security in your environment practicing fundamental zero trust strategy your organization may be aligning to. If you have any questions please feel free to ask them below.
Jason Samuel is a visionary product leader and trusted advisor with a proven track record of shaping strategy and driving technology innovation. With extensive expertise in enterprise end-user computing, security, cloud, automation, and virtualization technologies, Jason has become a globally recognized authority in the IT industry. His career spans consulting for hundreds of Fortune 500 enterprises across diverse business sectors worldwide, delivering cutting-edge digital solutions from Citrix, Microsoft, VMware, Amazon, Google, and NVIDIA that seamlessly balance security with exceptional user experiences.
Jason’s leadership is amplified by his dedication to knowledge-sharing as an author, speaker, podcaster, and mentor within the global IT and technology community. Recognized with numerous prestigious awards, Jason’s contributions underscore his commitment to advancing technology and empowering organizations to achieve transformative results. Follow him on LinkedIn.

Miguel Rodriguez
November 17, 2021 at 5:08 PM
Hi Jason, how about using smart card to authenticate to workspace or a Citrix client (to the virtual session itself)?
Jason Samuel
November 17, 2021 at 5:51 PM
Yes Citrix has supported certificate based authentication and in-session certificate usage for many years. A common example many enterprises use is setting the Workspace’s identity provider as AD FS with x.509 certs enabled for authentication. Cloud based identity providers that support certificate based authentication would also work. Smartcard redirection for in-session usage is by default on and automatic over the dedicated Smartcard HDX virtual channel (https://docs.citrix.com/en-us/citrix-virtual-apps-desktops/secure/smart-cards.html).
Miguel Rodriguez
January 26, 2022 at 5:26 PM
Hi Jason, to perform enrollment as you described, using the Windows enrollment notifications, is it necessary to install YubiKey mini drivers on the client machine, the VDA server and also on the actual virtual desktop? Without the YubiKey minidriver, as in your example, using the Windows notifications we get an error saying the smart card is “read only”. Is it possible that the smart card HDX channel is only for read only operations (and hence not for certificate enrollment). Can you please confirm?