I was recently working on a setup where I had 2 Azure resource groups and could not get the virtual networks (VNets) to peer between them. I had Azure AD Domain Services in one resource group and a bunch of session host servers in another resource group. The portal kept throwing this error message when attempting to create a peering:
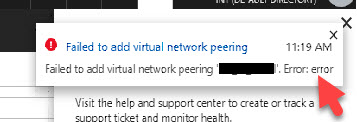
Failed to add virtual network peering
Failed to add virtual network peering ‘name of peering’. Error: error
Not very helpful right? If you see a nondescript error message like this while attempting to peer you can get around the issue using Azure PowerShell. PowerShell also gives you more descriptive error messages which can be clues to help you troubleshoot what’s wrong.
1. First make sure to have Azure PowerShell installed locally or on a jump box. It is a set of cmdlets for PowerShell that will help you manage Azure ARM resources. You can read more on it here: https://docs.microsoft.com/en-us/powershell/azure/overview.
Windows 10 comes with PowerShell already so just open up an elevated PowerShell window and type:
Install-Module AzureRM -AllowClobber
It will tell you:
You are installing the modules from an untrusted repository. If you trust this repository, change
its InstallationPolicy value by running the Set-PSRepository cmdlet.
Are you sure you want to install the modules from 'PSGallery'?
Just press “A” for Yes to All. Now load the AzureRM module for Resource Manager remote management by typing in:
Import-Module AzureRM
Now you can type in:
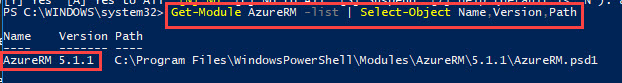
Get-Module AzureRM -list | Select-Object Name,Version,Path
and it will output the Azure PowerShell version installed like this:
I also like to manage Azure AD so I usually also do:
Install-Module AzureAD
Import-Module AzureAD
2. Now log into your Azure subscription from PowerShell. Type:
Login-AzureRmAccount
and a login box will popup. Just follow the prompts. Then PowerShell will show you the account you are logged in with:

3. Now for the VNet peering. You need to create 2 variables to store your VNet info in. My vnet2 is where my Azure ADDS VNet is in this example. My resource group is also specified here at the end:
$vnet2 = Get-AzureRmVirtualNetwork -Name Azure-AD-DS-vnet -ResourceGroupName RG_Azure_AD_Domain_Services
now do the same for where you other VNet is. This is where my session hosts are in this example:
$vnet1 = Get-AzureRmVirtualNetwork -Name OtherRG-tenant-01-vnet -ResourceGroupName OtherRG-tenant-01
and it should look something like this as you type them in:
![]()
4. Now type the following to create your first peer. Pro tip, just press tab after the cmdlet and it will automatically add each switch as you go, no need to even type the first letter of the switch:
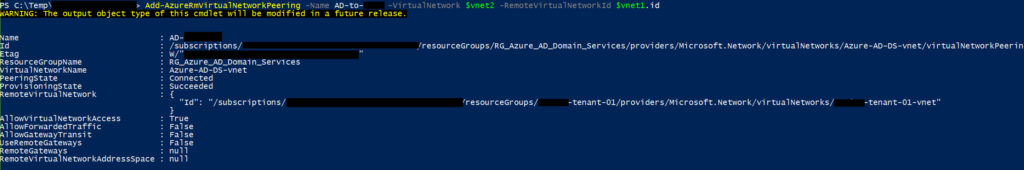
Add-AzureRmVirtualNetworkPeering -Name AD-to-OtherRG -VirtualNetwork $vnet2 -RemoteVirtualNetworkId $vnet1.id
Then do it again but the other way so you have 2 way communication:
Add-AzureRmVirtualNetworkPeering -Name OtherRG-to-AD -VirtualNetwork $vnet1 -RemoteVirtualNetworkId $vnet2.id
and you’re done! It should look something like this as you create each peer:
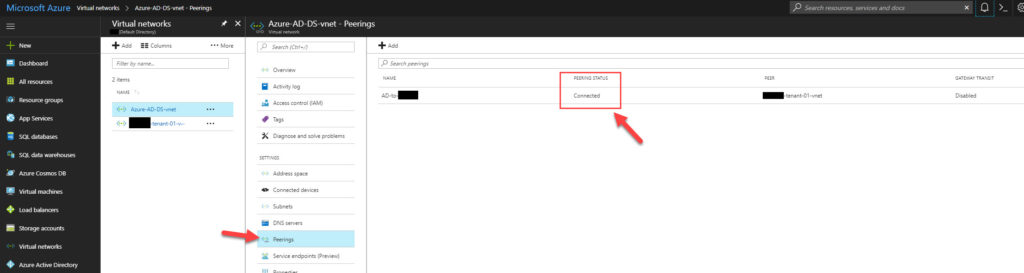
and your Azure Portal should say it’s Connected under Peering Status:
Hope this helps! Please leave a comment below if you have any questions.
Jason Samuel is a visionary product leader and trusted advisor with a proven track record of shaping strategy and driving technology innovation. With extensive expertise in enterprise end-user computing, security, cloud, automation, and virtualization technologies, Jason has become a globally recognized authority in the IT industry. His career spans consulting for hundreds of Fortune 500 enterprises across diverse business sectors worldwide, delivering cutting-edge digital solutions from Citrix, Microsoft, VMware, Amazon, Google, and NVIDIA that seamlessly balance security with exceptional user experiences.
Jason’s leadership is amplified by his dedication to knowledge-sharing as an author, speaker, podcaster, and mentor within the global IT and technology community. Recognized with numerous prestigious awards, Jason’s contributions underscore his commitment to advancing technology and empowering organizations to achieve transformative results. Follow him on LinkedIn.
Disclaimer: Views expressed here are his own and do not reflect the views of his employer, past or present, or any organizations he is affiliated with. Content is for informational or personal purposes only.




Thanks a lot for this article!
Hi Jason, I read your blogs and its quite good and eye opening for me. I need an input from…
I'm with Richard Powell and Andreas Mariotti. Things work if I do it the USB redirection way, but not with…
We see this behaviour with 2203 CU2 VDAs and while being happy, that there is at leasy an workaround without…
Saved my butt without playing around over dozens attempts to get that certificate installed! Thank you! <3 Chris